A new Android malware named 'Hook' is being sold by cybercriminals, boasting it can remotely take over mobile devices in real-time using VNC (virtual network computing).
The new malware is promoted by the creator of Ermac, an Android banking trojan selling for $5,000/month that helps threat actors steal credentials from over 467 banking and crypto apps via overlaid login pages.
While the author of Hook claims the new malware was written from scratch, and despite having several additional features compared to Ermac, researchers at ThreatFabric dispute these claims and report seeing extensive code overlaps between the two families.
ThreatFabric explains that Hook contains most of Ermac's code base, so it's still a banking trojan. At the same time, it includes several unnecessary parts found in the older strain that indicate it re-used code in bulk.
A more dangerous Android malware
Despite its origin, Hook is an evolution of Ermac, offering an extensive set of capabilities that make it a more dangerous threat to Android users.
One new feature of Hook compared to Ermac is the introduction of WebSocket communication that comes in addition to HTTP traffic used exclusively by Ermac. The network traffic is still encrypted using an AES-256-CBC hardcoded key.
The highlight addition, however, is the 'VNC' module that gives threat actors the capability to interact with the user interface of the compromised device in real-time.
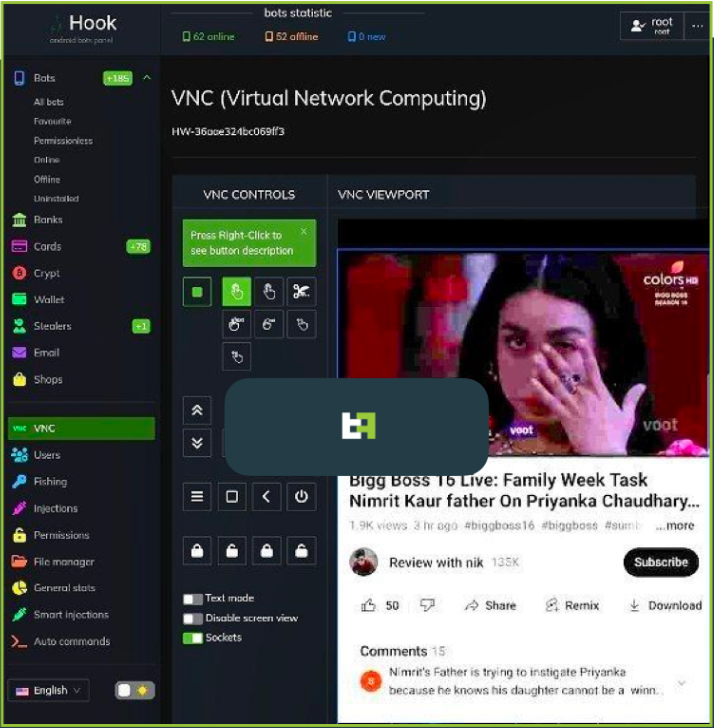
Hook's author promoting the new VNC system (ThreatFabric)
This new system enables Hook's operators to perform any action on the device, from PII exfiltration to monetary transactions.
"With this feature, Hook joins the ranks of malware families that are able to perform full DTO, and complete a full fraud chain, from PII exfiltration to transaction, with all the intermediate steps, without the need of additional channels," warns ThreatFabric.
"This kind of operation is much harder to detect by fraud scoring engines, and is the main selling point for Android bankers."
The catch is that Hook's VNC requires Accessibility Service access to work, which might be hard to get on devices running Android 11 or later.
Hook's new (in addition to Ermac's) commands can perform the following actions:
- Start/stop RAT
- Perform a specific swipe gesture
- Take a screenshot
- Simulate click at specific text item
- Simulate a key press (HOME/BACK/RECENTS/LOCK/POWERDIALOG)
- Unlock the device
- Scroll up/down
- Simulate a long press event
- Simulate click at a specific coordinate
- Set clipboard value to a UI element with specific coordinates value
- Simulate click on a UI element with a specific text value
- Set a UI element value to a specific text
Apart from the above, a "File Manager" command turns the malware into a file manager, allowing the threat actors to get a list of all files stored in the device and download specific files of their choice.
Another notable command that ThreatFabric found concerns WhatsApp, allowing Hook to log all messages in the popular IM app and even allowing the operators to send messages via the victim's account.
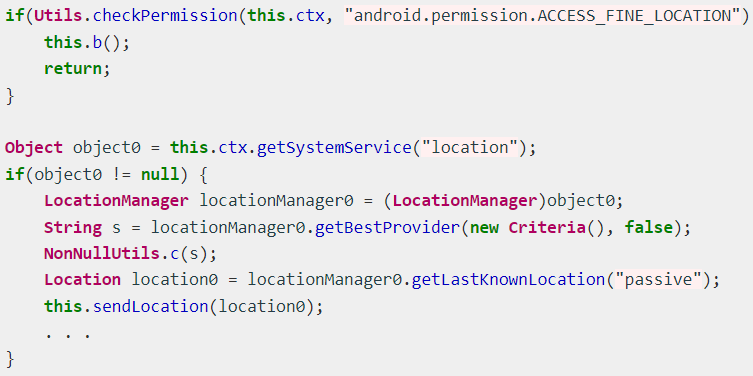
Finally, a new geolocation tracking system enables Hook operators to track the victim's precise position by abusing the "Access Fine Location" permission.
