A new iOS and Android trojan named 'GoldPickaxe' employs a social engineering scheme to trick victims into scanning their faces and ID documents, which are believed to be used to generate deepfakes for unauthorized banking access.
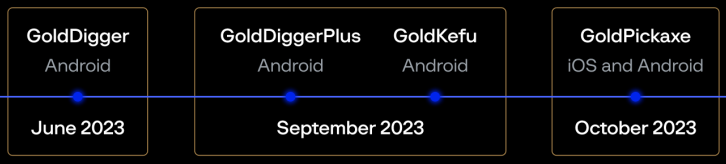
The new malware, spotted by Group-IB, is part of a malware suite developed by the Chinese threat group known as 'GoldFactory,' which is responsible for other malware strains such as 'GoldDigger', 'GoldDiggerPlus,' and 'GoldKefu.'
Group-IB says its analysts observed attacks primarily targeting the Asia-Pacific region, mainly Thailand and Vietnam. However, the techniques employed could be effective globally, and there's a danger of them getting adopted by other malware strains.
Starts with social engineering attacks
The distribution of Gold Pickaxe started in October 2023 and is still ongoing. It is considered part of a GoldFactory campaign that began in June 2023 with Gold Digger.
Victims are approached through phishing or smishing messages on the LINE app that are written in their local language, impersonating government authorities or services.
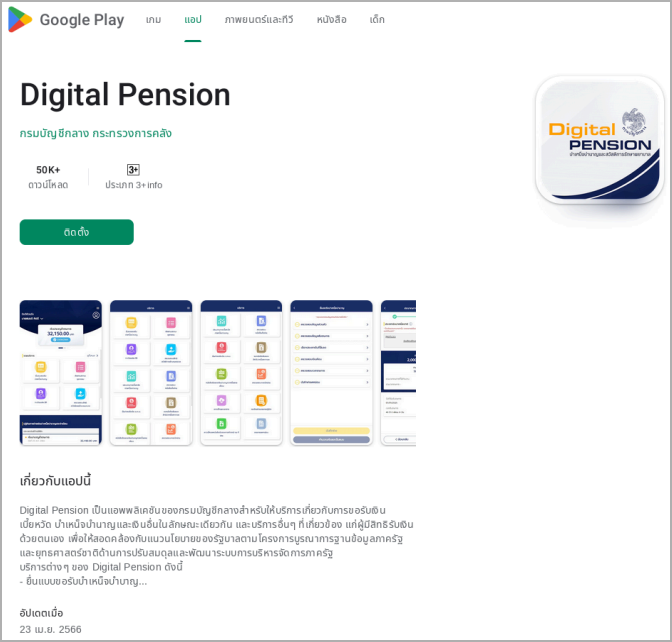
The messages attempt to trick them into installing fraudulent apps, such as a fake 'Digital Pension' app hosted on websites impersonating Google Play.
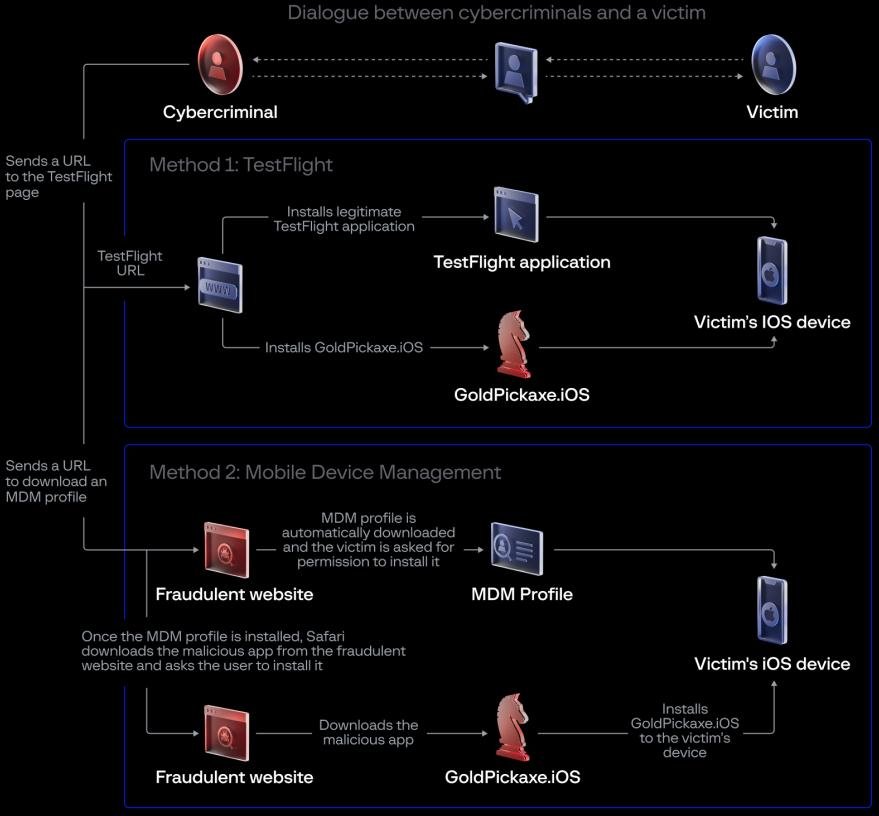
For iOS (iPhone) users, the threat actors initially directed targets to a TestFlight URL to install the malicious app, allowing them to bypass the normal security review process.
