Almost 11 million internet-exposed SSH servers are vulnerable to the Terrapin attack that threatens the integrity of some SSH connections.
The Terrapin attack targets the SSH protocol, affecting both clients and servers, and was developed by academic researchers from Ruhr University Bochum in Germany.
It manipulates sequence numbers during the handshake process to compromise the integrity of the SSH channel, particularly when specific encryption modes like ChaCha20-Poly1305 or CBC with Encrypt-then-MAC are used.
An attacker could thus downgrade the public key algorithms for user authentication and disable defenses against keystroke timing attacks in OpenSSH 9.5.
A notable requirement for the Terrapin attack is the need for attackers to be in an adversary-in-the-middle (AitM) position to intercept and modify the handshake exchange.
It is worth noting that threat actors often compromise networks of interest and wait for the right moment to progress their attack.
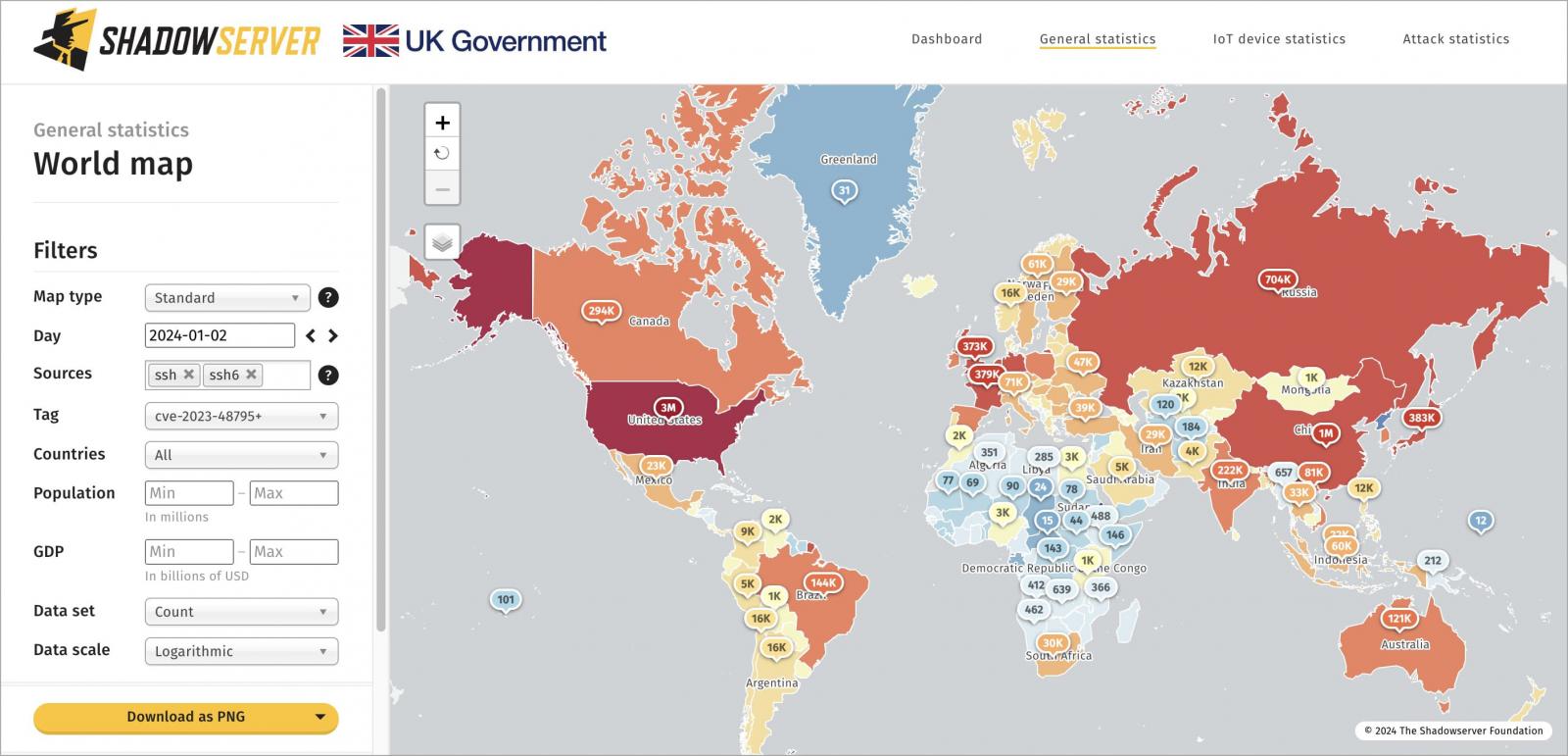
A recent report by security threat monitoring platform Shadowserver warns that there are nearly 11 million SSH servers on the public web - identified by unique IP addresses, that are vulnerable to Terrapin attacks.
This constitutes roughly 52% of all scanned samples in the IPv4 and IPv6 space monitored by Shadoserver.
Most of the vulnerable systems were identified in the United States (3.3 million), followed by China (1.3 million), Germany (1 million), Russia (700,000), Singapore (390,000), and Japan (380,000).
The significance of Shadowserver’s report lies in highlighting that Terrapin attacks can have a widespread impact.
While not all 11 million instances are at immediate risk of being attacked, it shows that adversaries have a large pool to choose from.
If you want to check an SSH client or server for its susceptibility to Terrapin, the Ruhr University Bochum team provides a vulnerability scanner.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.