Microsoft has recently addressed a weakness in the Microsoft Defender Antivirus on Windows that allowed attackers to plant and execute malicious payloads without triggering Defender's malware detection engine.
This security flaw [1, 2] affected the latest Windows 10 versions, and threat attackers could abuse it since at least 2014.
As BleepingComputer previously reported, the flaw resulted from lax security settings for the "HKLM\Software\Microsoft\Windows Defender\Exclusions" Registry key. This key contains the list of locations (files, folders, extensions, or processes) excluded from Microsoft Defender scanning.
Exploiting the weakness was possible because the Registry key was accessible by the 'Everyone' group, as shown in the image below.
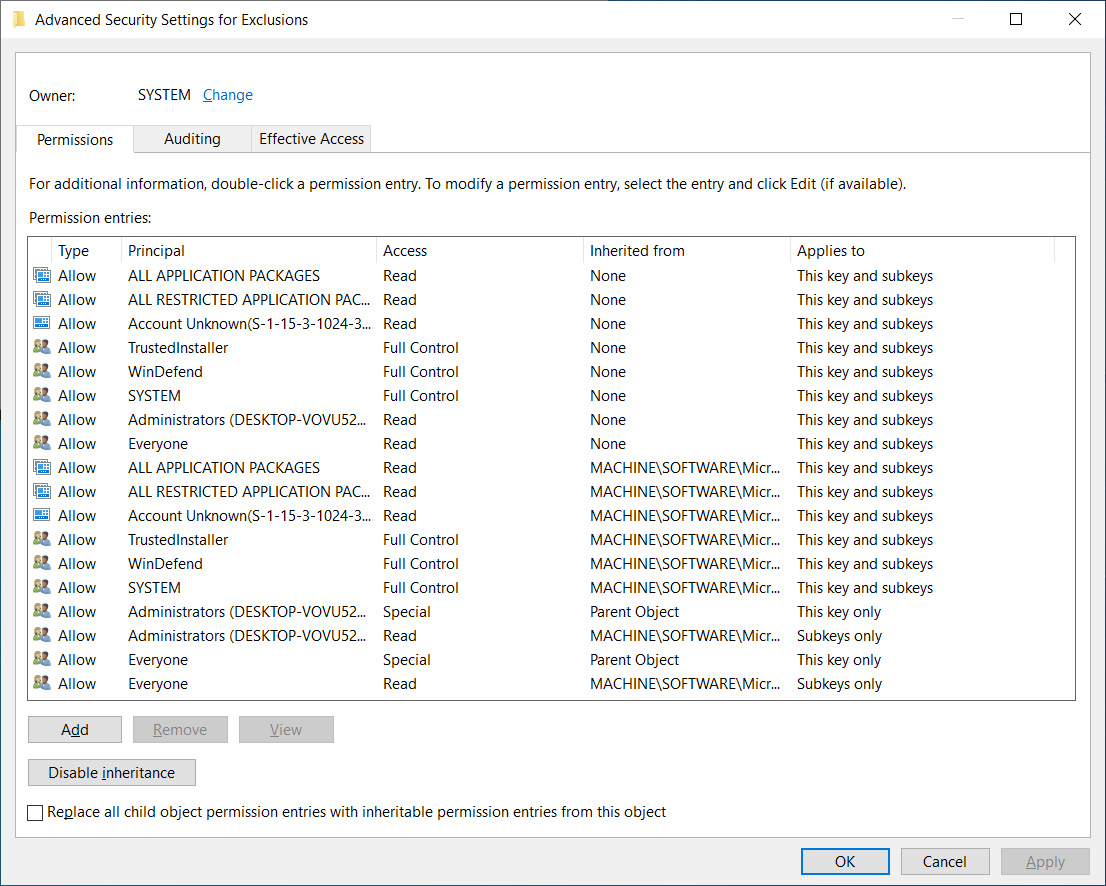
Source: BleepingComputer
This made it possible for local users (regardless of their permissions) to access it via the command line by querying the Windows Registry.
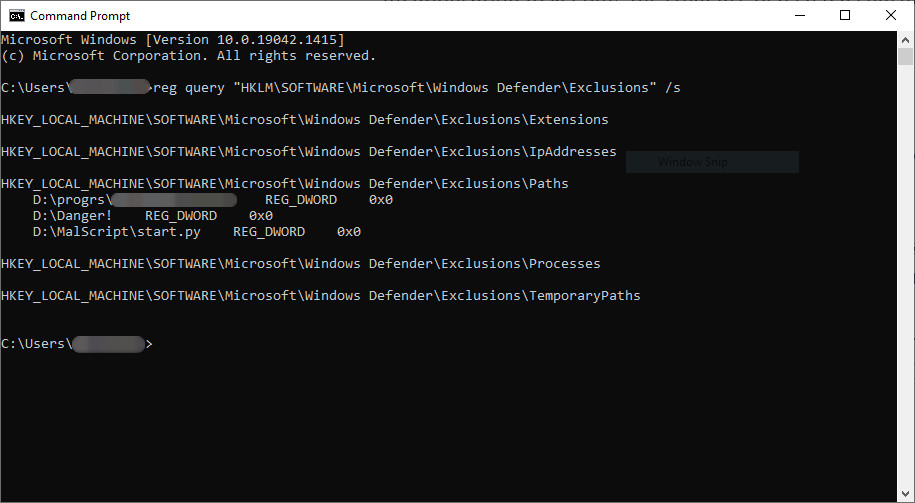
Security expert Nathan McNulty also warned that users could also grab the list of exclusions from registry trees with entries storing Group Policy settings, which is much more sensitive info as it provides exclusions for multiple computers on a Windows domain.
After finding out what folders were added to the antivirus exclusion list, attackers could deliver and execute malware from an excluded folder on a compromised Windows system without having to fear that its malicious payload will be detected and neutralized.
