A new ransomware family called 'GwisinLocker' targets South Korean healthcare, industrial, and pharmaceutical companies with Windows and Linux encryptors, including support for encrypting VMware ESXi servers and virtual machines.
The new malware is the product of a lesser-known threat actor dubbed Gwisin, which means "ghost" in Korean. The actor is of unknown origin but appears to have a good knowledge of the Korean language.
Also, the attacks coincided with Korean public holidays and occurred during early morning hours, so Gwisin has a good grasp of the country's culture and business routines.
Reports about Gwisin and its activities first appeared on South Korean media outlets late last month, when the threat actor compromised large pharmaceutical firms in the country.
On Wednesday, Korean cybersecurity experts at Ahnlab published a report on the Windows encryptor, and yesterday, security researchers at ReversingLabs published their technical analysis of the Linux version.
Targeting Windows and Linux servers
When GwisinLocker encrypts Windows devices, the infection begins with the execution of an MSI installer file, which requires special command line arguments to properly load the embedded DLL that acts as the ransomware encryptor.
Requiring command-line arguments makes it harder for security researchers to analyze the ransomware.
When the proper command-line arguments are provided, the MSI will decrypt and inject its internal DLL (ransomware) into a Windows process to evade AV detection, which is different for each company.
The configuration sometimes includes an argument that sets the ransomware to operate in safe mode. In those cases, it copies itself to a ProgramData subfolder, registers as a service, and then forces a reboot in safe mode.
For the Linux version analyzed by ReversingLabs, the encryptor focuses strongly on encrypting VMware ESXi virtual machines, including two command-line arguments that control how the Linux encryptor will encrypt virtual machines.
The command-line arguments for the GwisinLocker Linxu encryptor are listed below:
Usage: Usage
-h, --help show this help message and exit
Options
-p, --vp= Comma-separated list of paths to encrypt
-m, --vm= Kills VM processes if 1; Stops services and processes if 2
-s, --vs= Seconds to sleep before execution
-z, --sf= Skip encrypting ESXi-related files (those excluded in the configuration)
-d, --sd= Self-delete after completion
-y, --pd= Writes the specified text to a file of the same name
-t, --tb= Enters loop if Unix time is These arguments include the --vm flag, which will execute the following commands to enumerate ESXi virtual machines and shut them down.
esxcli --formatter=csv --format-param=fields=="DisplayName,WorldID" vm process list
esxcli vm process kill --type=force --world-id="[ESXi] Shutting down - %s"To avoid rendering the Linux server unusable, GwisinLocker will exclude the following directories from encryption.
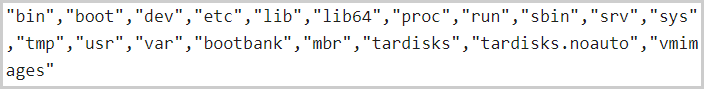
Processes excluded from encryption (ReversingLabs)
Unless the --sf command-line argument is used, the Linux ransomware will also exclude specific VMware ESXi related files (state.tgz, useropts.gz, jumpstrt.gz, etc) to prevent the server from becoming unbootable.
Finally, the ransomware terminates several Linux daemons before initiating encryption to make their data available for the locking process.
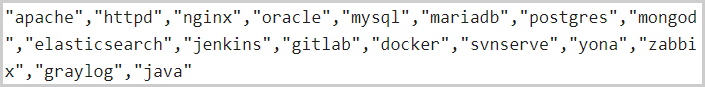
Services killed before encryption (ReversingLabs)
When encrypting files, the encryptor uses AES symmetric-key encryption with SHA256 hashing.
Customized for each victim
Regardless of the operating system targeted in the attack, all encryptors are customized to include the company name in the ransom note and to use a unique extension for encrypted file names.
For one victim known by BleepingComputer, threat actors heavily customized the ransom note to include the specific data that was stolen during the attack, which we redacted in the note below.
The ransom notes are named '!!!_HOW_TO_UNLOCK_[company_name]_FILES_!!!.TXT' and are written in English, with some warning the victim not to contact the South Korean law enforcement agencies or KISA (Korea Internet and Security Agency).
