Molerats Hackers Return With New Attacks Targeting Middle Eastern Governments
A Middle Eastern advanced persistent threat (APT) group has resurfaced after a two-month hiatus to target government institutions in the Middle East and global government entities associated with geopolitics in the region in a rash of new campaigns observed earlier this month.
Sunnyvale-based enterprise security firm Proofpoint attributed the activity to a politically motivated threat actor it tracks as TA402, and known by other monikers such as Molerats and GazaHackerTeam.
The threat actor is believed to be active for a decade, with a history of striking organizations primarily located in Israel and Palestine, and spanning multiple verticals such as technology, telecommunications, finance, academia, military, media, and governments.
The latest wave of attacks commenced with spear-phishing emails written in Arabic and containing PDF attachments that come embedded with a malicious geofenced URL to selectively direct victims to a password-protected archive only if the source IP address belongs to the targeted countries in the Middle East.
Recipients who fall outside of the target group are diverted to a benign decoy website, typically Arabic language news websites like Al Akhbar (www.al-akhbar.com) and Al Jazeera (www.aljazeera.net).
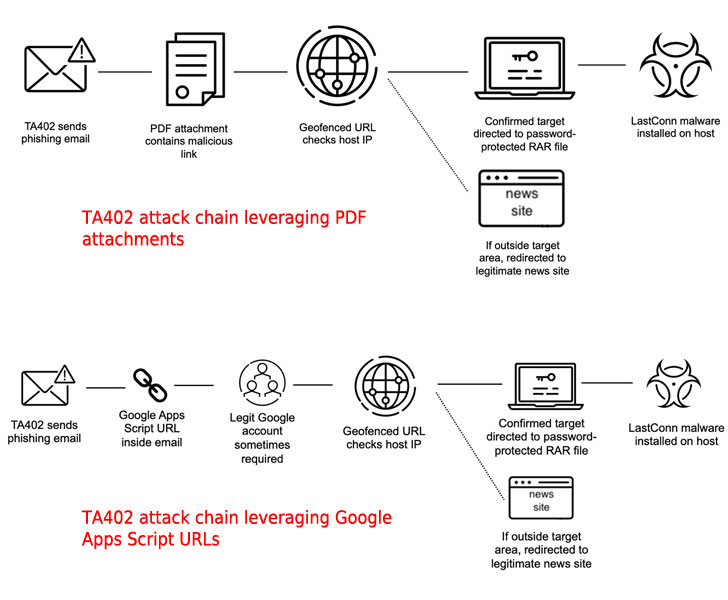
"The password protection of the malicious archive and the geofenced delivery method are two easy anti-detection mechanisms threat actors can use to bypass automatic analysis products," the researchers said.
The last step in the infection chain involved extracting the archive to drop a custom implant called LastConn, which Proofpoint said is an upgraded or new version of a backdoor called SharpStage that was disclosed by Cybereason researchers in December 2020 as part of a Molerats espionage campaign targeting the Middle East.
Besides displaying a decoy document when LastConn is run for the first time, the malware relies heavily on Dropbox API to download and execute files hosted on the cloud service, in addition to running arbitrary commands and capturing screenshots, the results of which are subsequently exfiltrated back to Dropbox.
If anything, the ever-evolving toolset of TA402 underscores the group's continued focus on developing and modifying customized malware implants in an attempt to sneak past defenses and thwart detection.
"TA402 is a highly effective and capable threat actor that remains a serious threat, especially to entities operating in and working with government or other geopolitical entities in the Middle East," the researchers concluded. "It is likely TA402 continues its targeting largely focused on the Middle East region."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.