Microsoft is further enhancing the Windows 11 Enhanced Phishing Protection by testing a new feature that warns users when they copy and paste their Windows password into websites and documents.
With the release of Windows 11 22H2, Microsoft introduced a new security feature called Enhanced Phishing protection, designed to protect your Windows and Active Directory domain credentials from being obtained by threat actors.
One of the most common methods threat actors use to gain access to websites or a corporate network is to purchase or steal corporate credentials. These credentials are obtained initially through phishing attacks or via information-stealing malware.
Threat actors use these stolen credentials to access other accounts used by the Windows user, including email accounts, bank accounts, and cryptocurrency trading accounts. Even worse, these stolen accounts can be used to access corporate networks, allowing the hackers to spread laterally on a network to conduct BEC scams, data theft, supply chain attacks, and ransomware attacks.
The number of stolen credentials is a massive and widespread problem, with cybercrime marketplaces selling billions of credentials and authentication cookies and more specialized sites selling over a million remote desktop credentials.
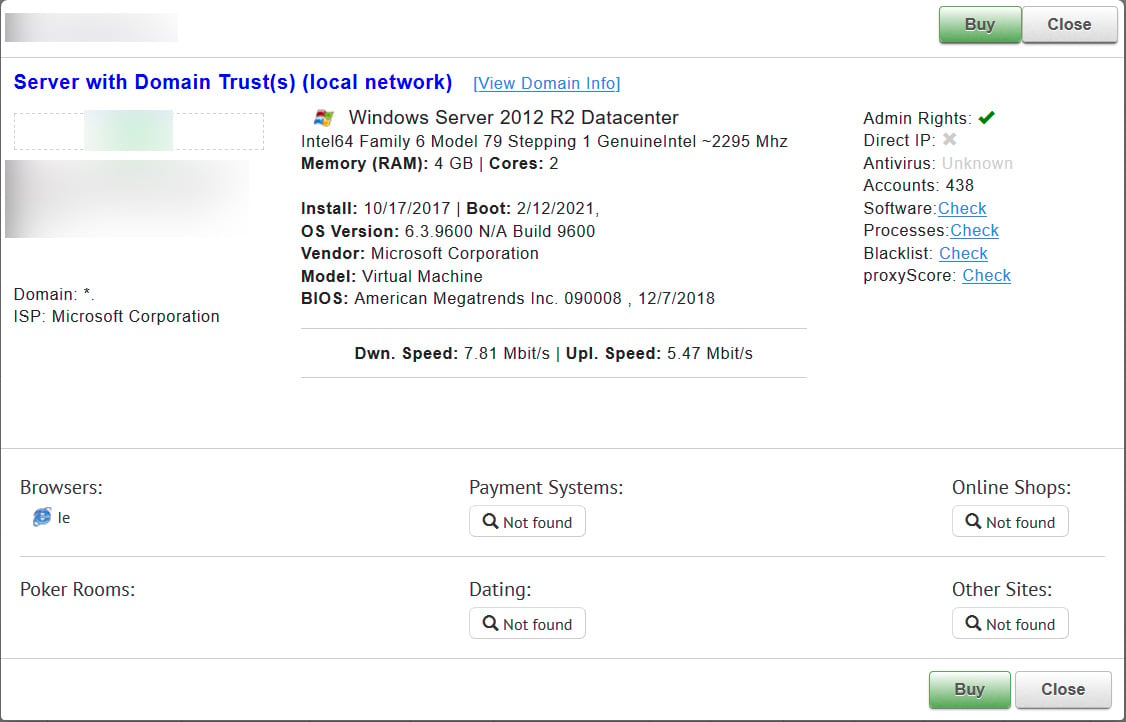
Stolen RDP credentials sold on dark web marketplace
Due to this widespread abuse, law enforcement has been actively targeting stolen credential marketplaces in law enforcement operations, seizing the WT1SHOP in 2022, and, more recently, taking down the Genesis Market.
Windows 11's Enhanced Phishing Protection
When Microsoft first released the new Windows Enhanced Phishing protection, it only warned users when they manually typed their Windows password into a document or web login page.
