New Cyber Espionage Group Targeting Ministries of Foreign Affairs
Cybersecurity researchers on Thursday took the wraps off a new cyberespionage group that has been behind a series of targeted attacks against diplomatic entities and telecommunication companies in Africa and the Middle East since at least 2017.
Dubbed "BackdoorDiplomacy," the campaign involves targeting weak points in internet-exposed devices such as web servers to perform a panoply of cyber hacking activities, including laterally moving across the network to deploy a custom implant called Turian that's capable of exfiltrating sensitive data stored in removable media.
"BackdoorDiplomacy shares tactics, techniques, and procedures with other Asia-based groups. Turian likely represents a next stage evolution of Quarian, the backdoor last observed in use in 2013 against diplomatic targets in Syria and the U.S," said Jean-Ian Boutin, head of threat research at Slovak cybersecurity firm ESET.
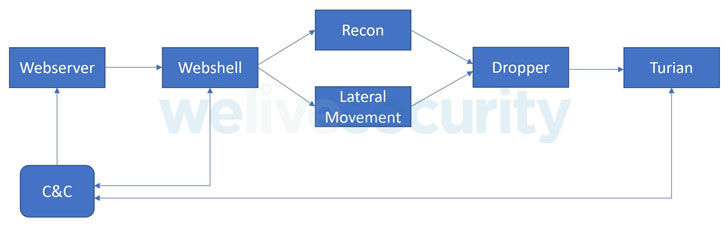
Engineered to target both Windows and Linux operating systems, the cross-platform group singles out management interfaces for networking equipment and servers with internet-exposed ports, likely exploiting unpatched vulnerabilities to deploy the China Chopper web shell for initial access, using it to conduct reconnaissance and install the backdoor.
Targeted systems include F5 BIG-IP devices (CVE-2020-5902), Microsoft Exchange servers, and Plesk web hosting control panels. Victims have been identified in the Ministries of Foreign Affairs of multiple African countries, as well as in Europe, the Middle East, and Asia. Additionally, telecom providers in Africa and at least one Middle Eastern charity have also been hit.
"In each case, operators employed similar tactics, techniques, and procedures (TTPs), but modified the tools used, even within close geographic regions, likely to make tracking the group more difficult," the researchers said. BackdoorDiplomacy is also believed to overlap with previously reported campaigns operated by a Chinese-speaking group Kaspersky tracks as "CloudComputating."
Besides its features to gather system information, take screenshots, and carry out file operations, ESET researchers said Turian's network encryption protocol is nearly identical to that employed by WhiteBird, a C++ backdoor operated by an Asia-based threat actor named Calypso, that was installed within diplomatic organizations in Kazakhstan and Kyrgyzstan, and during the same timeframe as BackdoorDiplomacy.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.