A previously unknown Chinese APT (advanced persistent threat) hacking group dubbed 'Earth Longzhi' targets organizations in East Asia, Southeast Asia, and Ukraine.
The threat actors have been active since at least 2020, using custom versions of Cobalt Strike loaders to plant persistent backdoors on victims' systems.
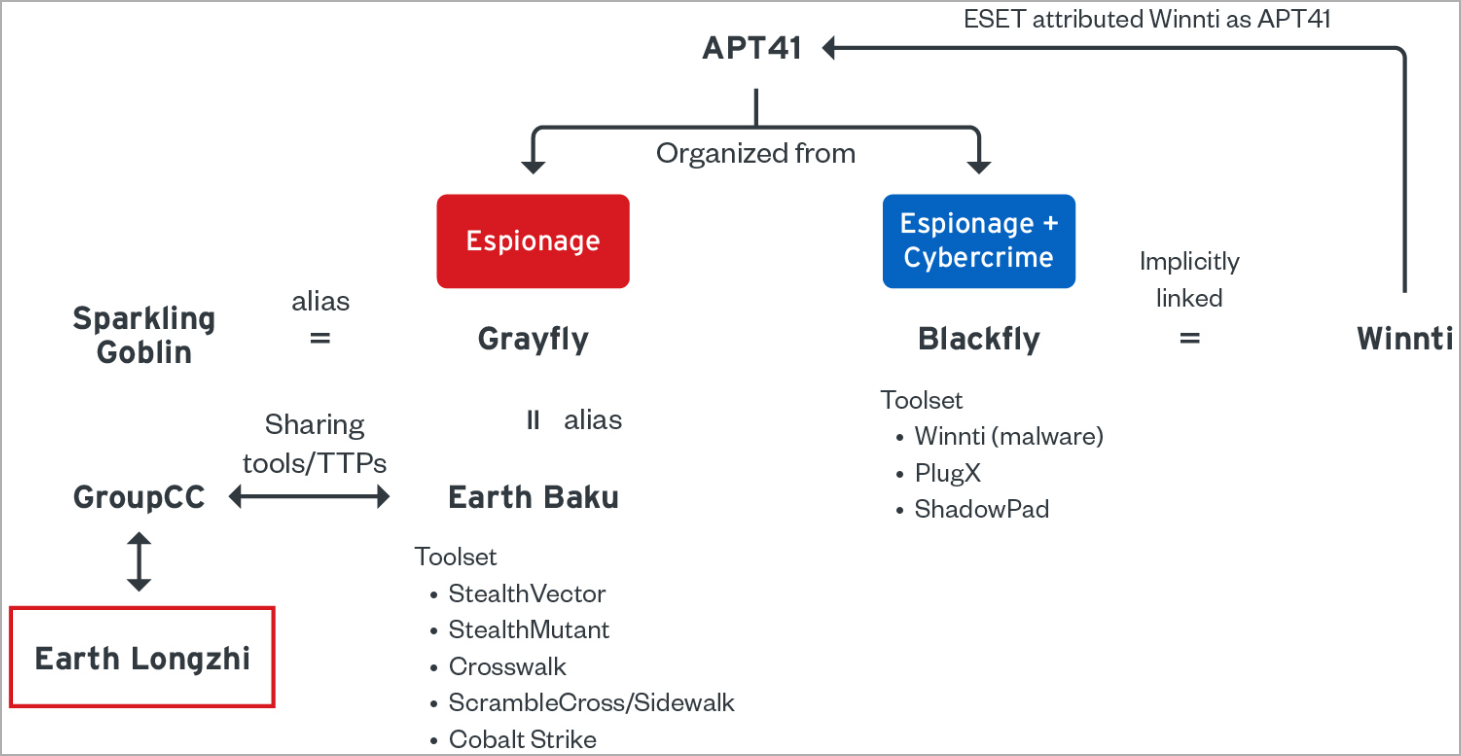
According to a new Trend Micro report, Earth Longzhi has similar TTP (techniques, tactics, and procedures) as 'Earth Baku,' both considered subgroups of the state-backed hacking group tracked as APT41.