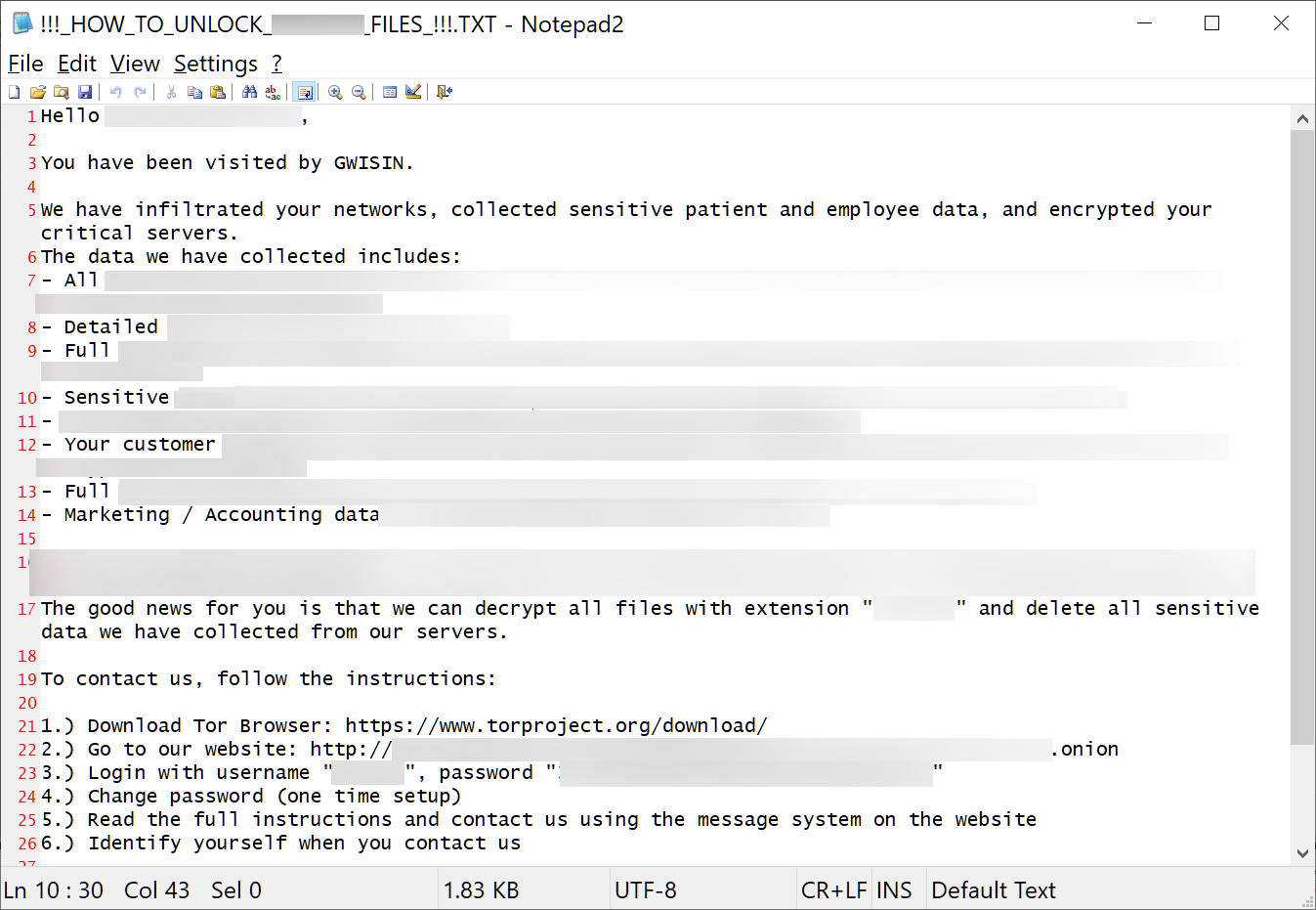
An example GwisinLocker ransom note
Source: BleepingComptuer
Instead, the victims are told to visit an onion address using the Tor browser, log in with the provided credentials, and follow the instructions on paying a ransom and restoring files.
While AhnLab's and ReversingLabs noted that GwisinLocker primarily targets South Korean industrial and pharmaceutical companies, BleepingComputer is aware of a healthcare clinic that was also targeted.
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.