Security researchers at WithSecure, previously F-Secure Business, found that it is possible to partially or fully infer the contents of encrypted messages sent through Microsoft Office 365 due to the use of a weak block cipher mode of operation.
Organizations use Office 365 Message Encryption to send or receive emails, both external and internal, to ensure confidentiality of the content from destination to source.
However, the feature encrypts the data using the Electronic Code Book (ECB) mode, which allows inferring the plaintext message under certain conditions.
ECB mode issue
The main problem with ECB is that repetitive areas in the plaintext data have the same encrypted result when the same key is used, thus creating a pattern.
The issue was highlighted after the massive Adobe data breach in 2013 when tens of millions of passwords were leaked and researchers discovered that the company used ECB mode to encrypt the data, making it possible to obtain plaintext passwords.
This weakness was highlighted again in 2020 when it was discovered that the widely used teleconference application Zoom used the same 128-bit key to encrypt all audio and video using the AES algorithm with ECB mode.
Harry Sintonen of WithSecure underlines that with Office 365 Message Encryption the content of the encrypted messages isn’t directly decipherable, but structural information about those messages can be captured.
An attacker able to collect multiple encrypted messages can look for patterns that could lead to parts of the message to become gradually readable without the need of an encryption key.
“More emails make this process easier and more accurate, so it’s something attackers can perform after getting their hands on email archives stolen during a data breach, or by breaking into someone’s email account, email server or gaining access to backups,” - Harry Sintonen
The researcher explains that a large database of messages allows inferring the entire content or just parts of it by looking at the relative locations of the repeated sections.
To demonstrate that this can be achieved, Sintonen revealed the content of an image protected by Office 365 Message Encryption.
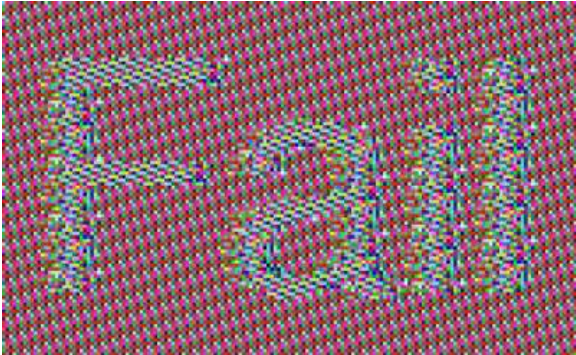
No solution yet
Threat actors can analyze stolen encrypted messages offline, since organizations have no way to prevent this for already sent messages. Sintonen notes that the use of rights management feature does not mitigate the issue.
The researcher reported this finding to Microsoft in January 2022. The tech giant acknowledged the problem and paid a bug bounty but did not release a fix.
After repeated subsequent queries about the status of the vulnerability, Microsoft told WithSecure that “the issue does not meet the bar for security servicing, nor is it considered a breach,” and hence there will be no patch for it.
BleepingComputer also reached out to Microsoft about this and a company spokesperson said that "rights management feature is intended as a tool to prevent accidental misuse and is not a security boundary."
"To help prevent abuse we recommend customers follow best security practices, including keeping systems up to date, enabling multi-factor authentication, and using a real time anti-malware product" - Microsoft
The reason Microsoft still uses the ECB implementation is support for legacy applications. However, the company is working on adding an alternative encryption protocol to future product versions.
WithSecure recommends that until a more secure mode of operation becomes available, users and admins should stop using or trusting the Office 365 Message Encryption feature.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.