A threat actor presumed to be of Chinese origin has been linked to a series of 10 attacks targeting Mongolia, Russia, Belarus, Canada, and the U.S. from January to July 2021 that involve the deployment of a remote access trojan (RAT) on infected systems, according to new research.
The intrusions have been attributed to an advanced persistent threat named APT31 (FireEye), which is tracked by the cybersecurity community under the monikers Zirconium (Microsoft), Judgement Panda (CrowdStrike), and Bronze Vinewood (Secureworks).
The group is a "China-nexus cyber espionage actor focused on obtaining information that can provide the Chinese government and state-owned enterprises with political, economic, and military advantages," according to FireEye.
Positive Technologies, in a write-up published Tuesday, revealed a new malware dropper that was used to facilitate the attacks, including the retrieval of next-stage encrypted payloads from a remote command-and-control server, which are subsequently decoded to execute the backdoor.
The malicious code comes with the capacity to download other malware, potentially putting affected victims at further risk, as well as perform file operations, exfiltrate sensitive data, and even delete itself from the compromised machine.
"The code for processing the [self-delete] command is particularly intriguing: all the created files and registry keys are deleted using a bat-file," Positive Technologies researchers Denis Kuvshinov and Daniil Koloskov said.
Also worthy of particular note is the malware's similarities to that of a trojan named DropboxAES RAT that was put to use by the same threat group last year and relied on Dropbox for its command-and-control (C2) communications, with numerous overlaps found in the techniques and mechanisms used to inject the attack code, achieve persistence, and the mechanism employed to delete the espionage tool.
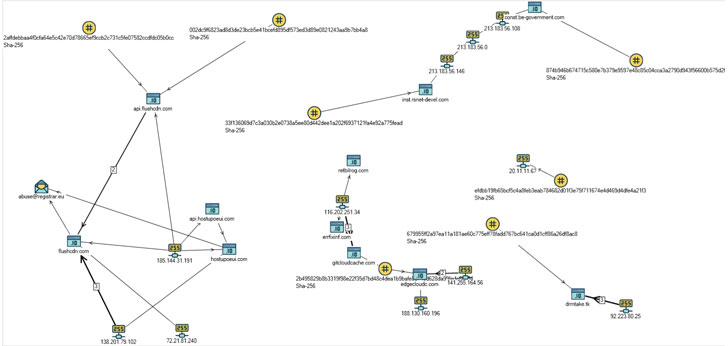
"The revealed similarities with earlier versions of malicious samples described by researchers, such as in 2020, suggest that the group is expanding the geography of its interests to countries where its growing activity can be detected, Russia in particular," the researchers concluded.
- Karlston
-

 1
1


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.