Earth Longzhi's older campaign
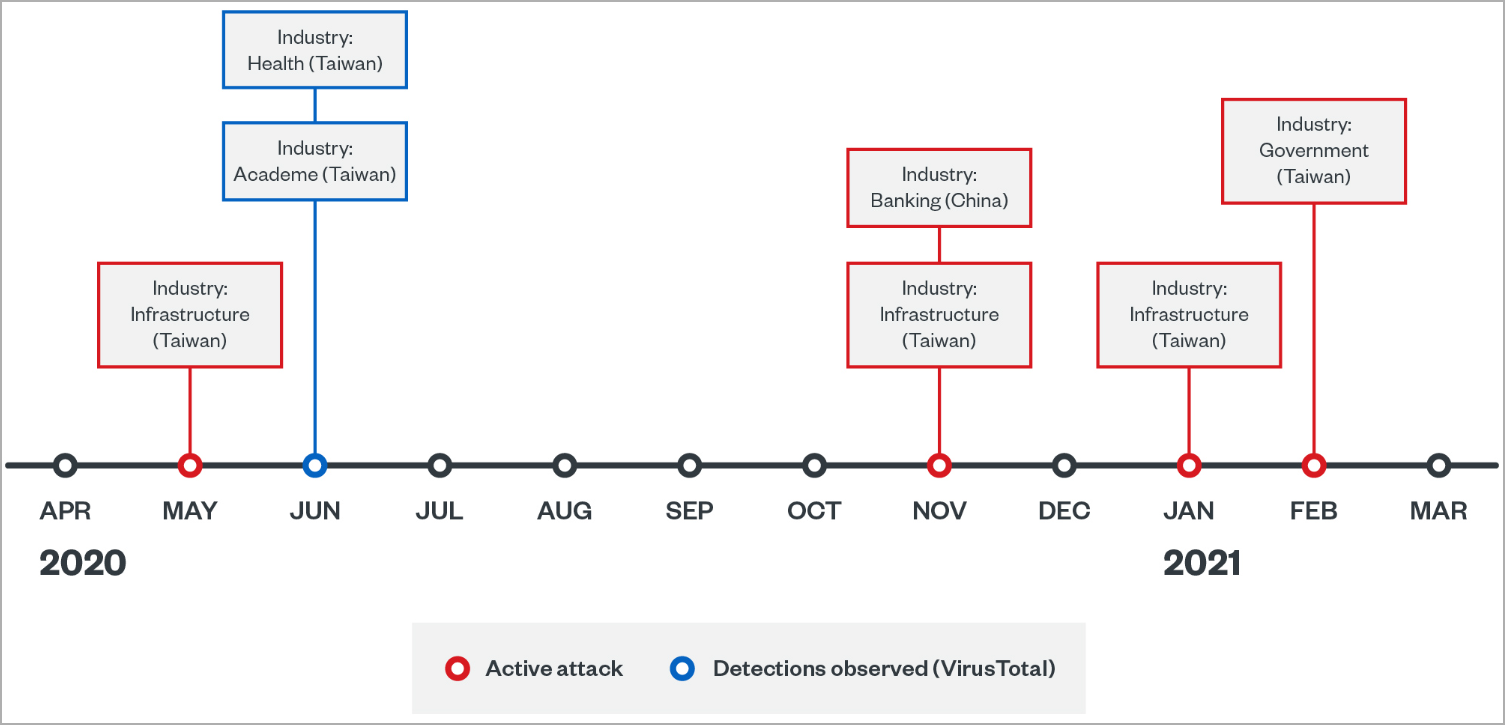
Trend Micro's report illustrates two campaigns conducted by Earth Longzhi, with the first occurring between May 2020 and February 2021.
