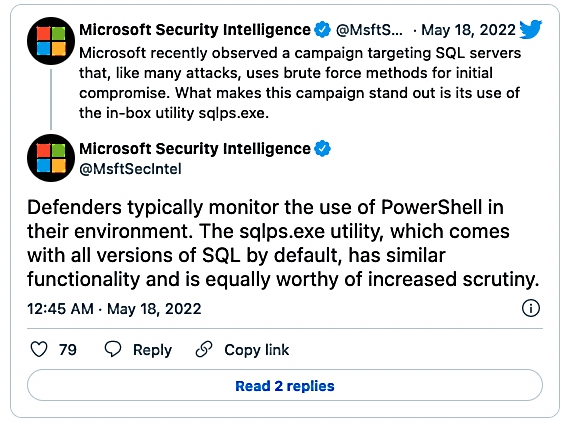
Microsoft warned of brute-forcing attacks targeting Internet-exposed and poorly secured Microsoft SQL Server (MSSQL) database servers using weak passwords.
While this isn't necessarily the first time MSSQL servers have been targeted in such attacks, Redmond says that the threat actors behind this recently observed campaign are using the legitimate sqlps.exe tool as a LOLBin (short for living-off-the-land binary).
"The attackers achieve fileless persistence by spawning the sqlps.exe utility, a PowerShell wrapper for running SQL-built cmdlets, to run recon commands and change the start mode of the SQL service to LocalSystem," the Microsoft Security Intelligence team revealed.
"The attackers also use sqlps.exe to create a new account that they add to the sysadmin role, enabling them to take full control of the SQL server. They then gain the ability to perform other actions, including deploying payloads like coin miners."
Using sqlps, a utility that comes included with the Microsoft SQL Server and allows loading SQL Server cmdlets, as a LOLBin, enables the attackers to execute PowerShell commands without worrying about defenders detecting their malicious actions.
It also helps ensure that they don't leave any traces to be found while analyzing their attacks since using sqlps is an effective way to bypass Script Block Logging, a PowerShell capability that would otherwise log cmdlet operations to the Windows event log.
Similar attacks against MSSQL servers were reported in March when they were targeted to deploy Gh0stCringe (aka CirenegRAT) remote access trojans (RATs).
In a previous campaign from February, threat actors compromised MSSQL servers to drop Cobalt Strike beacons using the Microsoft SQL xp_cmdshell command.
However, for years, MSSQL servers have been targeted as part of massive campaigns where malicious actors attempt to hijack thousands of vulnerable servers daily for various end goals.
In one such series of attacks (dubbed Vollgar) spanning almost two years, threat actors backdoored between 2,000 and 3,000 servers with RATs after brute-forcing publicly exposed servers to deploy Monero (XMR) and Vollar (VDS) cryptominers.
To defend their MSSQL servers against such attacks, admins are advised not to expose them to the Interne, use a strong admin password that can't be guessed or brute-forced, and place the server behind a firewall.
Admins are advised not to expose them to the Internet to defend their MSSQL servers against such attacks.
You should also:
- use a strong admin password that can't be guessed or brute-forced easily and place the server behind a firewall
- enable logging to monitor for suspicious or unexpected activity or recurring login attempts
- apply the latest security updates to decrease the attack surface and block attacks leveraging exploits that target known vulnerabilities
Microsoft warns of brute-force attacks targeting MSSQL servers
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.