Microsoft says that cryptocurrency investment companies have been targeted by a threat group it tracks as DEV-0139 via Telegram groups used to communicate with the firms' VIP customers.
"Microsoft recently investigated an attack where the threat actor, tracked as DEV-0139, took advantage of Telegram chat groups to target cryptocurrency investment companies," the company's Security Threat Intelligence team revealed.
"DEV-0139 joined Telegram groups used to facilitate communication between VIP clients and cryptocurrency exchange platforms and identified their target from among the members."
On October 19, attackers with broad knowledge of the crypto investment industry invited at least one target (posing as representatives of other crypto asset management firms) to another Telegram group, where they asked for feedback on cryptocurrency exchange platforms' fee structure.
After gaining their targets' trust, the threat actors sent them malicious Excel spreadsheets named "OKX Binance & Huobi VIP fee comparision.xls" with a data comparison (likely accurate to increase credibility) between the VIP fee structures of crypto exchange companies.
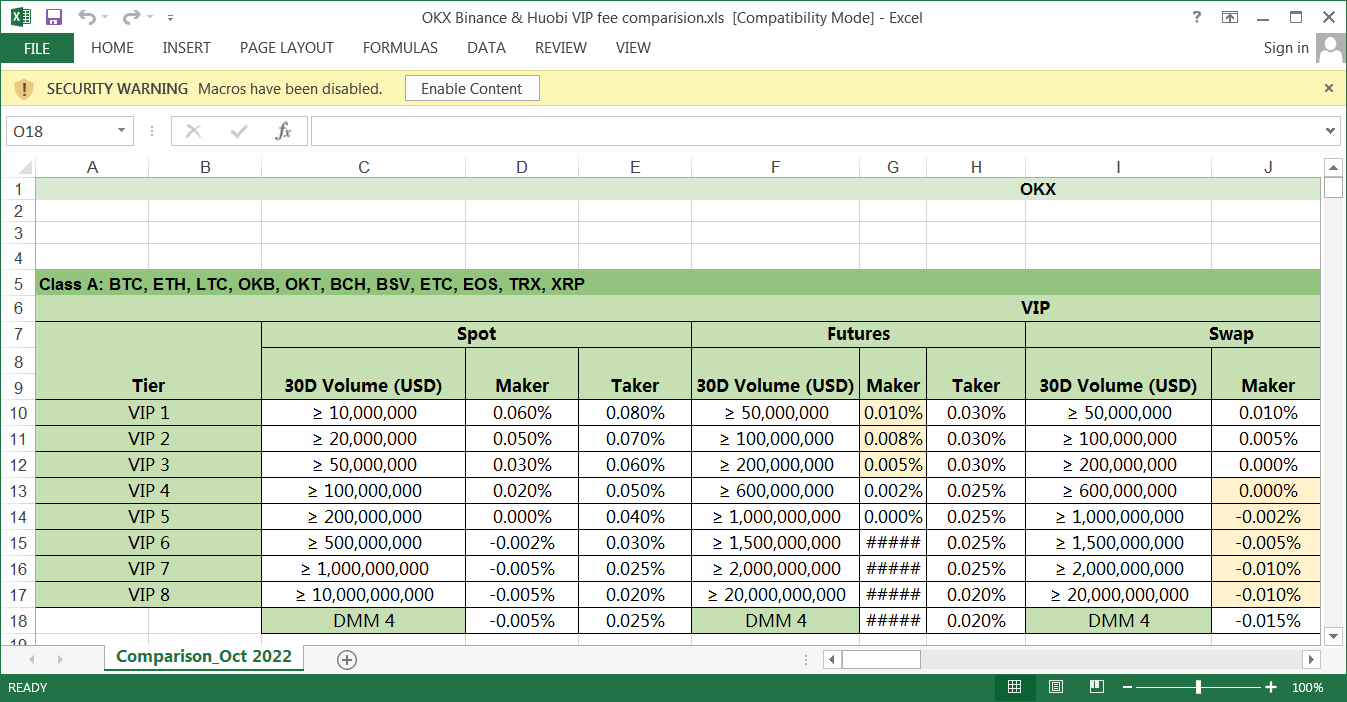
Malicious Excel sheet (BleepingComputer)
Once the victim opens the document and enables macros, a second worksheet embedded in the file will download and parse a PNG file to extract a malicious DLL, an XOR-encoded backdoor, and a legitimate Windows executable later used to sideload the DLL.
