A new set of vulnerabilities in 5G modems by Qualcomm and MediaTek, collectively called "5Ghoul," impact 710 5G smartphone models from Google partners (Android) and Apple, routers, and USB modems.
5Ghoul was discovered by university researchers from Singapore and consists of 14 vulnerabilities in mobile communication systems, 10 of which have been publicly disclosed and four withheld for security reasons.
The 5Ghoul attacks range from temporary service disruptions to network downgrades, which may be more severe from a security standpoint.
The researchers discovered the flaws while experimenting with 5G modem firmware analysis and report that the flaws are easy to exploit over-the-air by impersonating a legitimate 5G base station.
This applies even when attackers lack information about the target's SIM card, as the attack occurs before the NAS authentication step.
"The attacker does not need to be aware of any secret information of the target UE e.g., UE's SIM card details, to complete the NAS network registration," explains the researchers on their website.
"The attacker only needs to impersonate the legitimate gNB using the known Cell Tower connection parameters (e.g., SSB ARFCN, Tracking Area Code, Physical Cell ID, Point A Frequency)."
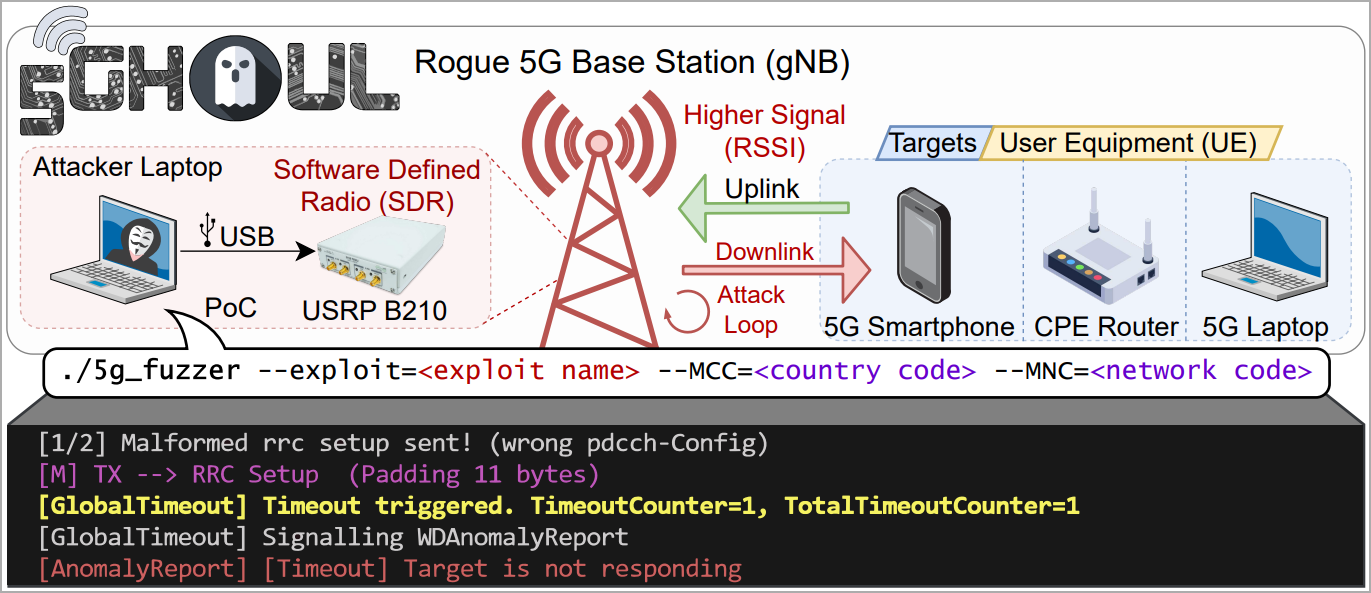
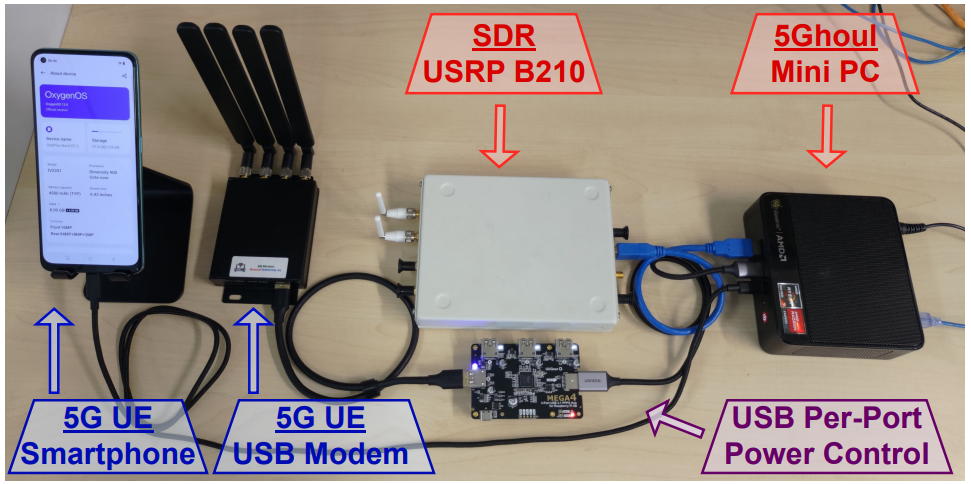
The above is achievable at the cost of a few thousand USD, using open-source software for network analysis and fuzzing, a mini PC, a software defined radio (SDR), and miscellaneous equipment like cables, antennas, power supplies, etc.
5Ghoul vulnerability details
The ten 5Ghoul vulnerabilities that have been publicly disclosed to Qualcomm and MediaTek as of December 7, 2023, are:
- CVE-2023-33043: Invalid MAC/RLC PDU causing Denial of Service (DoS) in Qualcomm X55/X60 modems. Attackers can send an invalid downlink MAC frame to the target 5G UE from a nearby malicious gNB, leading to a temporary hang and modem reboot.
- CVE-2023-33044: NAS Unknown PDU causing DoS in Qualcomm X55/X60 modems. This vulnerability allows attackers to send an invalid NAS PDU to the target UE, resulting in modem failure and reboot.