During that time, the hackers attacked several infrastructure companies in Taiwan, a bank in China, and a government organization in Taiwan.
Timeline of first campaign (Trend Micro)
In this campaign, the hackers used the custom Cobalt Strike loader 'Symatic,' which features a sophisticated anti-detection system including the following functions:
- Remove API hooks from 'ntdll.dll,' get raw file content, and replace the in-memory ntdll image with a copy not monitored by security tools.
- Spawn a new process for process injection and masquerade the parent process to obfuscate the chain.
- Inject a decrypted payload into the newly created process.
For its primary operations, Earth Longzhi used an all-in-one hacking tool that combined various publicly available tools under a single package.
This tool can open a Socks5 proxy, perform password scans on MS SQL servers, disable Windows file protection, modify file timestamps, scan ports, launch new processes, perform RID spoofing, enumerate drives, and execute commands with 'SQLExecDirect.'
2022 campaign
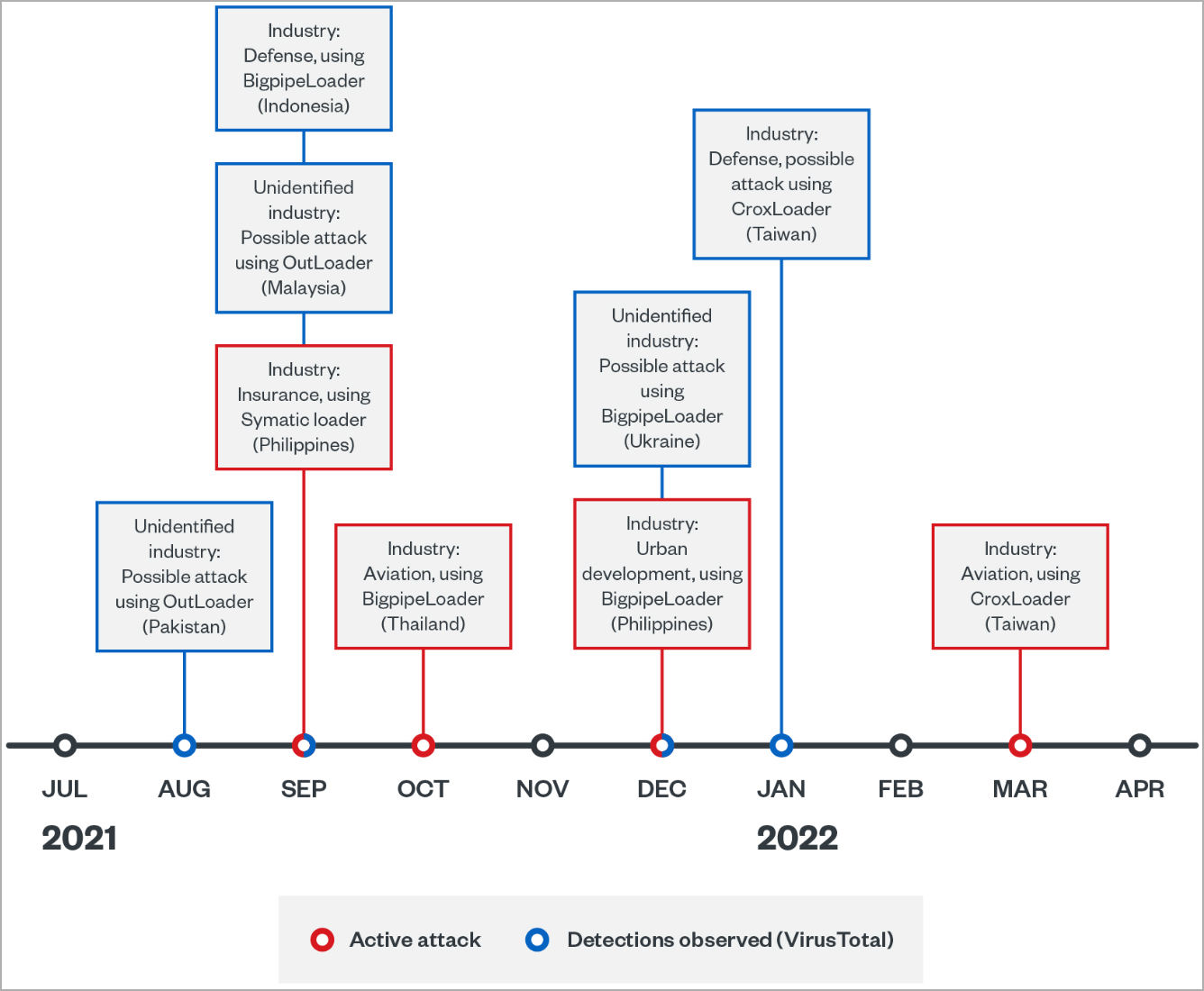
The second campaign observed by Trend Micro lasted from August 2021 until June 2022, targeting insurance and urban development firms in the Philippines and aviation firms in Thailand and Taiwan.
