An active extortion scam is targeting website owners and admins worldwide, claiming to have hacked their servers and demanding $2,500 not to leak data.
The attackers (self-dubbed Team Montesano) are sending emails with “Your website, databases and emails has been hacked” subjects.
The emails appear to be non-targeted, with ransom demand recipients from all verticals, including personal bloggers, government agencies, and large corporations.
The scam is so widespread that our own reporter Ax Sharma and Have I Been Breached created Troy Hunt have also received these extortion attempts.
The spam messages warn that the hackers will leak stolen data, damage their reputation, and get the site blacklisted for spam if the targets don’t make a payment of $2,500.
Website reputation extortion email (Ax Sharma)
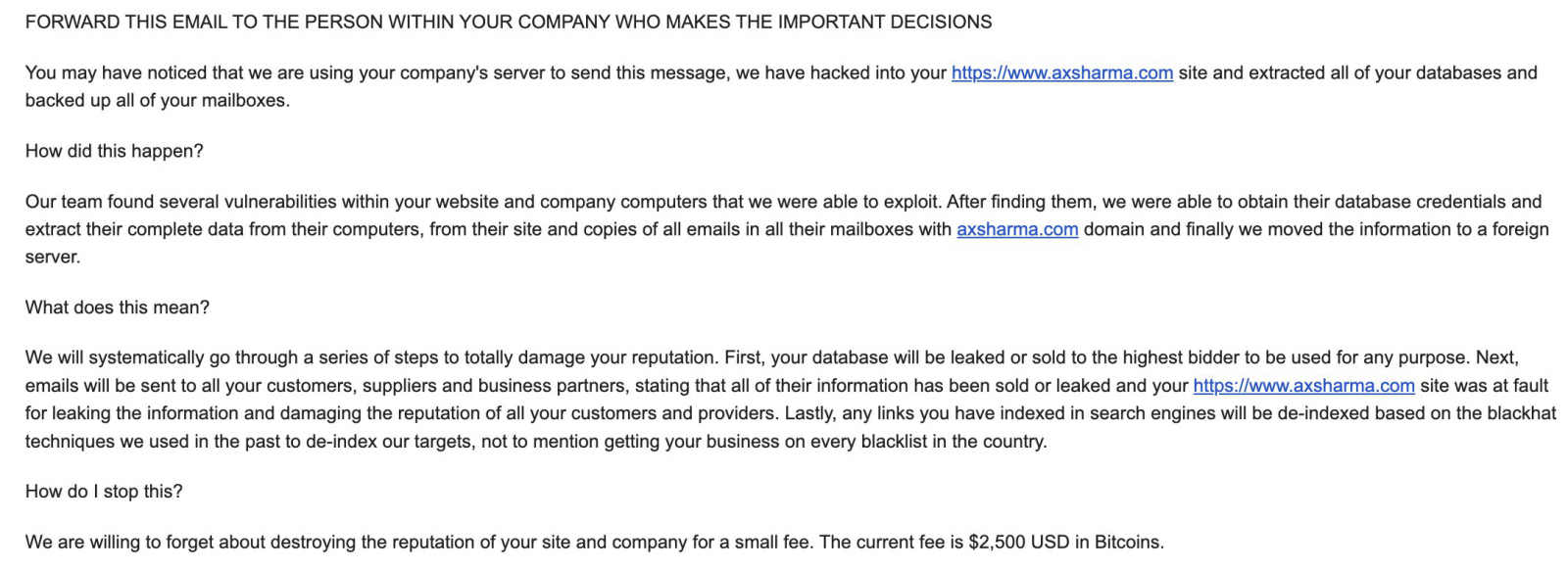
The full extortion message can be read below:
"FORWARD THIS EMAIL TO THE PERSON WITHIN YOUR COMPANY WHO MAKES THE IMPORTANT DECISIONS
You may have noticed that we are using your company's server to send this message, we have hacked into your https://www.***.gov site and extracted all of your databases and backed up all of your mailboxes.
How did this happen?
Our team found several vulnerabilities within your website and company computers that we were able to exploit. After finding them, we were able to obtain their database credentials and extract their complete data from their computers, from their site and copies of all emails in all their mailboxes with ***.gov domain and finally we moved the information to a foreign server.
What does this mean?
We will systematically go through a series of steps to totally damage your reputation. First, your database will be leaked or sold to the highest bidder to be used for any purpose. Next, emails will be sent to all your customers, suppliers and business partners, stating that all of their information has been sold or leaked and your https://***.gov site was at fault for leaking the information and damaging the reputation of all your customers and providers. Lastly, any links you have indexed in search engines will be de-indexed based on the blackhat techniques we used in the past to de-index our targets, not to mention getting your business on every blacklist in the country.
How do I stop this?
We are willing to forget about destroying the reputation of your site and company for a small fee. The current fee is $2,500 USD in Bitcoins.
Send the amount in Bitcoin to the following address:
3Fyjqj5WutzSVJ8DnKrLgZFEAxVz6Pddn7
Once you have made your payment, we will automatically be informed of it. At the precise moment that you have read this message, you have a period of 72 hours to make the payment, or I guarantee that the reputation of your company will be completely destroyed. The proof that we have access and all your data is that this message has been sent using your company's servers.
How do I get Bitcoins?
You can easily buy bitcoins through various websites.
What happens if I don't pay?
If you decide not to pay, we will launch the attack after 72 hours and keep it until you do, there is no countermeasure to this, you will just end up wasting more money trying to find a solution. We will completely destroy your reputation with your customers, your suppliers, your partners, on google and the entire country.
This is not a hoax, do not try to reason or negotiate, we will not read any answers. Once you've paid, we'll stop what we were doing, we'll destroy all data taken from your site, your databases, your mailboxes, and you'll never hear from us again.
Keep in mind that the payment with Bitcoin is anonymous and no one will know that you have complied. The time is running."
From extortion emails seen by BleepingComputer, the threat actors are currently using two bitcoin addresses.
nfortunately, the bitcoin transactions to the wallet 3Fyjqj5WutzSVJ8DnKrLgZFEAxVz6Pddn7 indicate that someone may have paid the extortion demand already.
Even though these emails can be scary to those website owners who receive them, it is important to remember that they are just scams.
They are being mass-emailed to many people and are just trying to scare people into making a payment. Instead, just mark them as spam and delete them.
Also, always search for the Bitcoin address embedded in the blackmail email you receive on the Bitcoin Abuse Database to find any reports of fraudsters actively using them.
Since the summer of 2018, when BleepingComputer started reporting on these scams, threat actors have been behind a wide assortment of email extortion scams.
The list includes scams that pretend to be bomb threats, hitman contracts, CIA investigations, threats of installing ransomware, as well ones containing threats to infect the targets' families with the SARS-CoV-2 virus.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.