- CVE-2023-33042: Disabling 5G/Downgrade via Invalid RRC pdcch-Config in Qualcomm X55/X60 modems, leading to either downgrade or denial of service. An attacker can send a malformed RRC frame during the RRC Attach Procedure, disabling 5G connectivity and requiring a manual reboot for restoration.
- CVE-2023-32842: Invalid RRC Setup spCellConfig causing DoS in MediaTek Dimensity 900/1200 modems. The vulnerability involves sending a malformed RRC Connection Setup, leading to modem failure and reboot in affected devices.
- CVE-2023-32844: Invalid RRC pucch CSIReportConfig causing DoS in MediaTek Dimensity 900/1200 modems. Attackers can send a malformed RRC Connection Setup, causing the modem to fail and reboot.
- CVE-2023-20702: Invalid RLC Data Sequence causing DoS (null pointer dereference) in MediaTek Dimensity 900/1200 modems. An attacker can exploit this by sending a malformed RLC Status PDU, leading to a modem crash and reboot.
- CVE-2023-32846: Truncated RRC physicalCellGroupConfig causing DoS (null pointer dereference) in MediaTek Dimensity 900/1200 modems. Malformed RRC Connection Setup can cause memory access errors, leading to a modem crash.
- CVE-2023-32841: Invalid RRC searchSpacesToAddModList causing DoS in MediaTek Dimensity 900/1200 modems. This involves sending a malformed RRC Connection Setup, causing a modem crash in affected devices.
- CVE-2023-32843: Invalid RRC Uplink Config Element causing DoS in MediaTek Dimensity 900/1200 modems. Sending a malformed RRC Connection Setup can result in modem failure and reboot in affected devices.
- CVE-2023-32845: Null RRC Uplink Config Element causing DoS in MediaTek Dimensity 900/1200 modems. Malformed RRC Connection Setup can trigger a modem crash by setting certain RRC payload fields to null.
CVE-2023-33042 is particularly concerning because it can force a device to disconnect from a 5G network and fall back to 4G, exposing it to potential vulnerabilities in the 4G domain that expose it to a broader range of attacks.
