Microsoft has revoked several Microsoft hardware developer accounts after drivers signed through their profiles were used in cyberattacks, including ransomware incidents.
The news comes in a coordinated disclosure between Microsoft, Mandiant, Sophos, and SentinelOne. The researchers explain that threat actors are utilizing malicious kernel-mode hardware drivers whose trust was verified with Authenticode signatures from Microsoft's Windows Hardware Developer Program.
"Microsoft was informed that drivers certified by Microsoft's Windows Hardware Developer Program were being used maliciously in post-exploitation activity. In these attacks, the attacker had already gained administrative privileges on compromised systems prior to use of the drivers," explains the advisory from Microsoft.
"We were notified of this activity by SentinelOne, Mandiant, and Sophos on October 19, 2022, and subsequently performed an investigation into this activity."
"This investigation revealed that several developer accounts for the Microsoft Partner Center were engaged in submitting malicious drivers to obtain a Microsoft signature."
"A new attempt at submitting a malicious driver for signing on September 29th, 2022, led to the suspension of the sellers' accounts in early October."
Signing kernel-mode drivers
When kernel-mode hardware drivers are loaded in Windows, they gain the highest privilege level on the operating system.
These privileges could allow a driver to perform various malicious tasks not usually permitted to user-mode applications. The actions include terminating security software, deleting protected files, and acting as rootkits to hide other processes.
Since Windows 10, Microsoft has required kernel-mode hardware drivers to be signed via Microsoft's Windows Hardware Developer Program.
As developers need to purchase an extended validation (EV) certificate, go through an identification process, and have submitted drivers vetted by Microsoft, many security platforms automatically trust code signed by Microsoft through this program.
For this reason, the ability to sign a kernel-mode driver by Microsoft to use it in malicious campaigns is a precious commodity.
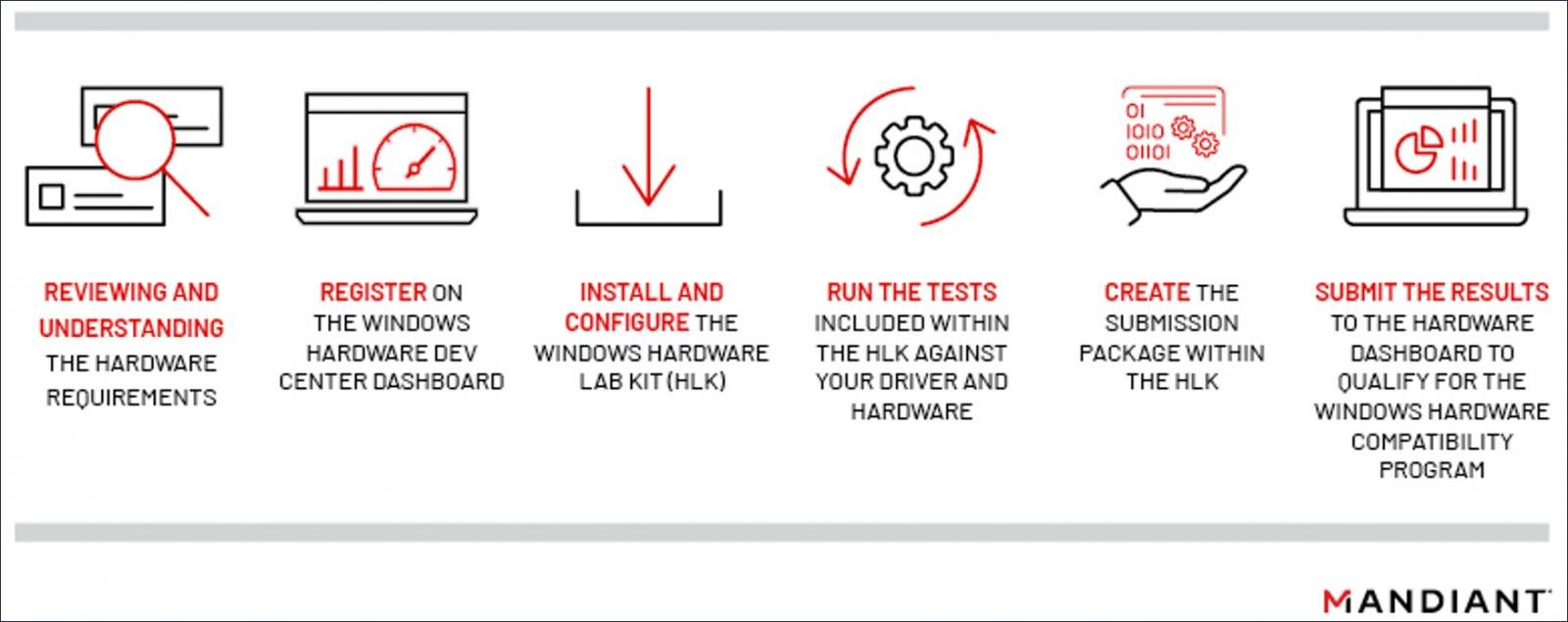
Signing a driver via the Windows Hardware Compatibility Program
Source: Mandiant
Toolkit used to terminate security software
In reports released today, researchers explain how they found a new toolkit consisting of two components named STONESTOP (loader) and POORTRY (kernel-mode driver) being used in "bring your own vulnerable driver" (BYOVD) attacks.
