A reverse-proxy Phishing-as-a-Service (PaaS) platform called EvilProxy has emerged, promising to steal authentication tokens to bypass multi-factor authentication (MFA) on Apple, Google, Facebook, Microsoft, Twitter, GitHub, GoDaddy, and even PyPI.
The service enables low-skill threat actors who don't know how to set up reverse proxies to steal online accounts that are otherwise well-protected.
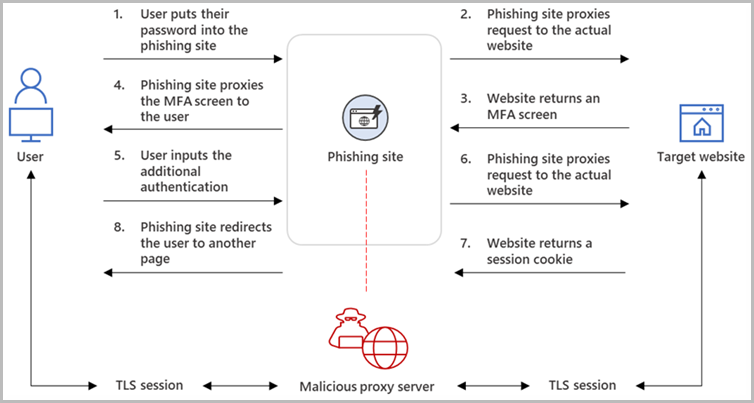
Reverse proxies are servers that sit between the targeted victim and a legitimate authentication endpoint, such as a company's login form. When the victim connects to a phishing page, the reverse proxy displays the legitimate login form, forwards requests, and returns responses from the company's website.
When the victim enters their credentials and MFA to the phishing page, they are forwarded to the actual platform's server, where the user is logged in, and a session cookie is returned.
However, as the threat actor's proxy sits in the middle, it can also steal the session cookie containing the authentication token. The threat actors can then use this authentication cookie to log in to the site as the user, bypassing configured multi-factor authentication protections.
