A new Android trojan called ‘Chameleon’ has been targeting users in Australia and Poland since the start of the year, mimicking the CoinSpot cryptocurrency exchange, an Australian government agency, and the IKO bank.
The mobile malware was discovered by cybersecurity firm Cyble, which reports seeing distribution through compromised websites, Discord attachments, and Bitbucket hosting services.
Chameleon includes a wide range of malicious functionality, including stealing user credentials through overlay injections and keylogging, cookies, and SMS texts from the infected device.
A focus on evasion
Upon launch, the malware performs a variety of checks to evade detection by security software.
These checks include anti-emulation checks to detect if the device is rooted and debugging is activated, increasing the likelihood that the app is running in an analyst’s environment.
If the environment appears clean, the infection continues, and Chameleon requests the victim to permit it to use the Accessibility Service, which it abuses to grant itself additional permissions, disable Google Play Protect, and stop the user from uninstalling it.
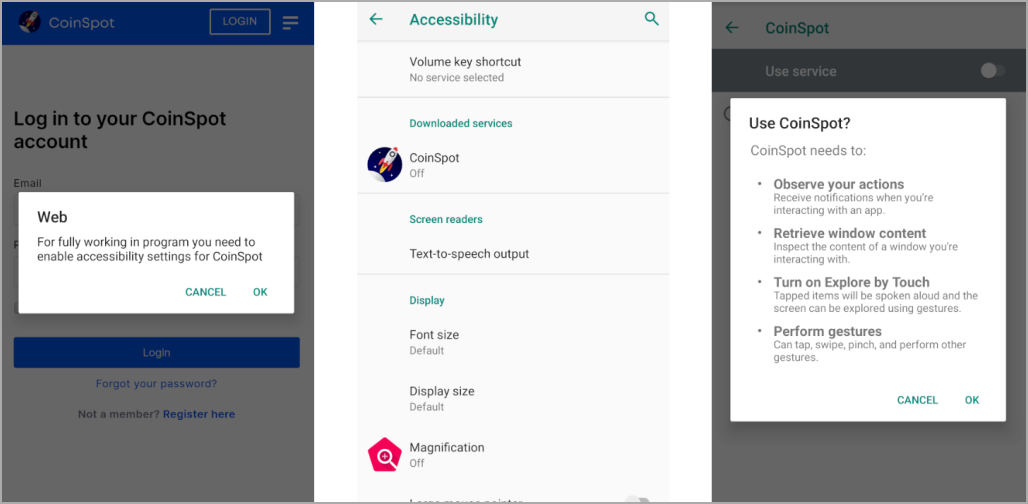
Requesting permission to use the Accessibility Service (Cyble)
At first connection with the C2, Chameleon sends the device version, model, root status, country, and precise location, probably to profile the new infection.
Next, depending on what entity the malware impersonates, it opens its legitimate URL in a WebView and starts loading malicious modules in the background.
These include a cookie stealer, a keylogger, an injector of phishing pages, a lock screen PIN/pattern grabber, and an SMS stealer that can snatch one-time passwords and help the attackers bypass 2FA protections.
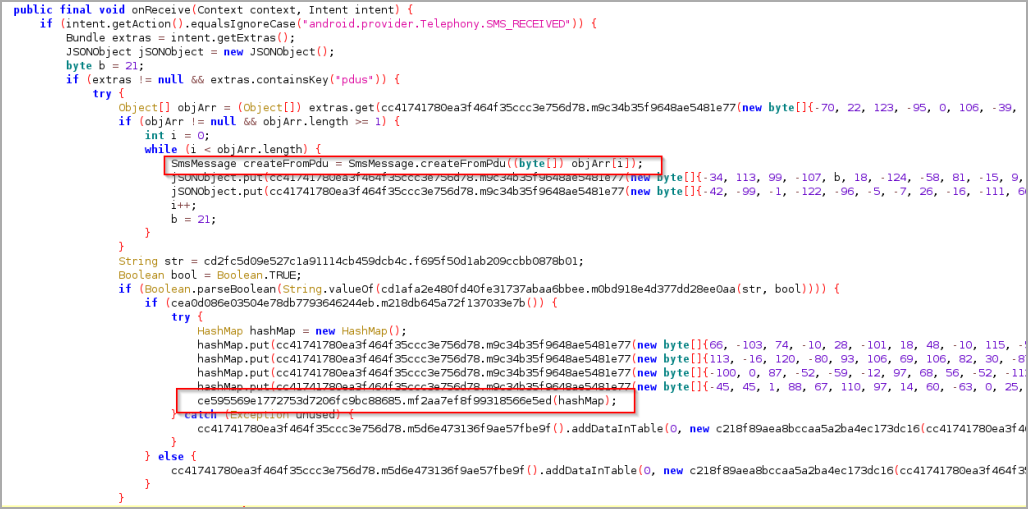
SMS interception (Cyble)
Most of these data-stealing systems rely on the abuse of Accessibility Services to work as required, allowing the malware to monitor the screen content, monitor for specific events, intervene to modify interface elements, or send certain API calls as needed.