Timeline of the second campaign (Trend Micro)
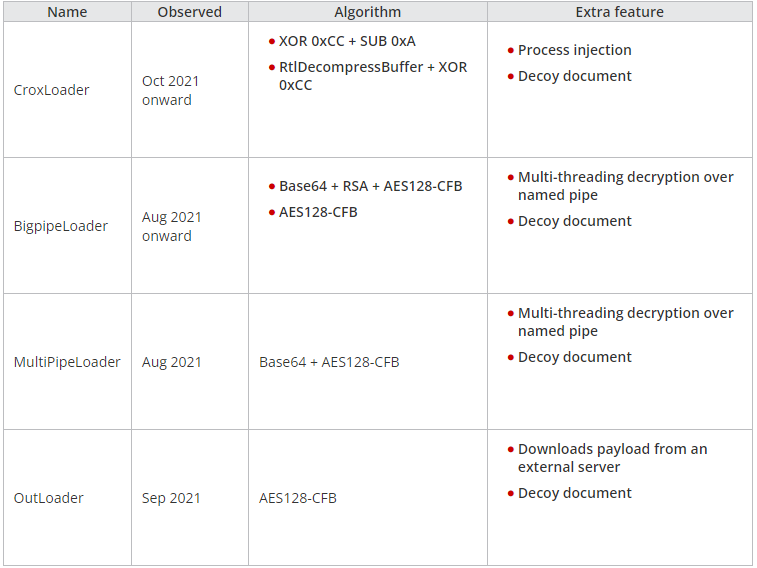
In these more recent attacks, Earth Longzhi deployed a new set of custom Cobalt Strike loaders that used different decryption algorithms and additional features for performance (multi-threading) and effectiveness (decoy documents).
Different loaders used in the recent campaign (Trend Micro)
The injection of the Cobalt Strike payload into a newly created process running in memory remains the same as in Symatic, never touching the disk to avoid risking detection.
One variant of the BigpipeLoader follows a very different payload loading chain, using DLL sideloading (WTSAPI32.dll) on a legitimate app (wusa.exe) to run the loader (chrome.inf) and inject Cobalt Strike on memory.