Worldwide targeting
Hook's target banking applications impact users in the United States, Spain, Australia, Poland, Canada, Turkey, the UK, France, Italy, and Portugal.
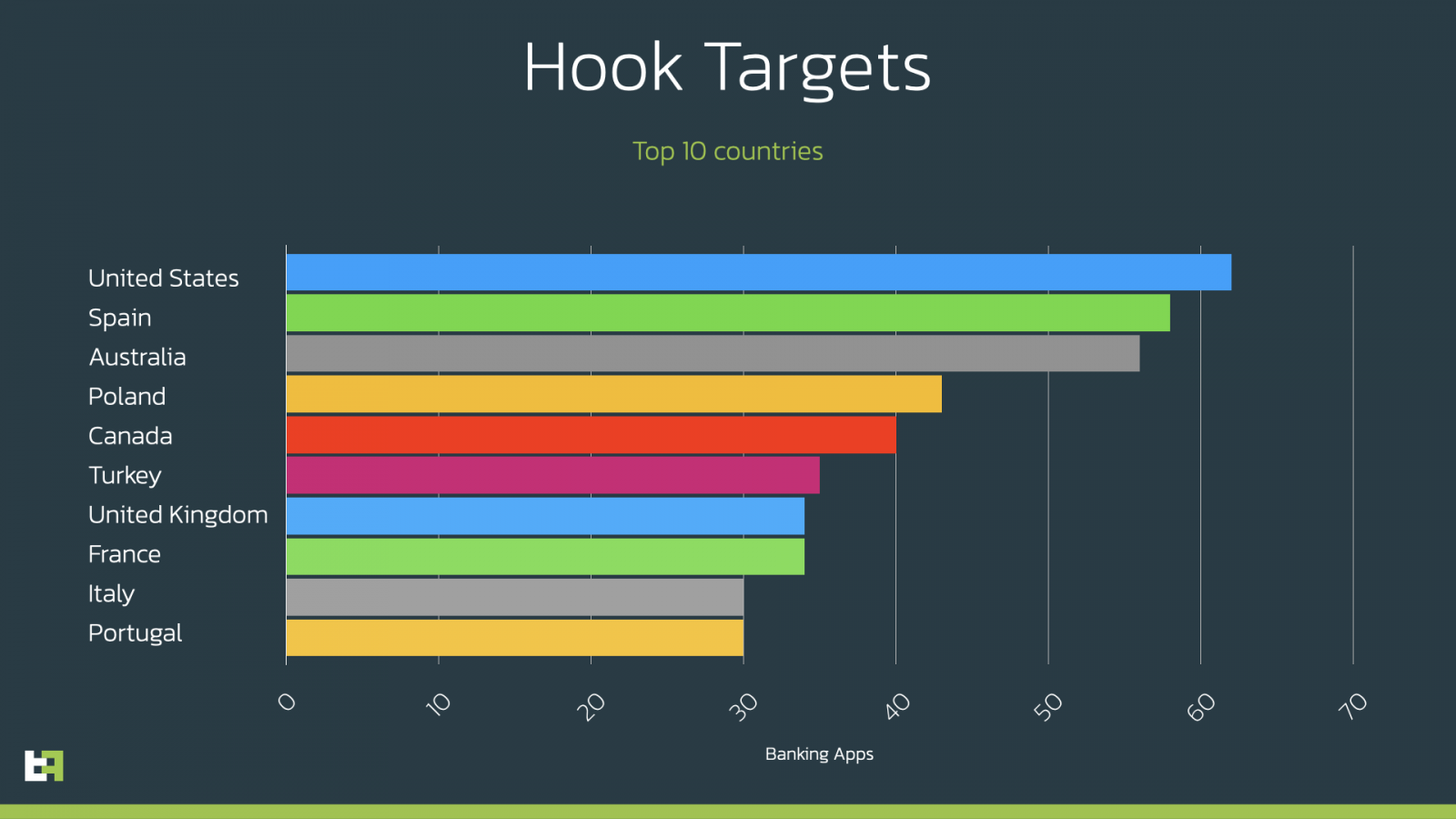
Number of banking apps per country targeted by Hook (ThreatFabric)
However, it is essential to note that Hook's broad targeting scope covers the entire world. ThreatFabric listed all the apps Hook targets in the report's appendix for those interested.
At this time, Hook is distributed as a Google Chrome APK under the package names "com.lojibiwawajinu.guna," "com.damariwonomiwi.docebi," "com.damariwonomiwi.docebi," and "com.yecomevusaso.pisifo," but of course, this could change at any moment.
To avoid becoming infected with Android malware, you should only install apps from the Google Play Store or those provided by your employer.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.