As a consequence of ongoing phishing campaigns using Microsoft OneNote, Microsoft announced that it would harden the application against phishing attacks in early March 2023. Microsoft planned to start the rollout of the security change in April 2023. The company has now published several support documents that provide system administrators and users with additional information.
The main change that Microsoft will introduce changes how 120 high-risk file extensions are handled by the application. OneNote showed a warning to users when they were about to open a high-risk attachment. Users were able to bypass the warning to open the extension.
The OneNote update will block the direct opening of embedded files, if the file extension is on Microsoft's list of dangerous extensions.
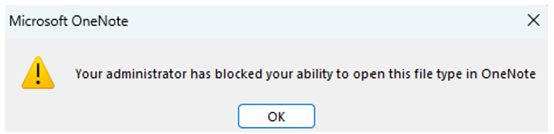
OneNote users see "Your administrator has blocked your ability to open this file type in OneNote". The dialog has just an ok button, and a close window control, but no option anymore to execute the embedded file.
The high risk file extensions match the filter lists of other Microsoft products, including Outlook. The full list is available on this support page. It includes common file extensions such as .exe, .iso or .bat, but also many lesser known file extensions.
Here is the full list of blocked extensions:
.ade .adp .app .application .appref-ms .asp .aspx .asx .bas .bat .bgi .cab .cer .chm .cmd .cnt .com .cpl .crt .csh .der .diagcab .exe .fxp .gadget .grp .hlp .hpj .hta .htc .inf .ins .iso .isp .its .jar .jnlp .js .jse .ksh .lnk .mad .maf .mag .mam .maq .mar .mas .mat .mau .mav .maw .mcf .mda .mdb .mde .mdt .mdw .mdz .msc .msh .msh1 .msh2 .mshxml .msh1xml .msh2xml .msi .msp .mst .msu .ops .osd .pcd .pif .pl .plg .prf .prg .printerexport .ps1 .ps1xml .ps2 .ps2xml .psc1 .psc2 .psd1 .psdm1 .pst .py .pyc .pyo .pyw .pyz .pyzw .reg .scf .scr .sct .shb .shs .theme .tmp .url .vb .vbe .vbp .vbs .vhd .vhdx .vsmacros .vsw .webpnp .website .ws .wsc .wsf .wsh .xbap .xll .xnk
Administrators may add more file extensions to the blocklist. They may use the Block additional file extensions for OLE embedding” policy for that, which is found under User Configuration\Policies\Administrative Templates\Microsoft Office 2016\Security Settings in the Group Policy Management Console.
Another option is to use the Cloud Policy service for Microsoft 365. The policies are only available for Microsoft 365 apps for enterprise, and not for Microsoft Apps for Business. Microsoft notes further that administrators should not use the "Embedded Files Blocked Extensions" policy, but without explanation.
There is also a policy to allow certain blocked file extensions. This is handled by "Allow file extensions for OLE embedding" found under User Configuration\Policies\Administrative Templates\Microsoft Office 2016\Security Settings in the Group Policy Management Console. Changes made to this policy do affect other Microsoft 365 apps, including Word, Excel and PowerPoint.
How to bypass the embedded file block in OneNote
OneNote users can't open high-risk files, based on their extension, anymore directly. Microsoft notes that users may save the embedded files to the local system to execute them there, provided that they trust the sender. Security solutions may block the execution of these saved files, however.
OneNote versions that support the change
The change affects OneNote for Microsoft 365 and OneNote in retail versions of Office. It does not affect OneNote for Mac, Android and iOS, OneNote on the web, OneNote for Windows 10, or OneNote in volume licensed versions of Office.
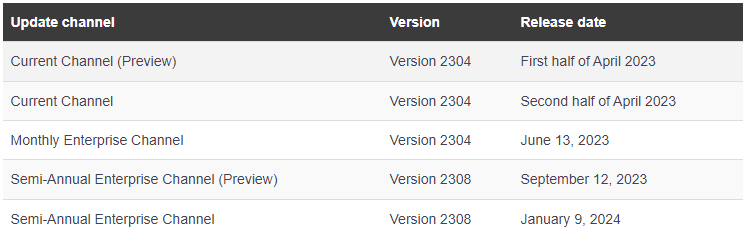
|
|---|
OneNote in retail versions of Office follows the Current Channel release data.



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.