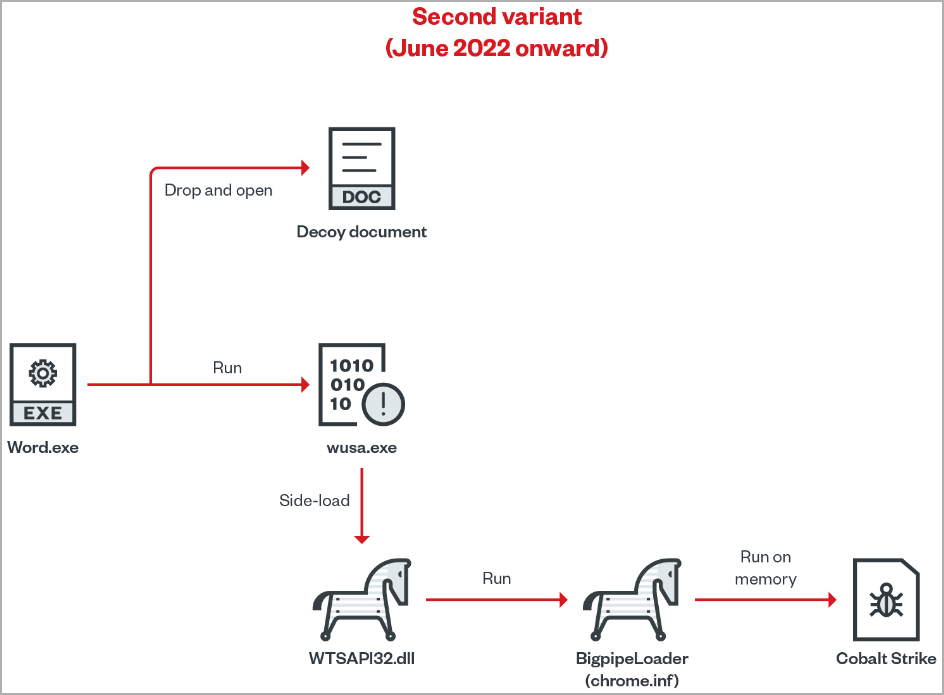
Latest loader variant used in Earth Longzhi attacks (Trend Micro)
After Cobalt Strike runs on the target, the hackers use a custom version of Mimikatz to steal credentials and use the 'PrintNighmare' and 'PrintSpoofer' exploits for privilege escalation.
To disable security products on the host, Earth Longzhi uses a tool named 'ProcBurner,' which abuses a vulnerable driver (RTCore64.sys) to modify the required kernel objects.
"ProcBurner is designed to terminate specific running processes," explains Trend Micro in the report.
"Simply put, it tries to change the protection of the target process by forcibly patching the access permission in the kernel space using the vulnerable RTCore64.sys."
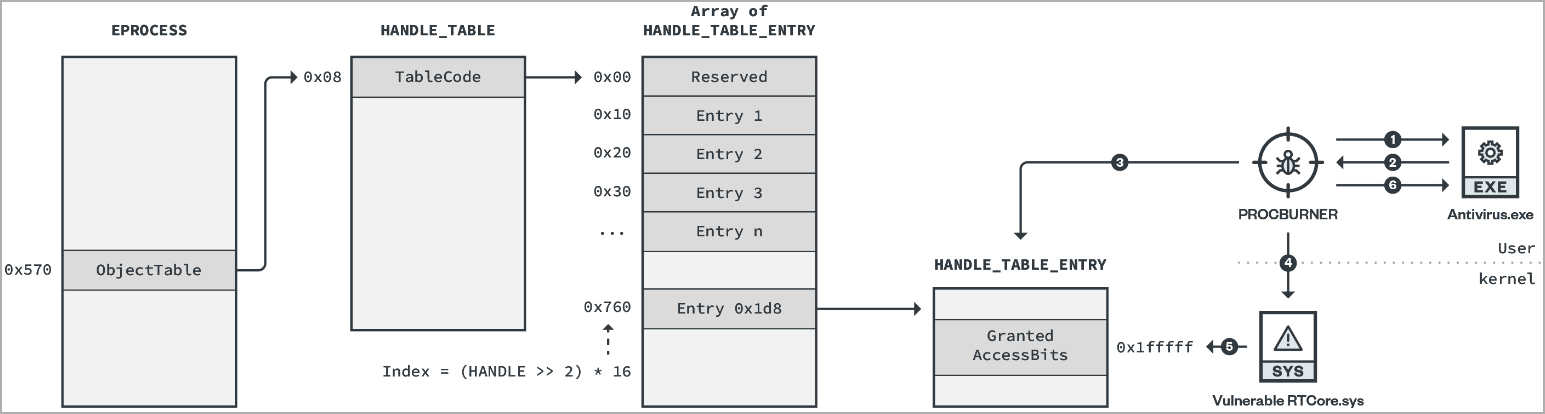
ProcBurner functional diagram (Trend Micro)
Notably, the same MSI Afterburner driver is also used by BlackByte ransomware in Bring Your Own Vulnerable Drive (BYOVD) attacks that abuse it to bypass over a thousand security protections.