This DLL will decrypt and load the backdoor, providing the attackers with remote access to the victim's compromised system.
"The main sheet in the Excel file is protected with the password dragon to encourage the target to enable the macros," Microsoft explained.
"The sheet is then unprotected after installing and running the other Excel file stored in Base64. This is likely used to trick the user to enable macros and not raise suspicion."
DEV-0139 has also delivered a second payload as part of this campaign, an MSI package for a CryptoDashboardV2 app, suggesting that they're also behind other attacks using the same technique to push custom payloads.
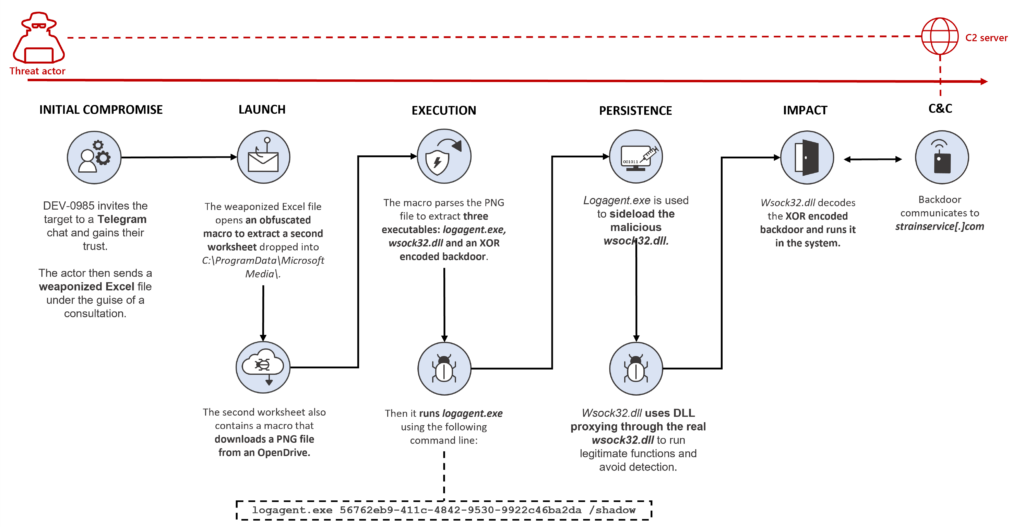
Attack overview (Microsoft)
While Microsoft has not attributed this attack to a specific group and instead chose to link it to the DEV-0139 cluster of threat activity, threat intelligence firm Volexity has also published its own findings on this attack over the weekend, connecting it to the North Korean Lazarus threat group.
According to Volexity, the North Korean hackers used the malicious crypto-exchange fee comparison spreadsheet to drop the AppleJeus malware Lazarus has previously used in cryptocurrency hijacking and digital asset theft operations.
Volexity also observed Lazarus using a website clone for the HaasOnline automated cryptocurrency trading platform to distribute a trojanized BloxHolder app which would instead deploy AppleJeus malware bundled within the QTBitcoinTrader app.
Microsoft says it notified customers who have been compromised or targeted in these attacks and shared the information needed to secure their accounts.
The Lazarus Group is a hacking group operating out of North Korea that has been active for over a decade, since at least 2009.
Its operatives are known for attacks on high-profile targets worldwide, including banks, media organizations, and government agencies.
The group is thought to be responsible for high-profile cyber attacks, including the 2014 Sony Pictures hack and the WannaCry ransomware attack of 2017.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.