When Apple remove the TestFlight app, the attackers switched to luring targets into downloading a malicious Mobile Device Management (MDM) profile that allows the threat actors to take control over devices.
Gold Pickaxe capabilities
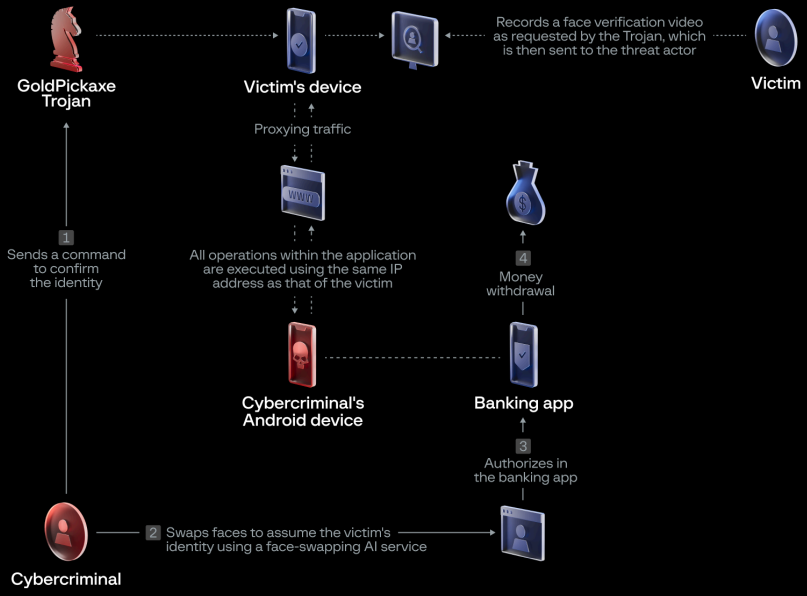
Once the trojan has been installed onto a mobile device in the form of a fake government app, it operates semi-autonomously, manipulating functions in the background, capturing the victim's face, intercepting incoming SMS, requesting ID documents, and proxying network traffic through the infected device using 'MicroSocks.'
On iOS devices, the malware establishes a web socket channel to receive the following commands:
- Heartbeat: ping command and control (C2) server
- init: send device information to the C2
- upload_idcard: request the victim to take an image of their ID card
- face: request the victim to take a video of their face
- upgrade: display bogus “device in use” message to prevent interruptions
- album: sync photo library date (exfiltrate to a cloud bucket)
- again_upload: retry exfiltration of victim's face video to the bucket
- destroy: stop the trojan
The results of executing the above commands are communicated back to the C2 via HTTP requests.
Group-IB says the Android version of the trojan performs more malicious activities than in iOS due to Apple's higher security restrictions. Also, on Android, the trojan uses over 20 different bogus apps as cover.
For example, GoldPickaxe can also run commands on Android to access SMS, navigate the filesystem, perform clicks on the screen, upload the 100 most recent photos from the victim's album, download and install additional packages, and serve fake notifications.

The use of the victims' faces for bank fraud is an assumption by Group-IB, also corroborated by the Thai police, based on the fact that many financial institutes added biometric checks last year for transactions above a certain amount.
It is essential to clarify that while GoldPickaxe can steal images from iOS and Android phones showing the victim's face and trick the users into disclosing their face on video through social engineering, the malware does not hijack Face ID data or exploit any vulnerability on the two mobile OSes.
Biometric data stored on the devices' secure enclaves is still appropriately encrypted and completely isolated from running apps.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.