Security analysts have found a severe security vulnerability in the desktop app for Microsoft Teams that gives threat actors access to authentication tokens and accounts with multi-factor authentication (MFA) turned on.
Microsoft Teams is a communication platform, included in the 365 product family, used by more than 270 million people for exchanging text messages, videoconferencing, and storing files.
The newly discovered security issue impacts versions of the application for Windows, Linux, and Mac and refers to Microsoft Teams storing user authentication tokens in clear text without protecting access to them.
An attacker with local access on a system where Microsoft Teams is installed could steal the tokens and use them to log into the victim's account.
"This attack does not require special permissions or advanced malware to get away with major internal damage," Connor Peoples at cybersecurity company Vectra explains in a report this week.
The researcher adds that by taking "control of critical seats–like a company's Head of Engineering, CEO, or CFO—attackers can convince users to perform tasks damaging to the organization."
Vectra researchers discovered the problem in August 2022 and reported it to Microsoft. However, Microsoft did not agree on the severity of the issue and said that it doesn't meet the criteria for patching.
Problem details
Microsoft Teams is an Electron app, meaning that it runs in a browser window, complete with all the elements required by a regular web page (cookies, session strings, logs, etc.).
Electron does not support encryption or protected file locations by default, so while the software framework is versatile and easy to use, it is not considered secure enough for developing mission-critical products unless extensive customization and additional work is applied.
Vectra analyzed Microsoft Teams while trying to find a way to remove deactivated accounts from client apps, and found an ldb file with access tokens in clear text.
"Upon review, it was determined that these access tokens were active and not an accidental dump of a previous error. These access tokens gave us access to the Outlook and Skype APIs." - Vectra
Additionally, the analysts discovered that the "Cookies" folder also contained valid authentication tokens, along with account information, session data, and marketing tags.
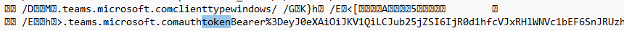
Finally, Vectra developed an exploit by abusing an API call that allows sending messages to oneself. Using SQLite engine to read the Cookies database, the researchers received the authentication tokens as a message in their chat window.
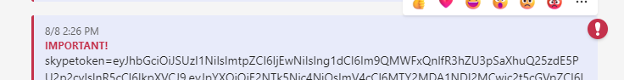
The biggest concern is that this flaw will be abused by information-stealing malware that have become one of the most commonly distributed paylods in phishing campaigns.
Using this type of malware, threat actors will be able to steal Microsoft Teams authentication tokens and remotely login as the user, bypassing MFA and gaining full access to the account.
Information stealers are already doing this for other applications, such as Google Chrome, Microsoft Edge, Mozilla Firefox, Discord, and many more.
Risk mitigation
With a patch unlikely to be released, Vectra's recommendation is for users to switch to the browser version of the Microsoft Teams client. By using Microsoft Edge to load the app, users benefit from additional protections against token leaks.
The researchers advise Linux users to move to a different collaboaration suite, especially since Microsoft announced plans to stop supporting the app for the platform by December.
For those that can't move to a different solution immediately, they can create a monitoring rule to discover processes accessing the following directories:
- [Windows] %AppData%\Microsoft\Teams\Cookies
- [Windows] %AppData%\Microsoft\Teams\Local Storage\leveldb
- [macOS] ~/Library/Application Support/Microsoft/Teams/Cookies
- [macOS] ~/Library/Application Support/Microsoft/Teams/Local Storage/leveldb
- [Linux] ~/.config/Microsoft/Microsoft Teams/Cookies
- [Linux] ~/.config/Microsoft/Microsoft Teams/Local Storage/leveldb
BleepingComputer has contacted Microsoft about the company's plans to release a fix for the issue and will update the article when we get an answer.
Update 9/14/22 - A Microsoft spokesperson sent us the following comment regarding Vectra's findings:
The technique described does not meet our bar for immediate servicing as it requires an attacker to first gain access to a target network.
We appreciate Vectra Protect’s partnership in identifying and responsibly disclosing this issue and will consider addressing in a future product release.
Source: Bleeping Computer
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.