Security researchers have discovered that Minecraft is the most heavily abused game title by cybercriminals, who use it to lure unsuspecting players into installing malware.
Based on stats collected by the security firm between July 2021 and July 2022, Minecraft-related files accounted for roughly 25% of malicious files spreading via game brand abuse, followed by FIFA (11%), Roblox (9.5%), Far Cry (9.4%), and Call of Duty (9%).
Other game titles with notable percentages of abuse during this period are Need for Speed, Grand Theft Auto, Valorant, The Sims, and GS:GO.
On the mobile space, Kaspersky recorded much smaller distribution volumes than those seen on PC gaming. Yet, Minecraft dominates this category, too, with a 40% share, followed by GTA (15%), PUBG (10%), Roblox (10%), and FIFA (5%).
In terms of yearly trends, Kaspersky reports seeing a drop in both the volumes of distribution (-30%) and the number of affected users (-36%) compared to 2020.
Why hackers use games as lures
Some recent examples of hiding malware in packages promoted as game cheats, installers, keygens, or as the games themselves are the following:
- Minecraft alt lists on gaming forums dropping Chaos ransomware
- NPM packages posing as Roblox libraries delivering ransomware and password stealers
- Games clones on the Microsoft Store containing malware loaders
- Valorant cheats promoted via YouTube dropping info-stealing malware
The reason why hackers leverage game titles to lure people is mainly the massive targeting pool, as the abused game titles attract the interest of tens of millions of people.
Moreover, modern games almost always involve the in-game economy aspect, so promises for “easy progress” through hacks, valuable items, and cheats of all kinds are enticing to users.
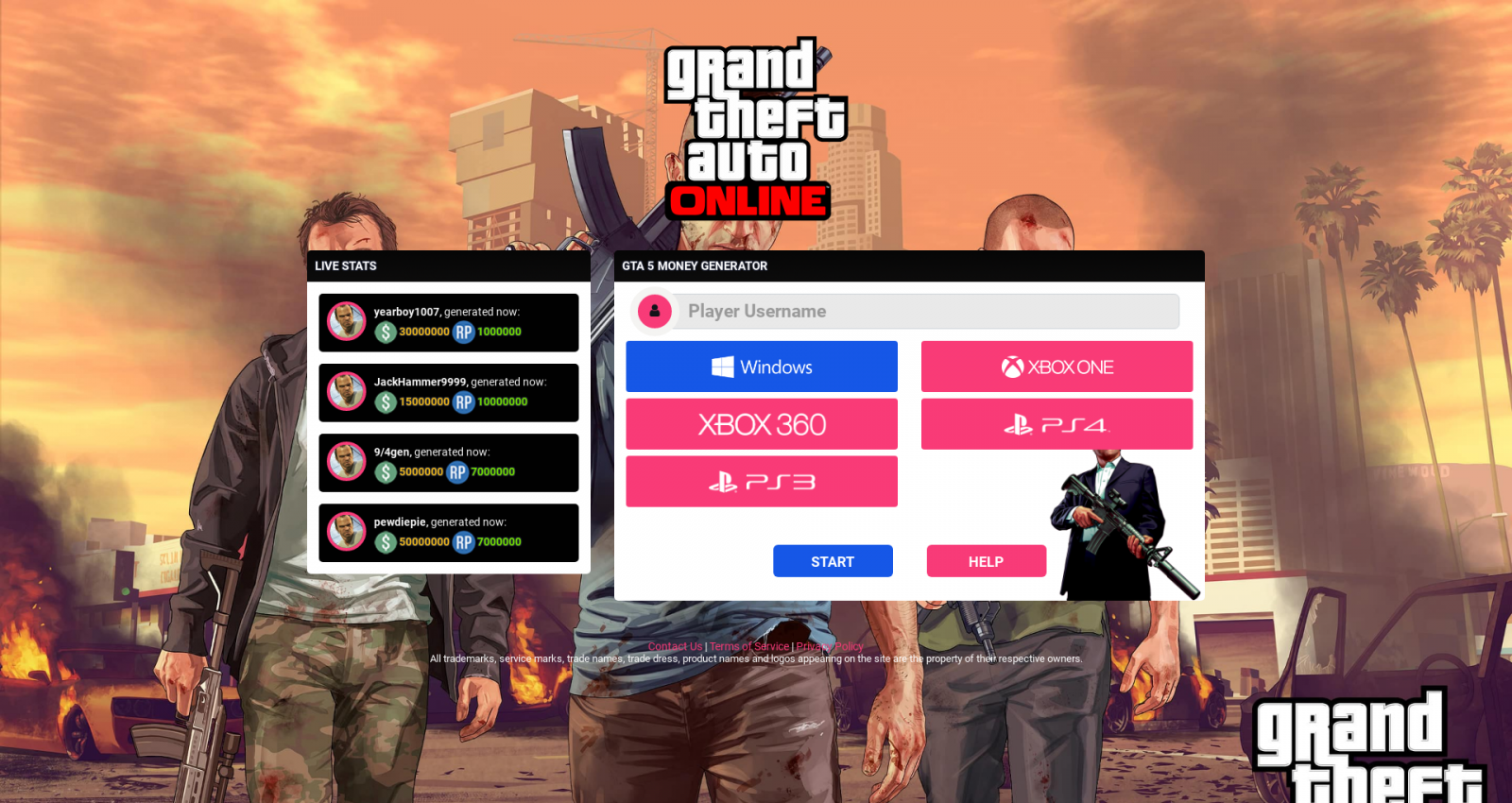
Kaspersky highlights a few examples of fraudulent in-game item stores that cloned originals, tricking players into paying for items they’ll never receive while also phishing their account credentials.
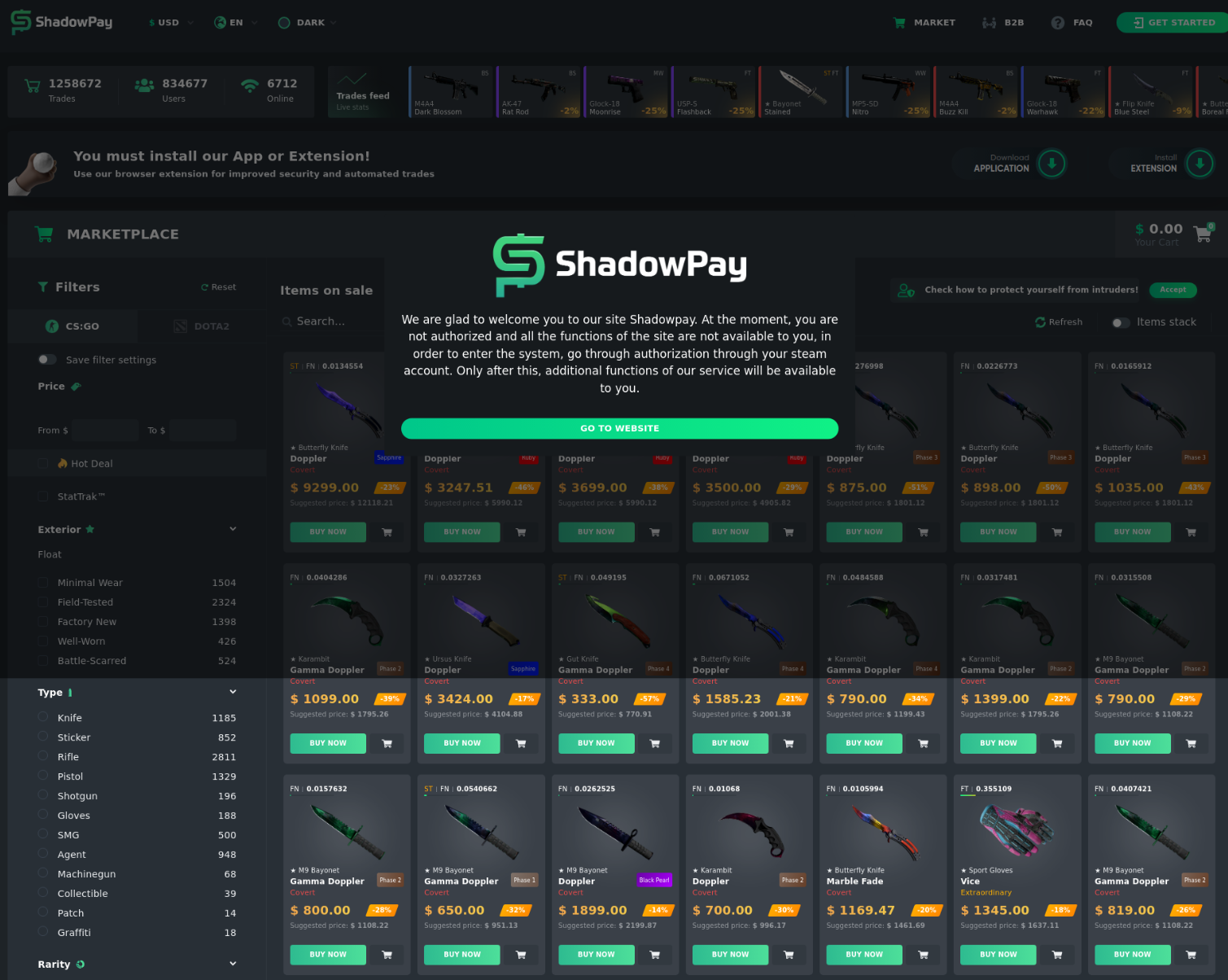
Games themselves often have a prohibitory cost for some people who then seek pirated alternatives. Other games are in a closed beta development status, excluding many interested individuals, causing users to search for different ways to gain access. Hackers exploit these conditions by offering fake pirated versions of phony beta testing launchers.
