Nobelium, the threat actor behind the SolarWinds compromise in December 2020, has been behind a new wave of attacks that compromised 14 downstream customers of multiple cloud service providers (CSP), managed service providers (MSP), and other IT services organizations, illustrating the adversary's continuing interest in targeting the supply chain via the "compromise-one-to-compromise-many" approach.
Microsoft, which disclosed details of the campaign on Monday, said it notified more than 140 resellers and technology service providers since May. Between July 1 and October 19, 2021, Nobelium is said to have singled out 609 customers, who were collectively attacked a grand total of 22,868 times.
"This recent activity is another indicator that Russia is trying to gain long-term, systematic access to a variety of points in the technology supply chain and establish a mechanism for surveilling – now or in the future – targets of interest to the Russian government," said Tom Burt, Microsoft's corporate vice president of customer security and trust.
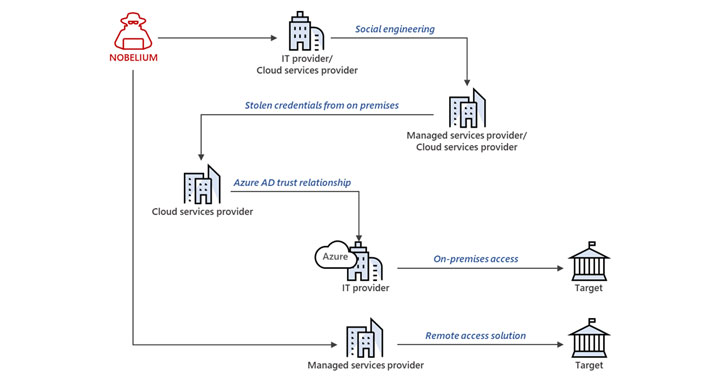
The newly disclosed attacks do not exploit any specific security weaknesses in software but rather leverage a diverse range of techniques such as password spraying, token theft, API abuse, and spear-phishing to siphon credentials associated with privileged accounts of service providers, enabling the attackers to move laterally in cloud environments and mount further intrusions.
The goal, according to Microsoft, appears that "Nobelium ultimately hopes to piggyback on any direct access that resellers may have to their customers' IT systems and more easily impersonate an organization's trusted technology partner to gain access to their downstream customers."
If anything, the attacks are yet another manifestation of Nobelium's oft-repeated tactics, which has been found abusing trust relationships enjoyed by service providers to burrow into multiple victims of interest for intelligence gain. As mitigations, the company is recommending companies to enable multi-factor authentication (MFA) and audit delegated administrative privileges (DAP) to prevent any potential misuse of elevated permissions.
The development also arrives less than a month after the tech giant revealed a new passive and highly targeted backdoor dubbed "FoggyWeb" deployed by the hacking group to deliver additional payloads and steal sensitive information from Active Directory Federation Services (AD FS) servers.
- Karlston
-

 1
1


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.