Microsoft says the North Korean-sponsored Lazarus threat group is trojanizing legitimate open-source software and using it to backdoor organizations in many industry sectors, such as technology, defense, and media entertainment.
The list of open-source software weaponized by Lazarus state hackers to deploy the BLINDINGCAN (aka ZetaNile) backdoor includes PuTTY, KiTTY, TightVNC, Sumatra PDF Reader, and the muPDF/Subliminal Recording software installer.
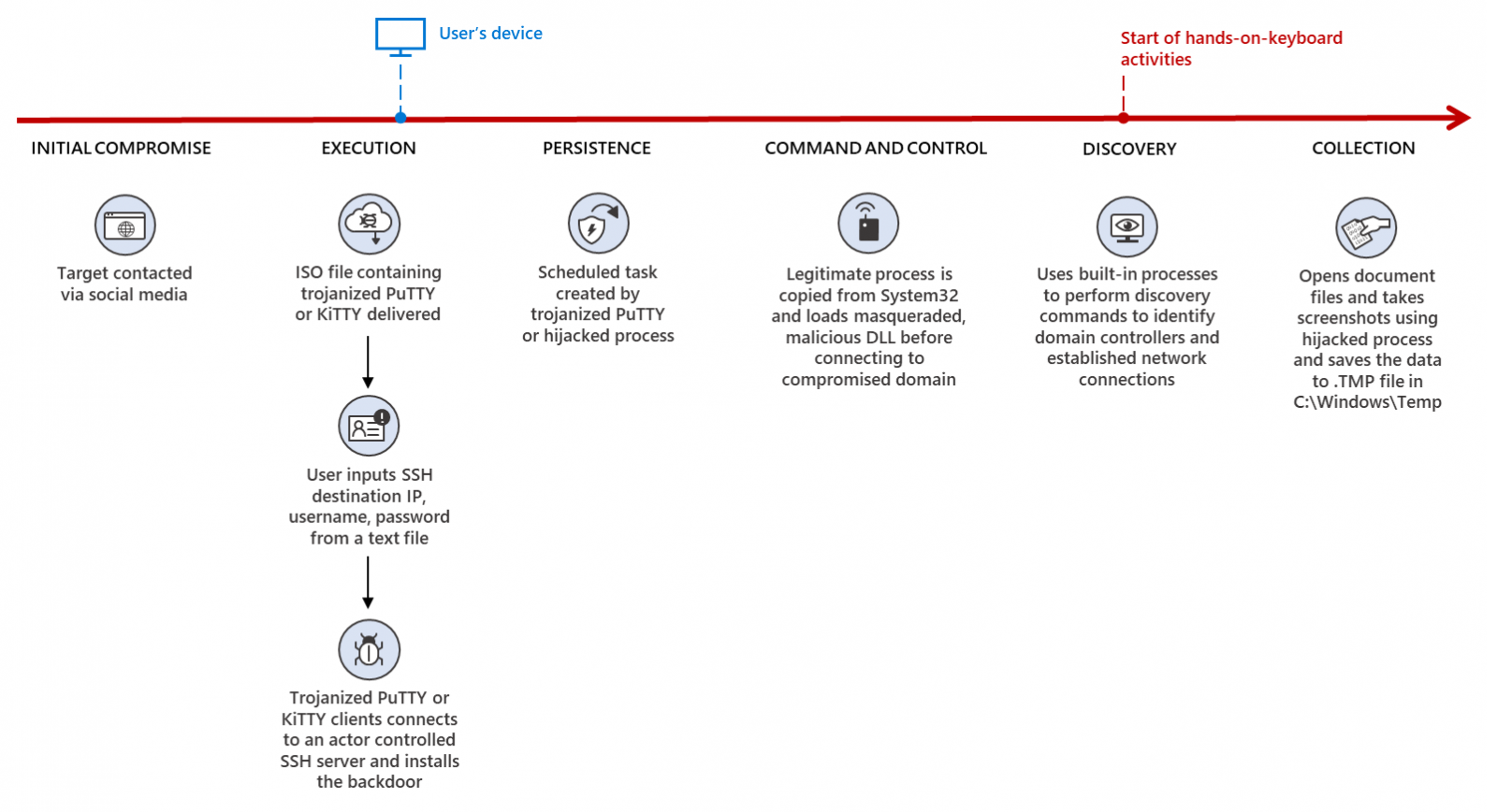
The PuTTY and KiTTY SSH clients were also used to backdoor targets' devices in fake job skills assessments, as reported by Mandiant this month.
This trojanized software was used in social engineering attacks from late April to mid-September 2022 and primarily focused on engineers and technical support professionals working at IT and media organizations in the UK, India, and the U.S.
The attackers created "fake profiles claiming to be recruiters working at technology, defense, and media entertainment companies, with the goal of moving targets away from LinkedIn and to the encrypted messaging app WhatsApp for the delivery of malware," Microsoft said.
"Targets received outreach tailored to their profession or background and were encouraged to apply for an open position at one of several legitimate companies."
After the targets were tricked into downloading the weaponized software to deploy the malware on their systems, the Lazarus operators used the backdoor for lateral movement and network discovery, with the end goal of stealing sensitive info.
Recent ZINC campaign (Microsoft)
Mandiant said in its report that the group's latest activities seem to be a continuation of Operation Dream Job, a North Korean cyber-espionage campaign active since June 2020 when it lured targets from prominent defense and aerospace companies in the U.S. with fake job offers.
The Lazarus Group (also tracked as ZINC, Labyrinth Chollima, and Black Artemis) is a North-Korean military hacking group active since at least 2009.
It gained notoriety after hacking Sony Films in Operation Blockbuster, multiple banks worldwide, and for coordinating the 2017 global WannaCry ransomware campaign.
More recently, Lazarus targeted security researchers in social engineering attacks using elaborate fake "security researcher" social media personas in January and in a similar campaign in March.
They also used the ThreatNeedle backdoor in a large-scale cyber-espionage campaign against the defense industry of over a dozen countries.
The U.S. government sanctioned three DPRK-sponsored hacking groups (Lazarus, Bluenoroff, and Andariel) in September 2019 and now offers a reward of up to $5 million for information on North Korean hackers' cyber activity.
- Karlston and aum
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.