Sophisticated APT groups have been employing reverse proxies for a while now to bypass MFA protections on target accounts, some using their own custom tools while others using more readily-deployable kits like Modlishka, Necrobrowser, and Evilginx2.
The difference between these phishing frameworks and EvilProxy is that the latter is far simpler to deploy, offers detailed instructional videos and tutorials, a user-friendly graphical interface, and a rich selection of cloned phishing pages for popular internet services.
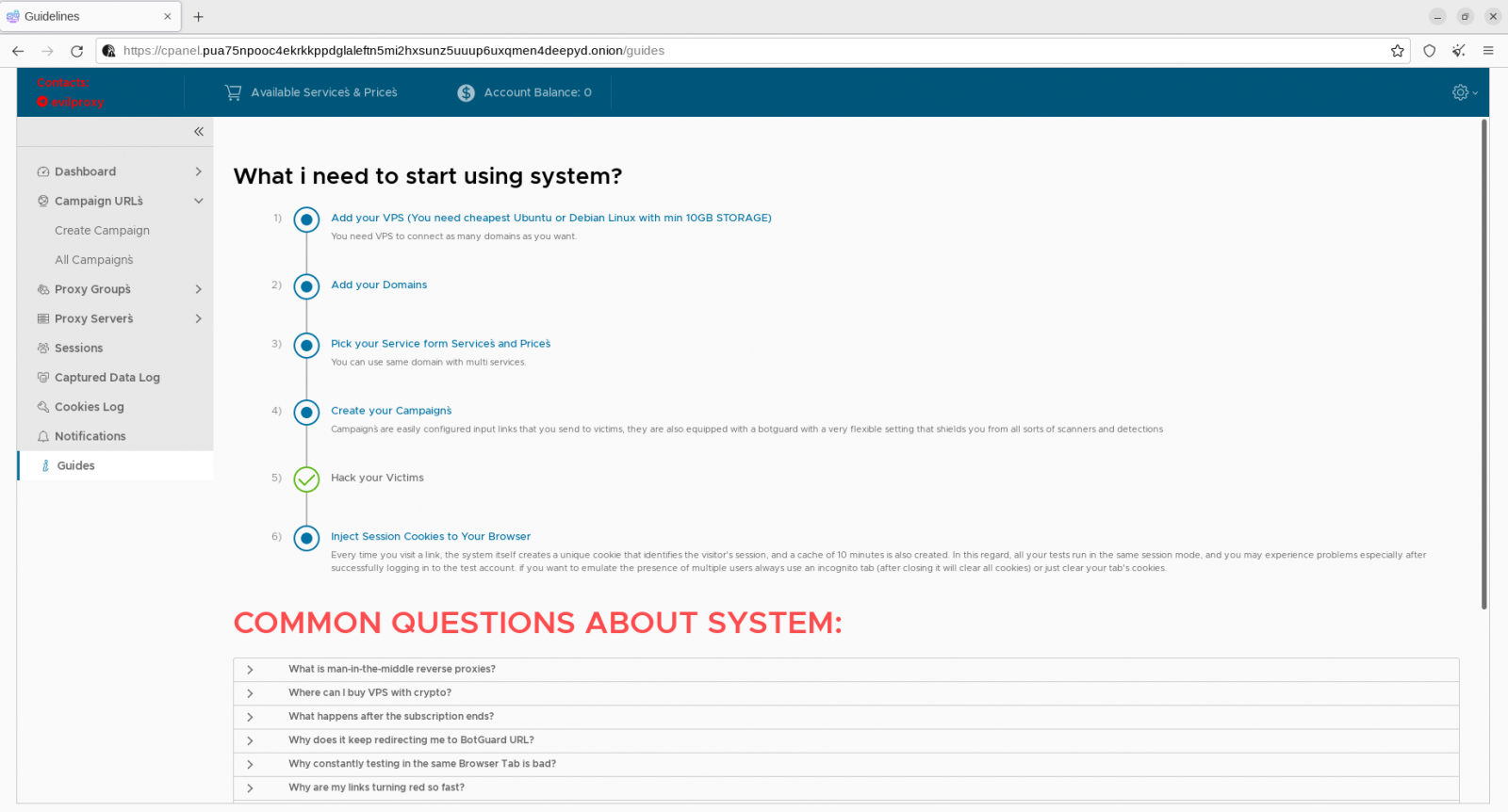
A deeper look at EvilProxy
Cybersecurity firm Resecurity reports that EvilProxy offers an easy-to-use GUI where threat actors can set up and manage phishing campaigns and all the details that underpin them.
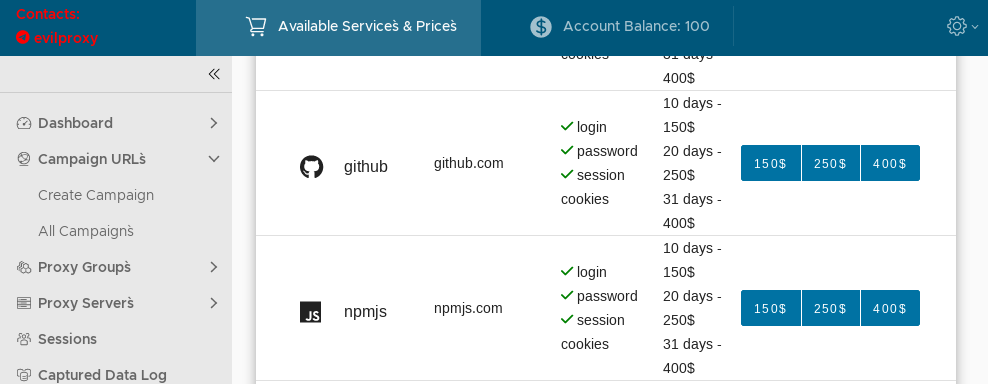
The service promises to steal usernames, passwords, and session cookies, for a cost of $150 for ten days, $250 for 20 days, or $400 for a month-long campaign. Attacks against Google accounts cost more, at $250/450/600.
In the following video, Resecurity demonstrates how an attack against a Google account would unfold through EvilProxy.
While the service is actively promoted on various clearnet and dark web hacking forums, the operators vet the clients, so some prospective buyers are likely rejected.