By exploiting this weakness, BleepingComputer could execute a sample of Conti ransomware from an excluded folder and encrypt a Windows system without any warnings or signs of detection from Microsoft Defender.
Security weakness addressed silently by Microsoft
This is no longer be possible given Microsoft has now addressed the weakness via a silent update, as spotted by Dutch security expert SecGuru_OTX on Thursday.
SentinelOne threat researcher Antonio Cocomazzi confirmed that the flaw can no longer be used on Windows 10 20H2 systems after installing the February 2022 Patch Tuesday Windows updates.
Some users are seeing the new permission change after installing the February 2022 Patch Tuesday Windows cumulative updates.
On the other hand, Will Dormann, a vulnerability analyst for CERT/CC, noted that he received the permissions change without installing any updates, indicating that the change could be added by both Windows updates and Microsoft Defender security intelligence updates.
As BleepingComputer was also able to confirm today, the permissions on Windows advanced security settings for Defender exclusions have indeed been updated, with the 'Everyone' group removed from the Registry key's permissions.
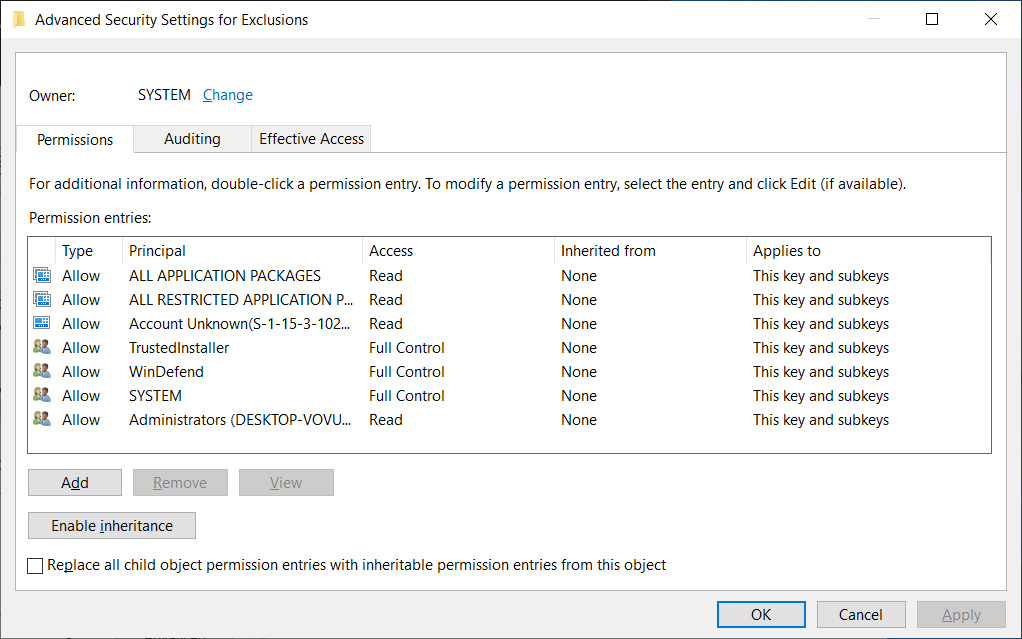
Source: BleepingComputer
On Windows 10 systems where this change has already rolled out, users are now required to have admin privileges to be able to access the list of exclusions via the command line or when adding them using the Windows Security settings screen.
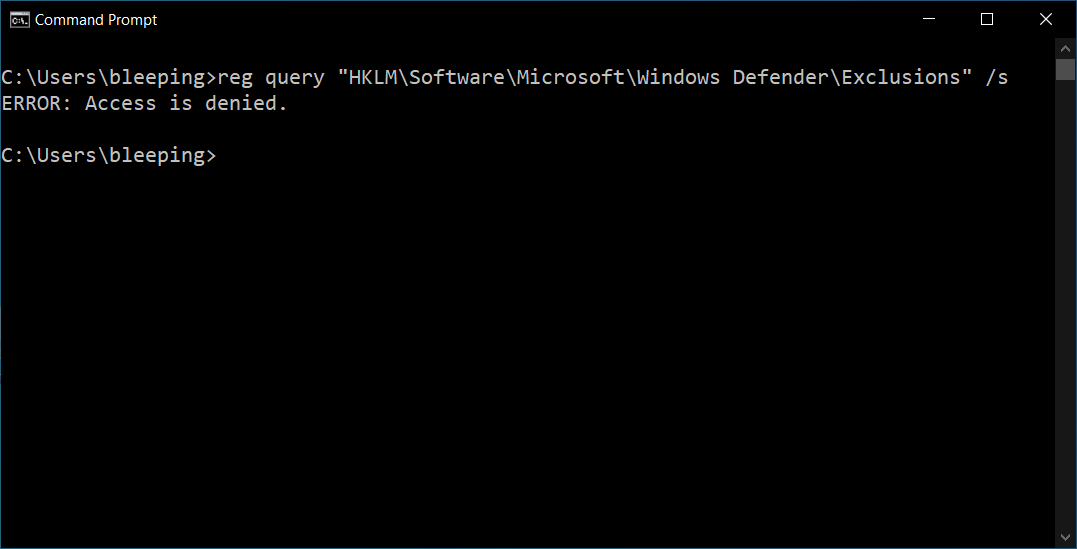
The change rolled out since our previous report, but, at the moment, only Microsoft knows how it was pushed to affected Windows 10 systems (via Windows updates, Defender intelligence updates, or other means).
A Microsoft spokesperson was not available for comment when contacted by BleepingComputer earlier today.
Microsoft fixes Defender flaw letting hackers bypass antivirus scans
- DKT27 and aum
-

 2
2



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.