ProcBurner first detects the OS, as the kernel patching process changes depending on the version. The tool supports the following releases:
- Windows 7 SP1
- Windows Server 2008 R2 SP1
- Windows 8.1
- Windows Server 2012 R2
- Windows 10 1607, 1809, 20H2, 21H1
- Windows Server 2018 1809
- Windows 11 21H2, 22449, 22523, 22557
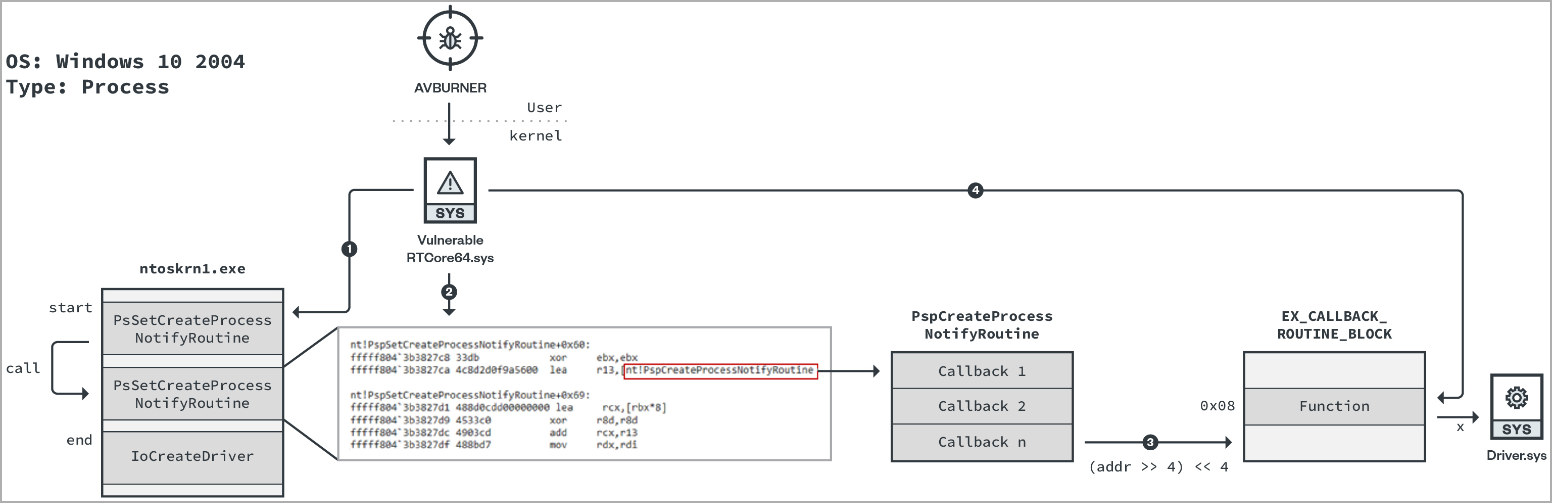
A second protection-negating tool, ' AVBurner,' also abuses the vulnerable driver to unregister security products by removing their kernel callback routine.
Commodity + custom
APT groups increasingly rely on commodity malware and attack frameworks like Cobalt Strike to obscure their trace and make attribution difficult.
However, the sophisticated hackers still develop and use custom tools for stealthy payload loading and to bypass security software.
By following these tactics, Earth Longzhi has managed to stay undetected for at least 2.5 years now, and following this exposure by Trend Micro, they are likely to switch to new tactics.
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.