Researchers from four American universities have developed a new GPU side-channel attack that leverages data compression to leak sensitive visual data from modern graphics cards when visiting web pages.
The researchers have demonstrated the effectiveness of this 'GPU.zip' attack by performing cross-origin SVG filter pixel-stealing attacks through the Chrome browser.
The researchers disclosed the vulnerability to impacted video card manufacturers in March 2023. However, as of September 2023, no affected GPU vendors (AMD, Apple, Arm, NVIDIA, Qualcomm) or Google (Chrome) have rolled out patches to address the problem.
The new flaw is outlined in a paper from researchers at the University of Texas at Austin, Carnegie Mellon University, University of Washington, and University of Illinois Urbana-Champaign and will appear in the 45th IEEE Symposium on Security and Privacy.
Leaking through compression
Generally, data compression creates distinct data-dependent DRAM traffic and cache utilization, which can be abused for leaking secrets, so software turns off compression when handling sensitive data.
The GPU.zip researchers explain that all modern graphic processor units, especially integrated Intel and AMD chips, perform software-visible data compression even when not explicitly asked.
Modern GPUs follow this risky practice as an optimization strategy, as it helps save on memory bandwidth and improve performance without software.
This compression is often undocumented and vendor-specific, and the researchers have found a way to exploit it to leak visual data from GPUs.
Specifically, they demonstrated an attack that extracts individual pixel data through a web browser on various devices and GPU architectures, as shown below.
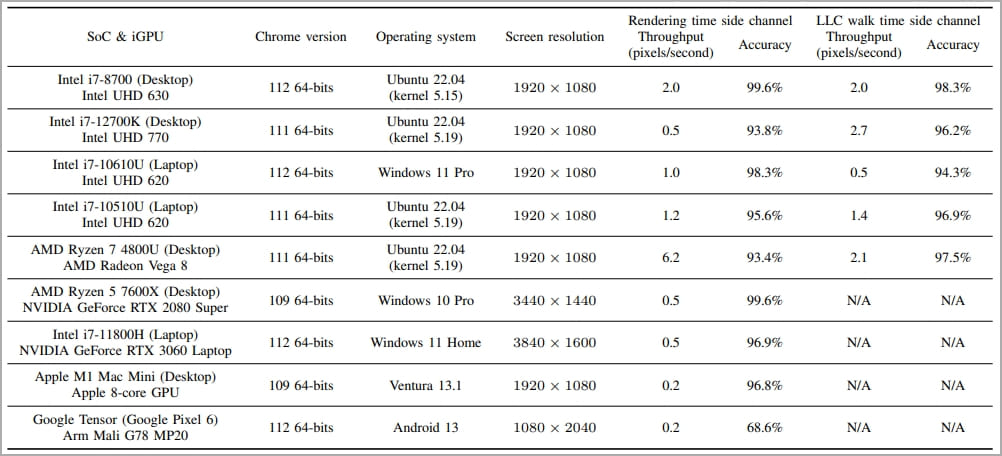
The proof-of-concept attack demonstrates stealing the username from a Wikipedia iframe, which is possible within 30 minutes on Ryzen and 215 minutes on Intel GPUs, at accuracies of 97% and 98.3%, respectively.
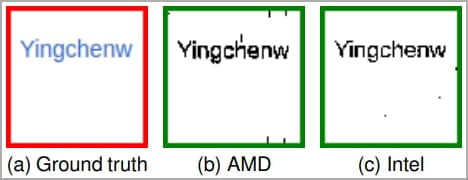
The iframe hosts a cross-origin webpage whose pixels are isolated and turned into binary, meaning they're converted into two possible colours.
Next, these pixels are enlarged, and a specialized SVG filter stack is applied to create textures that are either compressible or not. By measuring the time taken for the texture to render, the researchers can deduce the original colour/state of the target pixel.
We have recently seen the application of SVG filters to induce data-dependent execution and the use of JavaScript to measure computation time and frequency to discern the pixel's colour on the "Hot Pixels" attack.
While Hot Pixels exploits data-dependent computation times on modern processors, GPU.zip hinges on undocumented GPU data compression to achieve similar results.
GPU.zip severity
GPU.zip impacts almost all major GPU manufacturers, including AMD, Apple, Arm, Intel, Qualcomm, and NVIDIA, but not all cards are equally affected.
The fact that none of the impacted vendors have decided to fix the issue by optimizing their data compression approach and limiting its operation to non-sensitive cases further raises the risk.
Although GPU.zip potentially impacts the vast majority of laptops, smartphones, tablets, and desktop PCs worldwide, the immediate impact on users is moderated by the complexity and time required to perform the attack.
Also, websites that deny cross-origin iframe embedding cannot be used for leaking user data through this or similar side-channel attacks.
"Most sensitive websites already deny being embedded by cross-origin websites. As a result, they are not vulnerable to the pixel stealing attack we mounted using GPU.zip," explains the researchers in a FAQ on the team's website.
Finally, the researchers note that Firefox and Safari do not meet all the criteria needed for GPU.zip to work, such as allowing cross-origin iframes to be loaded with cookies, rendering SVG filters on iframes, and delegating rendering tasks to the GPU.
- Mutton
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.