Microsoft's incomplete PrintNightmare patch fails to fix vulnerability
Researchers have bypassed Microsoft's emergency patch for the PrintNightmare vulnerability to achieve remote code execution and local privilege escalation with the official fix installed.
Last night, Microsoft released an out-of-band KB5004945 security update that was supposed to fix the PrintNightmare vulnerability that researchers disclosed by accident last month.
After the update was released, security researchers Matthew Hickey, co-founder of Hacker House, and Will Dormann, a vulnerability analyst for CERT/CC, determined that Microsoft only fixed the remote code execution component of the vulnerability.
However, malware and threat actors could still use the local privilege escalation component to gain SYSTEM privileges on vulnerable systems for older Windows versions, and for newer versions if the Point and Print policy was enabled.
Today, as more researchers began modifying their exploits and testing the patch, it was determined that exploits could bypass the entire patch entirely to achieve both local privilege escalation (LPE) and remote code execution (RCE).
According to Mimikatz creator Benjamin Delpy, the patch could be bypassed to achieve Remote Code Execution when the Point and Print policy is enabled.
Dormann also confirmed this patch bypass on Twitter.
To bypass the PrintNightmare patch and achieve RCE and LPE, a Windows policy called 'Point and Print Restrictions' must be enabled, and the "When installing drivers for a new connection" setting configured as "Do not show warning on elevation prompt."
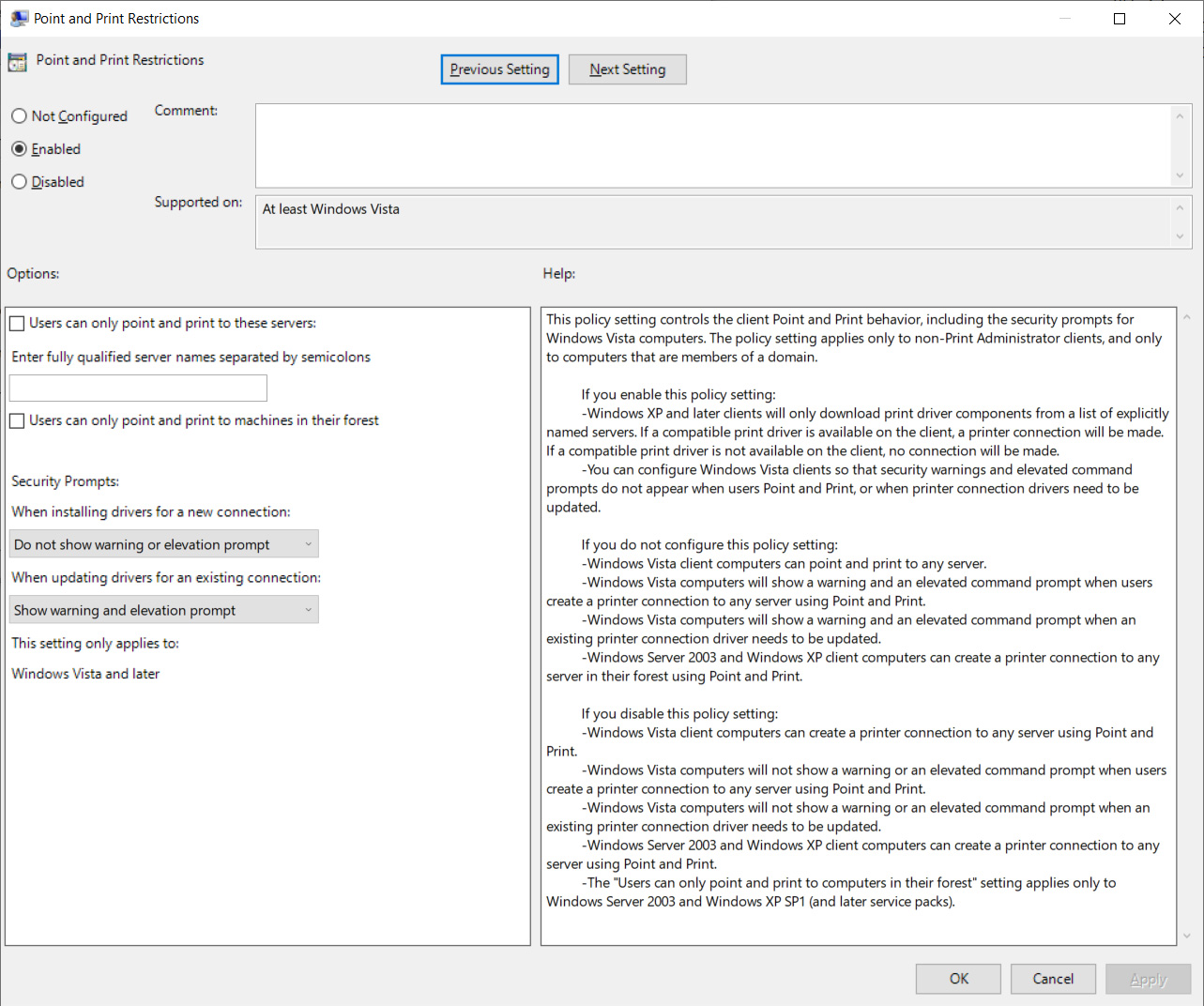
This policy is located under Computer Configuration > Administrative Templates > Printers > Point and Print Restrictions.
When enabled, the 'NoWarningNoElevationOnInstall' value will be set to 1 under the HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint key.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint]
"NoWarningNoElevationOnInstall"=dword:00000001
Hickey told BleepingComputer that he is still advising admins and users to disable the Print Spooler service to protect their Windows servers and workstations until a working patch is released.
"We're still advising our clients to disable the printer spooler wherever its not required until a fix arrives that addresses this issue appropriately," Hickey told BleepingComputer.
0patch has also released a free micropatch for PrintNightmare that has so far been able to block attempts at exploiting the vulnerability.
However, they are warning against installing Microsoft's July 6th patch as it not only doesn't protect against the vulnerabilities but modifies the 'localspl.dll' file so 0Patch's patch no longer works.
"If you're using 0patch against PrintNightmare, DO NOT apply the July 6 Windows Update! Not only does it not fix the local attack vector but it also doesn't fix the remote vector. However, it changes localspl.dll, which makes our patches that DO fix the problem stop applying," tweeted the 0Patch service.
"We've decided not to port our PrintNightmare patches to the localspl.dll version brought by Microsoft's out-of-band update from July 6, but will rather wait for Patch Tuesday that'll hopefully fix the flawed IsLocalFile function, then we'll port our patches to block local attacks"
BleepingComputer has contacted Microsoft about the security update but has not heard back at this time.
Microsoft's incomplete PrintNightmare patch fails to fix vulnerability


.jpg)
3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.