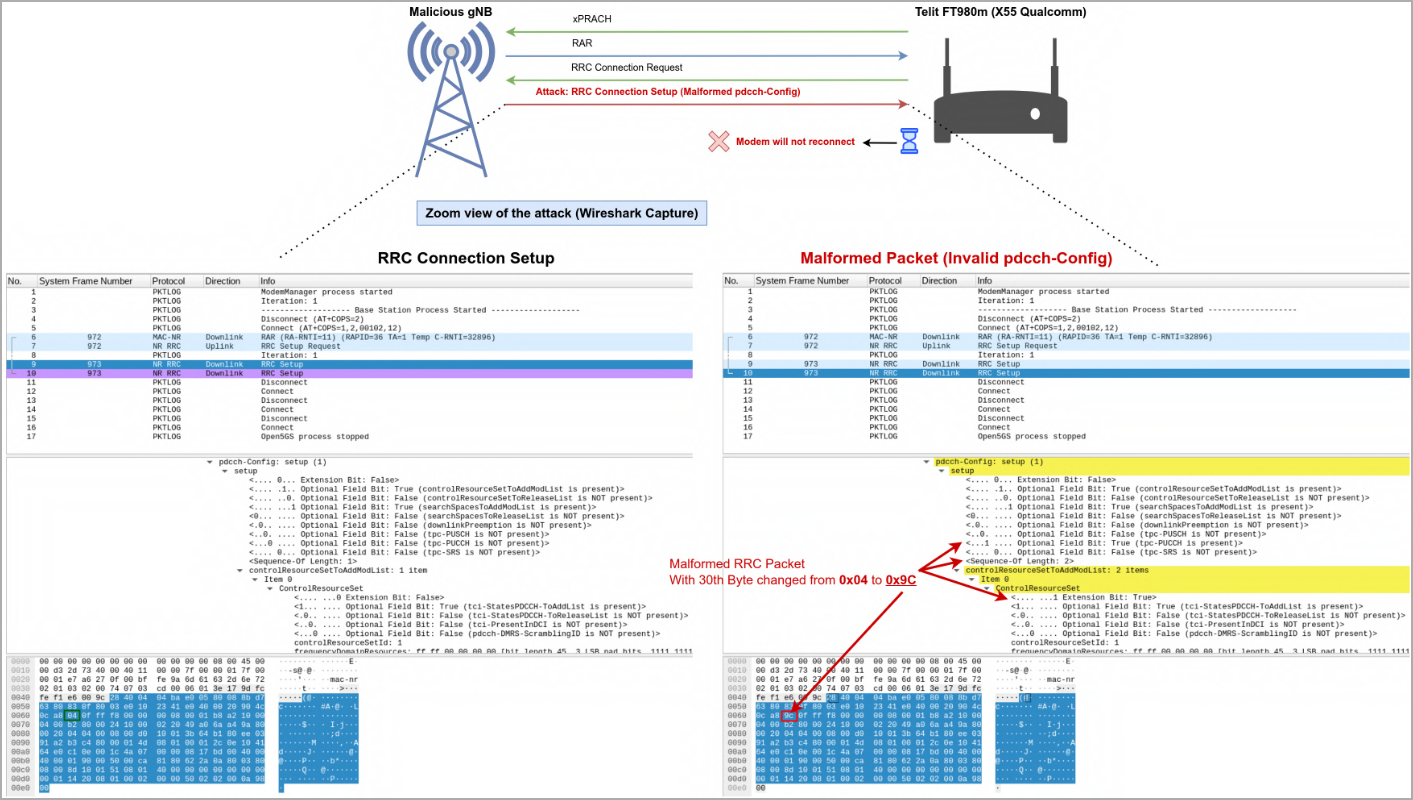
The DoS flaws in these vulnerabilities cause the devices to lose all connectivity until they are rebooted. This isn't as critical, although it can still have significant implications in mission-critical environments that rely on cellular service.
It is important to note that the disclosed flaws aren't limited to the devices mentioned in the above list.
