Microsoft has shared mitigations for two new Microsoft Exchange zero-day vulnerabilities tracked as CVE-2022-41040 and CVE-2022-41082, but researchers warn that the mitigation for on-premise servers is far from enough.
Threat actors are already chaining both of these zero-day bugs in active attacks to breach Microsoft Exchange servers and achieve remote code execution.
Both security flaws were reported privately through the Zero Day Initiative program about three weeks ago by Vietnamese cybersecurity company GTSC, who shared the details publicly last week.
Mitigation too specific
Microsoft confirmed the two issues on Friday and said that they were “aware of limited targeted attacks” exploiting them.
As part of an advisory, Microsoft shared mitigations for on-premise servers and a strong recommendation for Exchange Server customers to “disable remote PowerShell access for non-admin users” in the organization."
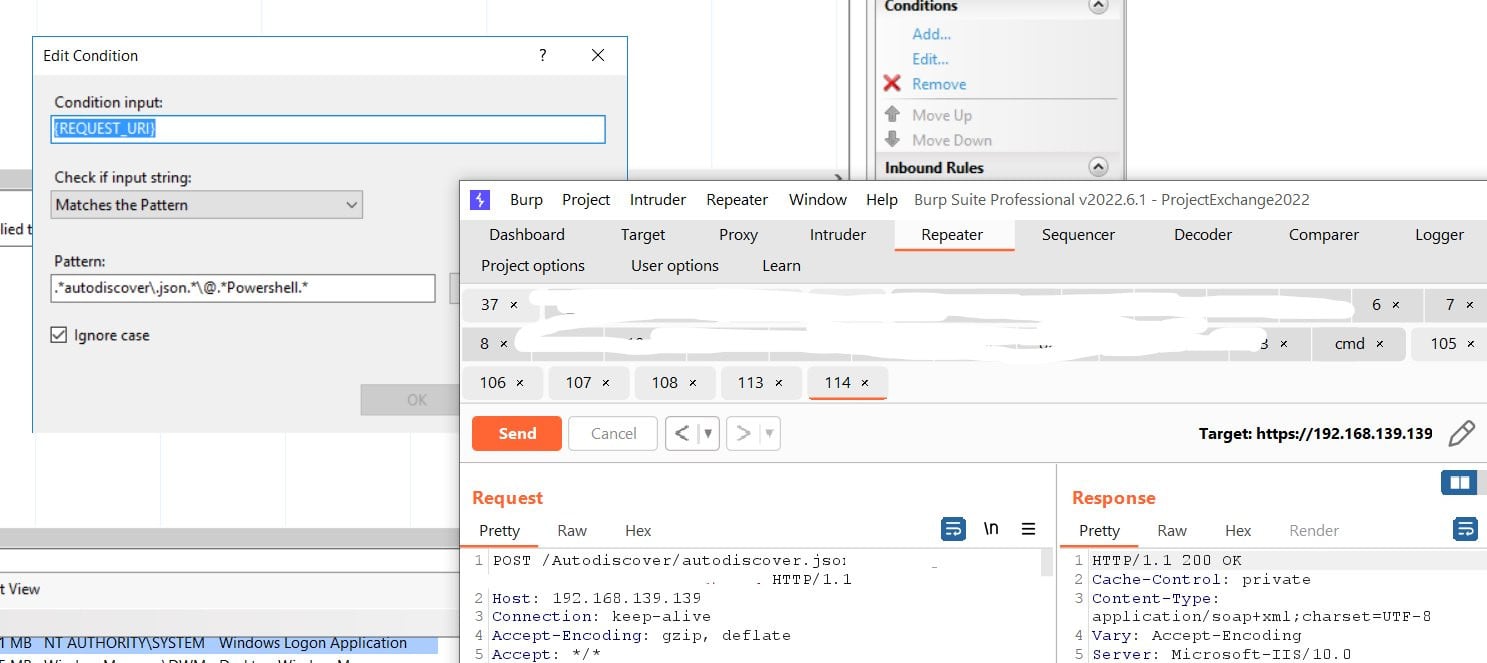
To reduce the risk of exploitation, Microsoft proposed blocking the known attack patterns through a rule in the IIS Manager:
- Open the IIS Manager.
- Select Default Web Site.
- In the** Feature View**, click URL Rewrite.
- In the Actions pane on the right-hand side, click Add Rules....
- Select** Request Blocking** and click OK.
- Add the string “.autodiscover.json.*@.*Powershell.” (excluding quotes) and then click OK.
- Expand the rule and select the rule with the pattern “autodiscover.json.*@.*Powershell.” and click Edit under Conditions.
- Change the Condition input from {URL} to {REQUEST_URI}
Administrators can achieve the same result by running Microsoft’s updated Exchange On-premises Mitigation Tool - a script that requires PowerShell 3 or later, needs to run with admin privileges, and runs on IIS 7.5 or newer.
The rule that Microsoft proposes, though, covers only known attacks, so the URL pattern is limited to them.
Security researcher Jang in a tweet today shows that Microsoft’s temporary solution for preventing the exploitation of CVE-2022-41040 and CVE-2022-41082 is not efficient and can be bypassed with little effort.
