A new Iranian state-sponsored hacking group known as APT42 has been discovered using a custom Android malware to spy on targets of interest.
The cybersecurity firm has collected enough evidence to determine that APT42 is a state-sponsored threat actor who engages in cyberespionage against individuals and organizations of particular interest to the Iranian government.
APT42's first signs of activity date back to seven years ago and revolve around lengthy spear-phishing campaigns that targeted government officials, policymakers, journalists, academics across the globe, and Iranian dissidents.
The hackers' goal is to steal account credentials. However, in many cases, they also deploy a custom Android malware strain capable of tracking victims, accessing the device's storage, and extracting communication data.
Campaigns and targets
According to Mandiant, who discovered the activities of the new hacking group, APT42 has conducted at least 30 operations in 14 countries since 2015. However, this is likely only a small part that surfaced due to operation security mistakes that allowed them to be tracked.
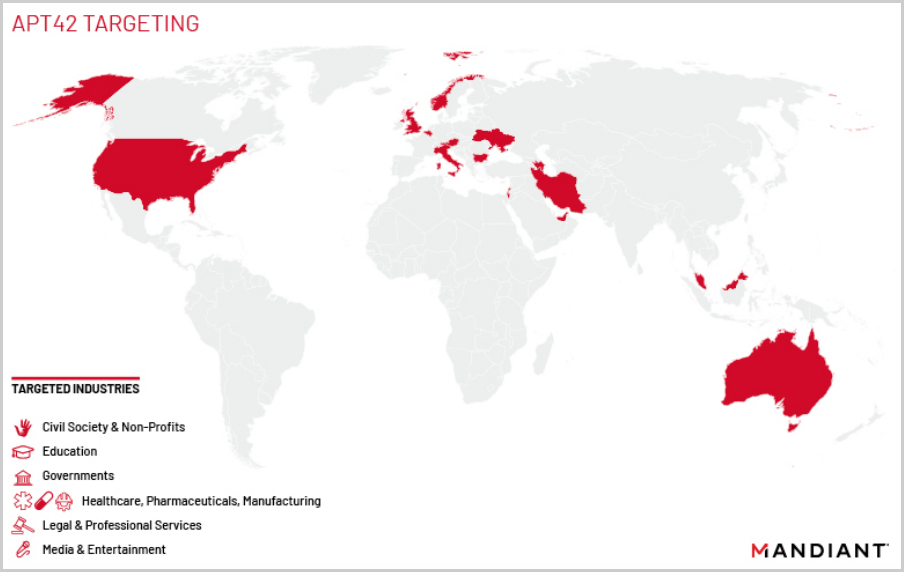
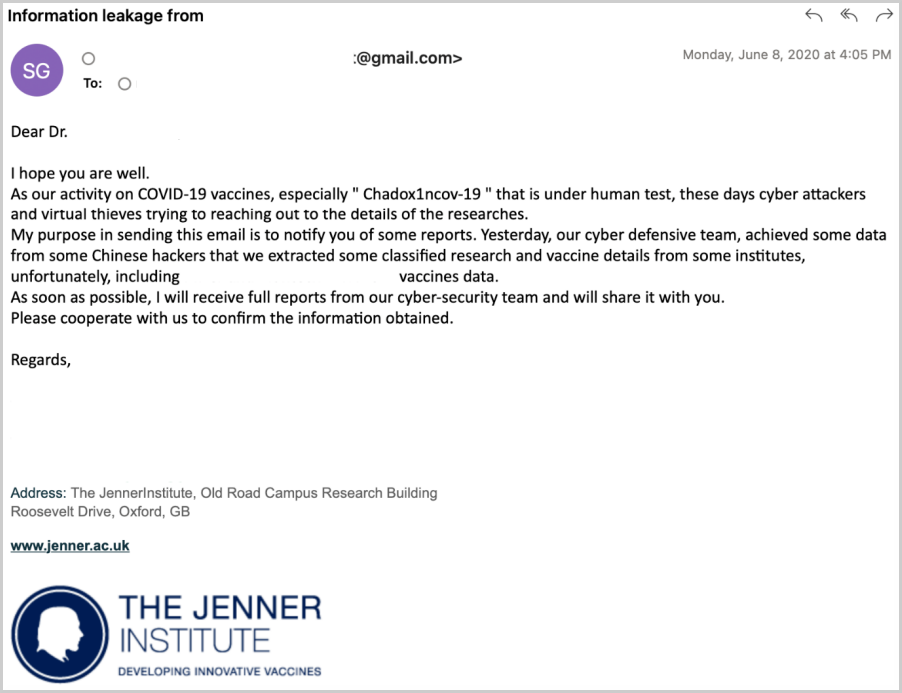
The group switched targets multiple times to match changing intelligence-collection interests. For example, in 2020, APT42 used phishing emails impersonating an Oxford university vaccinologist to target foreign pharmaceuticals.
In 2021, APT42 used compromised email addresses from U.S. media organizations to target victims with fake interview requests, engaging with them for 37 days before striking with a credential harvesting page.

More recently, in February 2022, the hackers impersonated a British news agency to target political science professors in Belgium and the United Arab Emirates.