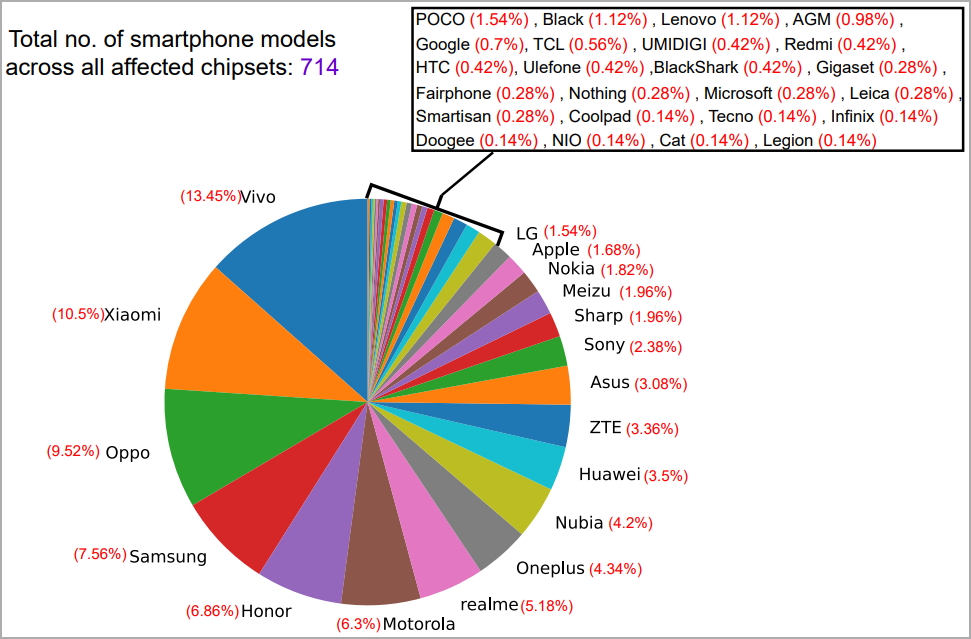
Identifying all impacted models is ongoing, but the researchers have already confirmed that 714 smartphones from 24 brands are impacted.
Some vulnerable brands include phones from POCO, Black, Lenovo, AGM, Google, TCL, Redmi, HTC, Microsoft, and Gigaset, with the complete list in the image below.
To learn more about the 5Ghoul flaws, their exploitation potential and ramifications, and technical information can be found in the researchers' whitepaper.
A proof-of-concept (PoC) exploit kit can also be found in their GitHub repository.
Vendor response and fixes
Both Qualcomm and MediaTek released security bulletins on Monday for the disclosed 5Ghoul vulnerabilities,
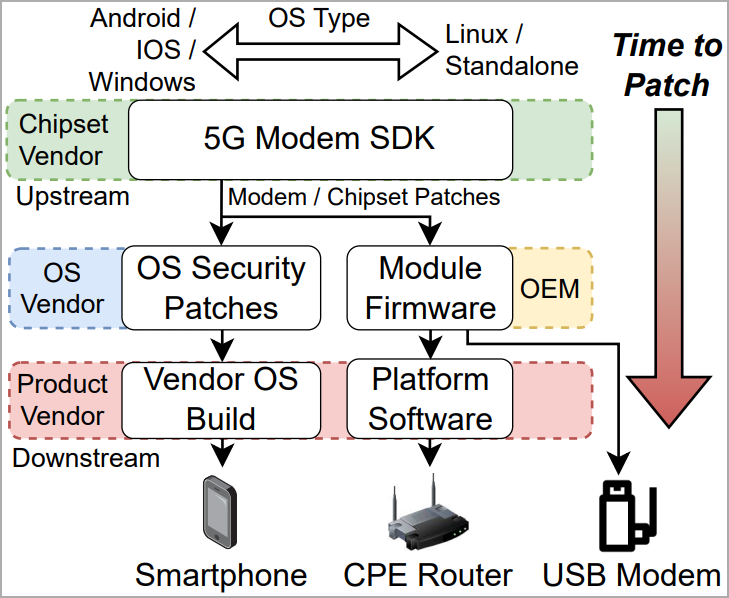
The security updates were made available to device vendors two months ago. Still, given the complexity of the software supply, especially on Android, it will be a while before the fixes reach the end users via security updates.
Inevitably, some impacted smartphone models and other devices will never receive the fixes as they will likely reach end of support first.
If you're overly worried about 5Ghool flaws, the only practical solution is to avoid using 5G entirely until fixes are available.
Signs of a 5Ghoul attack include loss of 5G connections, inability to re-connect until the device is rebooted, and consistent drop to 4G despite the availability of a 5G network in the area.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.