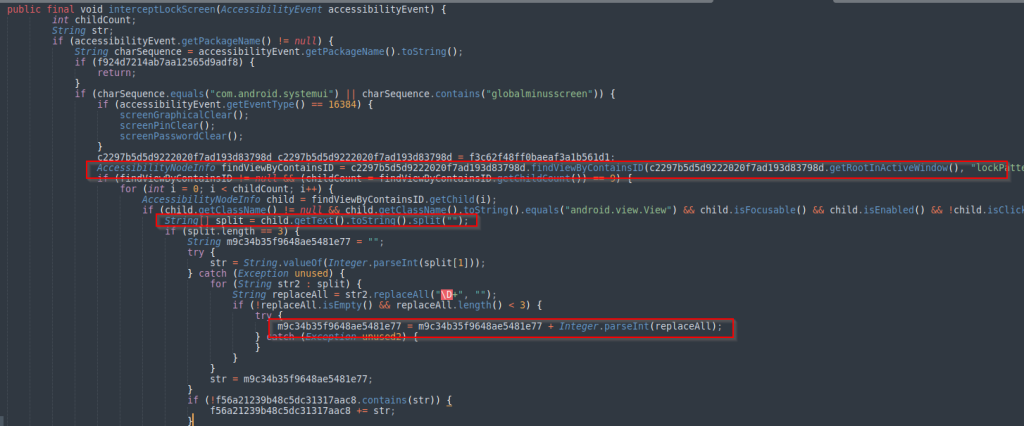
Abuse of Accessibility Service to retrieve lock screen password (Cyble)
The same system service is also abused to prevent the uninstallation of the malware, identifying when the victim attempts to remove the malicious app and deleting its shared preference variables to make it appear as if it’s no longer present in the device.
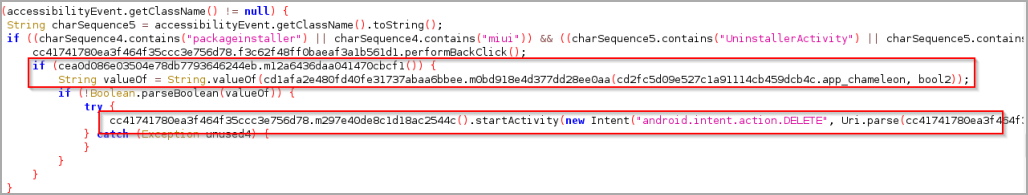
Auto-delete shared preferences variables (Cyble)
The wiping of shared preferences files forces the app to re-establish communications with the C2 the next time it launches but prevents its uninstallation and makes it harder for researchers to analyze.
Cyble also observed code that enables Chameleon to download a payload during runtime and save it on the host as a “.jar” file, to be executed later via DexClassLoader. However, this feature is currently unused.
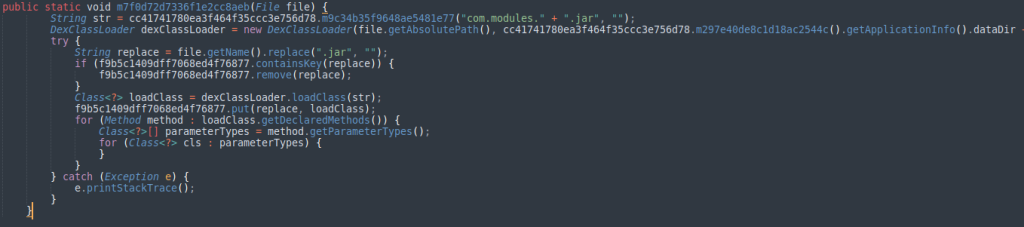
Code to download additional payloads (Cyble)
Chameleon is an emerging threat that may add more features and capabilities in future versions.
Android users are advised to be cautious with apps they install on their devices, only download software from official stores, and ensure that Google Play Protect is always enabled.
- aum and Karlston
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.