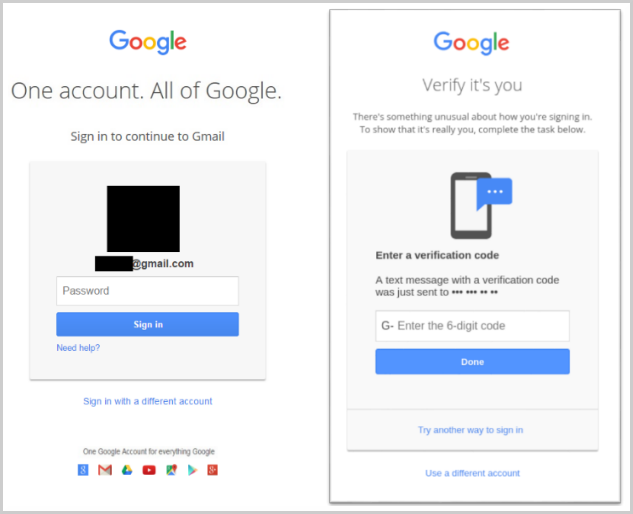
In most cases, the hackers aimed at credential harvesting by directing their victims to phishing pages made to appear as legitimate login portals.
They either do this by sending shortened links or a PDF attachment containing buttons leading to credential harvesting pages also capable of intercepting MFA codes.
Android malware
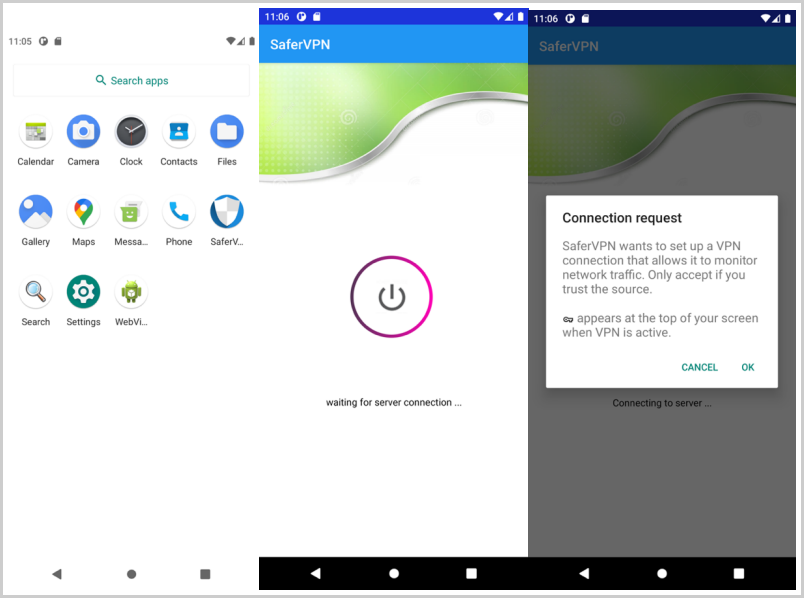
The mobile malware strain used in APT42 campaigns helps the threat actor track its most high-interest targets closely, exfiltrating phone calls, SMS inboxes, and room audio recordings daily.
Mandiant says the Android spyware is primarily spread to Iranian targets via SMS texts containing links to a messaging or VPN app that can help bypass government-imposed restrictions.
"The use of Android malware to target individuals of interest to the Iranian government provides APT42 with a productive method of obtaining sensitive information on targets, including movement, contacts, and personal information," comments Mandiant in the technical report.
"The group's proven ability to record phone calls, activate the microphone and record the audio, exfiltrate images and take pictures on command, read SMS messages, and track the victim's GPS location in real-time poses a real-world risk to individual victims of this campaign."
However, Mandiant also reports discovering landing pages for downloading IM apps in Arabic, so threat actors might have deployed the Android malware outside Iran too.
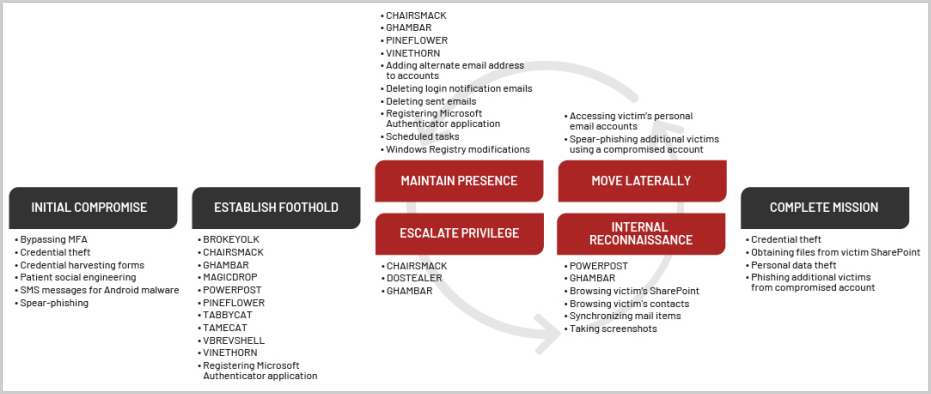
APT42 uses a rich set of lightweight custom malware on Windows systems to establish a foothold and steal credentials that will enable them to escalate privileges and perform reconnaissance on the network.
For lateral movement, the hackers send phishing emails to colleagues of the compromised user. At the same time, presence in newly breached systems is secured by adding scheduled tasks and new Windows registry keys.
Links to ransomware
Mandiant highlights a link between APT42's TTPs and ransomware activity using BitLocker, reported in November 2021 by Microsoft.
"In one observed campaign, PHOSPHORUS targeted the Fortinet FortiOS SSL VPN and unpatched on-premises Exchange Servers globally with the intent of deploying ransomware on vulnerable networks," described the Microsoft report.
While Microsoft named the threat cluster 'Phosphorus' in its report, Mandiant now says there's enough technical and OSINT evidence to link the attacks to APT42, together with APT35.
Finally, Mandiant has assessed with moderate confidence that APT42 and APT35 are both handles of the IRGC (Islamic Revolutionary Guard Corps), which the U.S. designates as a terrorist organization.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.