According to Mandiant and SentinelOne, STONESTOP is a user-mode application that attempts to terminate endpoint security software processes on a device. Another variant includes the ability to overwrite and delete files.
As security software processes are usually protected against tampering by regular applications, STONESTOP loads the POORTRY kernel-mode driver signed by Microsoft to terminate the associated protected processes or Windows services.
"STONESTOP functions as both a loader/installer for POORTRY, as well as an orchestrator to instruct the driver with what actions to perform," explains the SentinelLabs report.
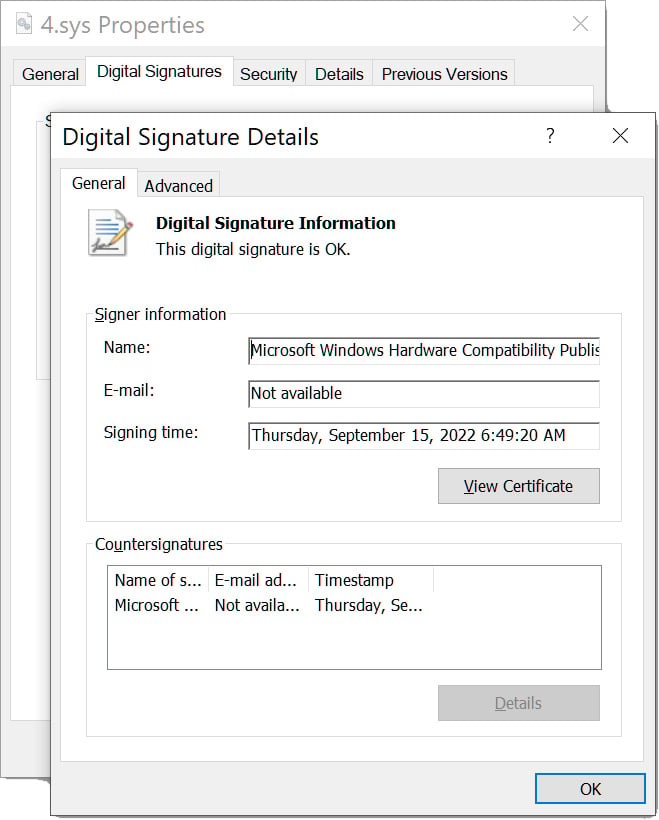
POORTRY driver signed by Microsoft
Source: BleepingComputer
Linked to ransomware and SIM swappers
The three companies have seen the toolkit used by different threat actors.
Sophos' Rapid Response team ended an attack in an incident response engagement before hackers could distribute the final payload.
However, Sophos has attributed this attack with 'high confidence' to the Cuba ransomware operation, which previously used a variant of this malware.
"In incidents investigated by Sophos, threat actors tied to Cuba ransomware used the BURNTCIGAR loader utility to install a malicious driver signed using Microsoft's certificate," explains Sophos.
SentinelOne has also seen this Microsoft-signed toolkit used in attacks against telecommunication, BPO, MSSP, and financial services businesses. In one case, they saw it used by the Hive Ransomware operation against a company in the medical industry.
"Notably, SentinelLabs observed a separate threat actor also utilizing a similar Microsoft signed driver, which resulted in the deployment of Hive ransomware against a target in the medical industry, indicating a broader use of this technique by various actors with access to similar tooling," explained the SentinelLabs researchers.
Mandiant, on the other hand, saw a threat actor identified as UNC3944 utilizing the toolkit in attacks as early as August 2022, who is known for SIM swapping attacks.
"Mandiant has observed UNC3944 utilizing malware that has been signed via the attestation signing process. UNC3944 is a financially motivated threat group that has been active since at least May 2022 and commonly gains initial network access using stolen credentials obtained from SMS phishing operations," detailed Mandiant's report.
As numerous threat clusters are using the signed drivers, it is unclear how they all gained access to similar Microsoft-signed toolkits for use in attacks.
Both Mandiant and SentinelOne believe the toolkit, or at least the code-signing, is coming from a supplier or a service that other threat actors pay to access.
Mandiant says they could extract the following organization names used to sign the driver submissions to Microsoft.
Qi Lijun
Luck Bigger Technology Co., Ltd
XinSing Network Service Co., Ltd
Hangzhou Shunwang Technology Co.,Ltd
Fuzhou Superman
Beijing Hongdao Changxing International Trade Co., Ltd.
Fujian Altron Interactive Entertainment Technology Co., Ltd.
Xiamen Hengxin Excellence Network Technology Co., Ltd.
Dalian Zongmeng Network Technology Co., Ltd.
Microsoft's reponse
Microsoft has released security updates to revoke the certificates used by malicious files and has already suspended the accounts used to submit the drivers to be signed.
New Microsoft Defender signatures (1.377.987.0) have also been released to detect legitimate signed drivers in post-exploitation attacks.
"Microsoft is working with Microsoft Active Protections Program (MAPP) partners to help develop further detections and to better protect our shared customers," explained Microsoft.
"Microsoft Partner Center is also working on long-term solutions to address these deceptive practices and prevent future customer impacts."
However, Microsoft has yet to share how the malicious drivers passed the review process in the first place.
BleepingComputer has reached out to Microsoft with further questions about the advisory and review proccess but Microsoft said they had nothing further to share.
Edited by Karlston




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.