Finally, because many game-related mods, cheats, and tools are made by unofficial one-person projects and face false positive security detections, many developers warn victims to disable antivirus before installing them.
Due to this, gamers may ignore AV warnings and execute detected malware programs on their systems.
What files are dropped
Kaspersky’s statistics indicate that most malicious files targeting players are downloaders, accounting for 88.5% of all detected infection cases.
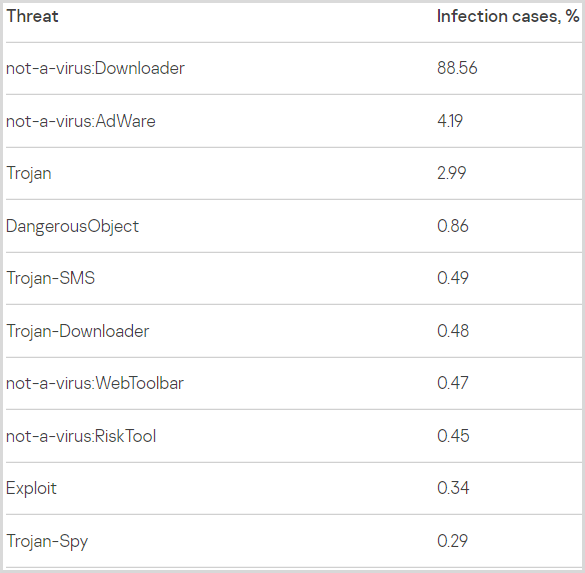
Other threat types with substantial percentages are adware (4.2%), and trojans that can steal user data or give threat actors remote access to the host machine (3%).
Downloaders take the lion’s share because they can come up clean on internet security scans but fetch riskier payloads at a second stage when the user executes the program.
In many cases, according to Kaspersky, info-stealers, cryptocurrency miners, or both are dropped onto the victim’s computer.
As always, be careful of downloading free software from the Internet and only do so from trusted sites.
Furthermore, if any developer states that you must disable antivirus to properly run the program, you should stay far away from it, as there is no limit to the malicious behavior that can be performed.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.