Microsoft has discovered a new malware used by the Russian hacker group APT29 (a.k.a. NOBELIUM, Cozy Bear) that enables authentication as anyone in a compromised network.
As a state-sponsored cyberespionage actor, APT29 employs the new capability to hide their presence on the networks of their targets, typically government and critical organizations across Europe, the U.S., and Asia.
Dubbed ‘MagicWeb’, the new malicious tool is an evolution of ‘FoggyWeb’, which allowed hackers to exfiltrate the configuration database of compromised Active Directory Federation Services (ADFS) servers, decrypt token-signing and token-decryption certificates, and fetch additional payloads from the command and control (C2) server.
AD FS relies on claims-based authentication to validate the identity of the user and their authorization claims. These claims are packaged into a token that can be used for authentication. MagicWeb injects itself into the claims process to perform malicious actions outside the normal roles of an AD FS server.
The MagicWeb’ tool replaces a legitimate DLL used by ADFS with a malicious version to manipulate user authentication certificates and to modify claims passed in tokens generated by the compromised server.
Because ADFS servers facilitate user authentication, MagicWeb can help APT29 validate authentication for any user account on that server, giving them persistence and an abundance of pivoting opportunities.
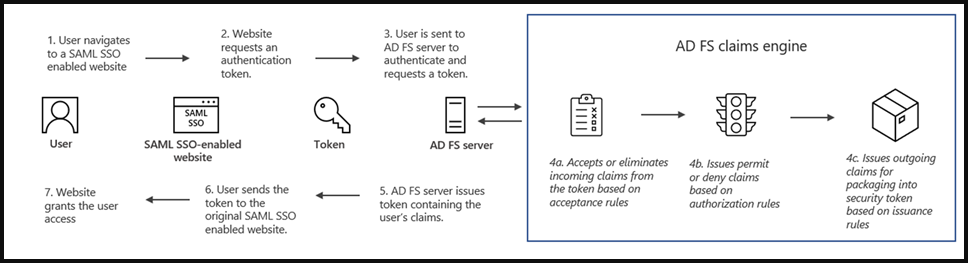
MagicWeb requires APT29 to first gain admin access to the target ADFS server and replace the said DLL with their version, but Microsoft reports that this has already happened in at least one case its Detection and Response Team (DART) team was called to investigate.
MagicWeb details
Microsoft observed NOBELIUM replace the “Microsoft.IdentityServer.Diagnostics.dll” with a backdoored version that features an additional section in the ‘TraceLog’ class.
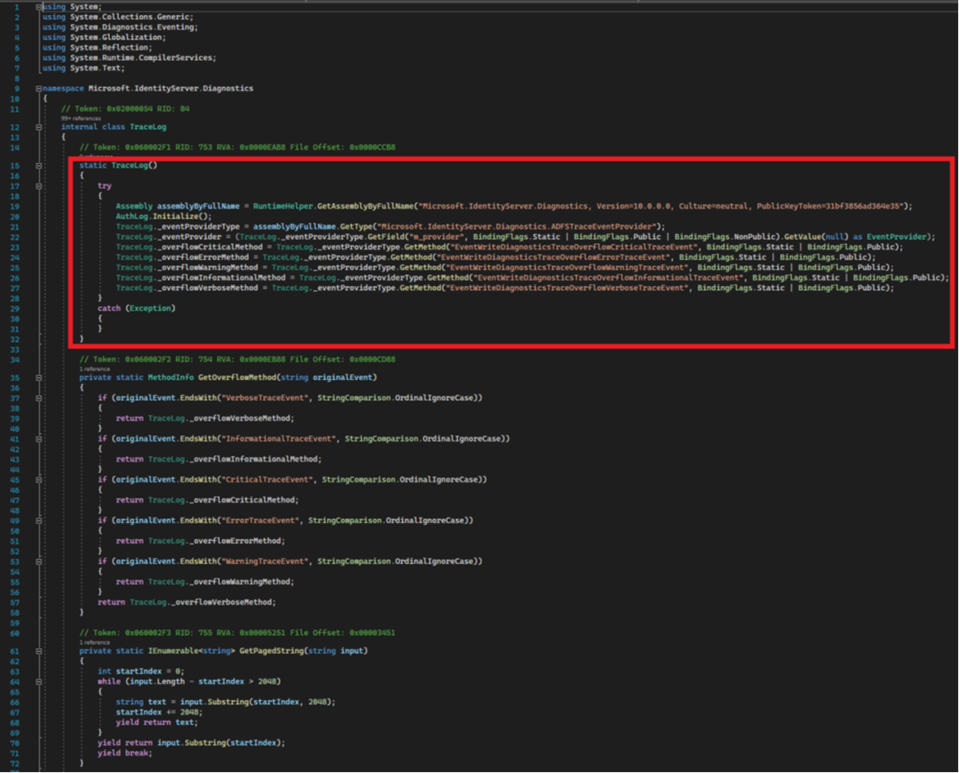
This new section is a static constructor executed once during the loading of the DLL when launching the ADFS server.
The goal of the constructor is to hook four legitimate ADFS functions, namely “Build”, “GetClientCertificate”, “EndpointConfiguration”, and “ProcessClaims”.
The hooked functions enable the Russian hackers to perform the following actions:
- BeginBuild() - Subvert the normal certificate inspection/build process by introducing a custom method before invoked before “Build()”.
- BeginGetClientCertificate() - Force the application to accept a non-valid client certificate as valid, as long as the OID value matches either of the hardcoded MD5 values in MagicWeb.
- BeginEndpointConfiguration() - Allow WAP to pass the request with the specific malicious certificate to ADFS for further authentication processing.
- BeginProcessClaims() - Ensure that fraudulent claims with the MagicWeb OID value are added to the list of claims returned to the caller of the legitimate hooked method (ProcessClaims).
Hunting for MagicWeb
Microsoft recommends defenders to follow the hunting guidance provided in the report. Indicators of compromise (IoCs) have not been shared as they wouldn’t be very helpful.
NOBELIUM frequently customizes infrastructure and capabilities per campaign, minimizing operational risk should their campaign-specific attributes be discovered.
“If MagicWeb is identified in your environment, it’s unlikely to match any static IOCs from other targets such as an SHA-256 value,” the company adds.
Additionally, searching for unsigned DLLs in GAC (Global Assembly Cache) using Microsoft 365 Defender or enumerating non-Microsoft signed DLLs in GAC via PowerShell, could help unearth malicious library replacements.
Source: BleepingComputer
- aum
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.