Will Dormann, a senior vulnerability analyst at ANALYGENCE, agrees with the finding and says that the '@' in Microsoft’s URL block “seems unnecessarily precise, and therefore insufficient.”
Jang’s finding has been tested by researchers at GTSC, who confirmed in a video today that Microsoft’s mitigation does not provide sufficient protection.
Instead of the URL block that Microsoft put forward, Jang provided a less specific alternative, designed to cover a wider set of attacks:
.*autodiscover\.json.*Powershell.*
Hybrid deployments at risk
In their advisories for the two vulnerabilities, Microsoft says that the mitigation instructions apply for customers with on-premise Exchange Server and that Exchange Online clients do not need to take any action.
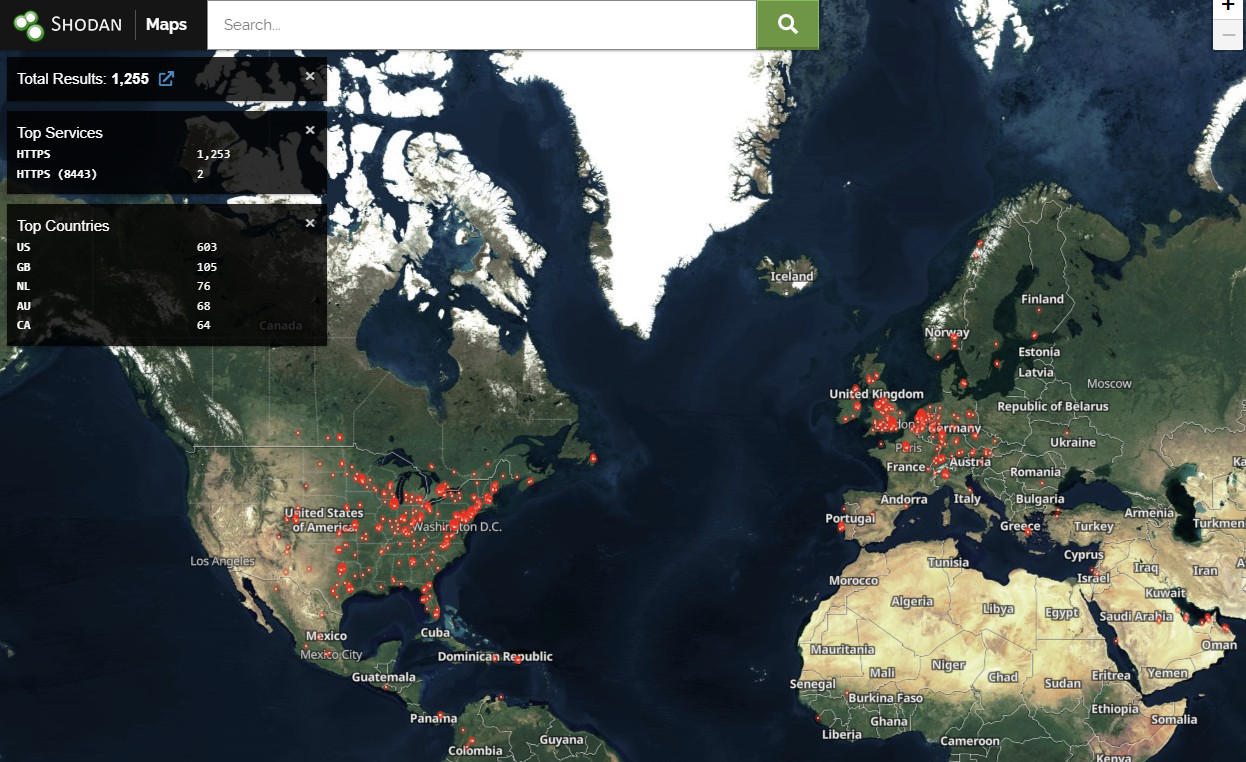
However, many organizations have a hybrid setup that combines on-prem with cloud deployment of Microsoft Exchange and they should understand that they are also vulnerable.
In a video today, security researcher Kevin Beaumont is warning that as long as there is an on-premise Exchange Server deployment, the organization is at risk.
Referring to the exploit chain as ProxyNotShell, Beaumont says that a hybrid Exchange setup is "extremely common" in enterprise environments and should consider the level of risk they're exposed to.
More than 1,200 of these organizations also expose their hybrid deployments on the public web. Among them are entities in the financial, education, and the government sector, all highly attractive targets for hackers running espionage or extortion operations.
A patch is yet to come
At the time of publishing, Microsoft has not released an update to fix the two issues but published security advisories with information about the impact and the conditions necessary for exploitation.
Microsoft describes CVE-2022-41040 as a high-risk (8.8/10 severity score) vulnerability that an attacker can leverage easily to increase their privilege on the affected machine without any user interaction.
The reason this security issue does not have a higher severity score is that the threat actor needs to be authenticated.
CVE-2022-41082 has the same high-severity score but it can be used for remote code execution on vulnerable on-premise Microsoft Exchange Servers by an attacker with “privileges that provide basic user capabilities” (settings and files owned by the user).
Update [October 3, 2022, 17:06 EST]: Article updated with clarification from Kevin Beaumont about some organizations' misconception that having a hybrid Microsoft Exchange setup would keep them safe from attacks.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.