According to Resecurity, the payment for the service is arranged individually on Telegram. Once the deposit is made, the customer gets access to the portal hosted in the onion network (TOR).
Resecurity's test of the platform confirmed that EvilProxy also offers VM, anti-analysis, and anti-bot protection to filter out invalid or unwanted visitors on the phishing sites hosted by the platform.
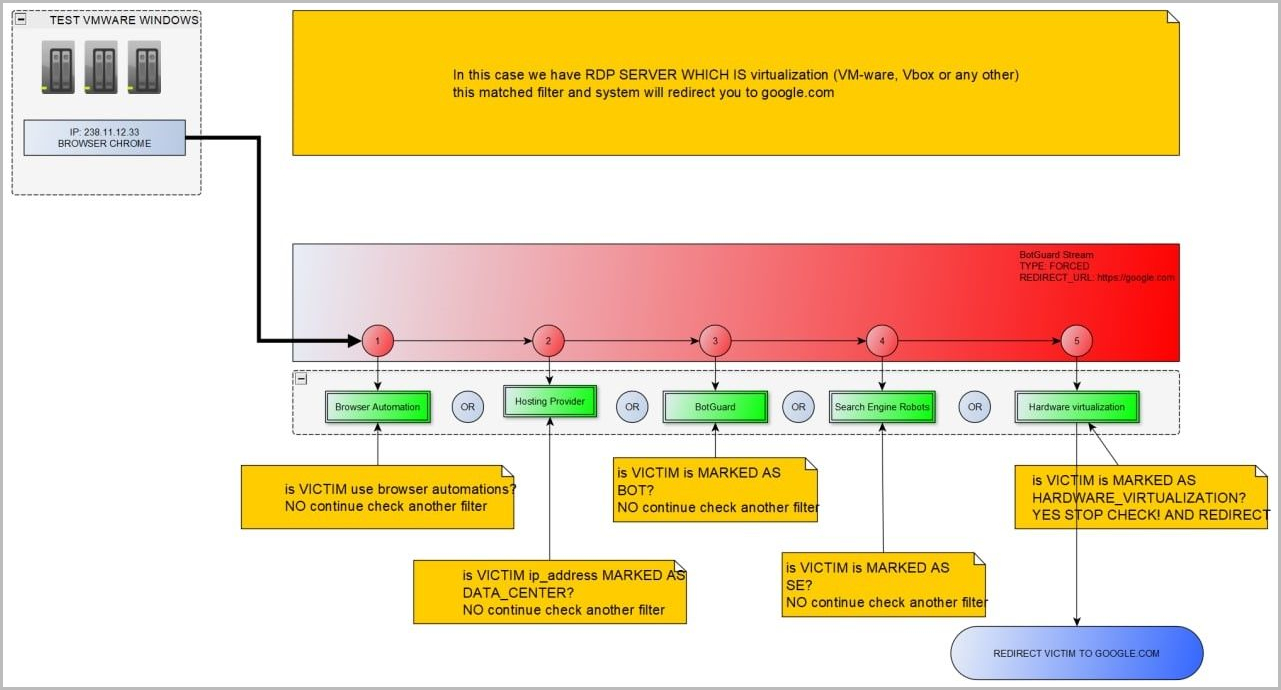
“The bad actors are using multiple techniques and approaches to recognize victims and to protect the phishing-kit code from being detected,” explains Resecurity in the report.
“Like fraud prevention and cyber threat intelligence (CTI) solutions, they aggregate data about known VPN services, Proxies, TOR exit nodes and other hosts which may be used for IP reputation analysis (of potential victims).”
A service to look out for
As MFA adoption continues to increase, more threat actors turn to reverse-proxy tools, and the appearance of a platform that automates everything for the crooks isn’t good news for security professionals and network admins.
.png)
For now, this problem remains addressable only by implementing client-side TLS fingerprinting to identify and filter out man-in-the-middle requests. However, the status of this implementation in the industry isn’t in sync with the developments.
Hence, platforms like EvilProxy essentially bridge the skill gap and offer low-tier threat actors a cost-efficient way to steal valuable accounts.
Source: Bleeping Computer
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.