However, as it's commonly advised that users use password managers to create strong and unique passwords for all their logins, many people copy and paste their passwords from the password manager into their login prompts.
As the feature did not previously protect against copy and paste, this would bypass the Windows security feature.
With the release of Windows 11 Insider Dev build 23506, Microsoft has enhanced the phishing protection feature by now detecting the copy and paste of a user's Windows password.
"We are trying out a change starting with this build where users who have enabled warning options for Windows Security under App & browser control > Reputation-based protection > Phishing protection will see a UI warning on unsafe password copy and paste, just as they currently see when they type in their password," reads the Dev build release notes.
As this feature is not enabled by default, Windows users should turn it on by going to Windows Security > App & browser control > Reputation-based protection > Phishing protection and putting checkmarks under all three options, as shown below.
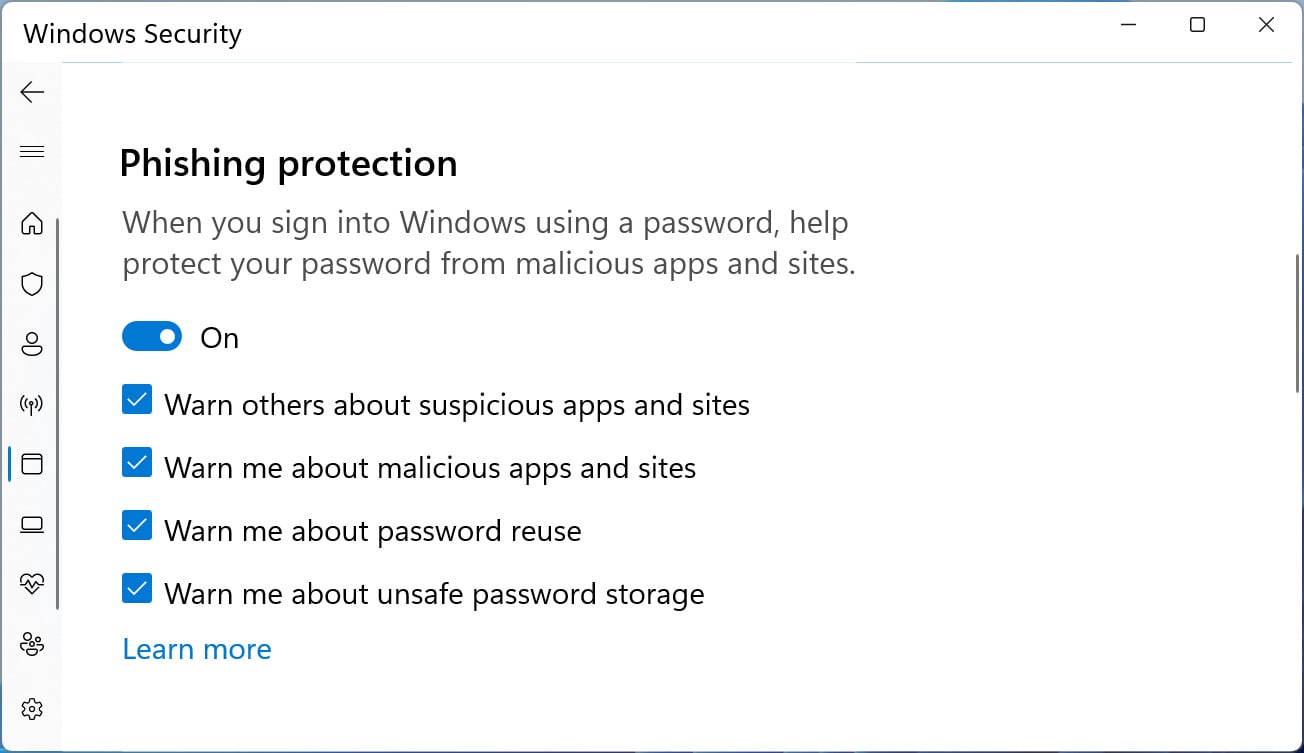
Phishing protection enabled in Windows 11Source: BleepingComputer
Once enabled, this feature will warn users when they type or copy and paste their Windows logon password into website forms or documents.
This alert will be titled "Password reuse is a security risk," and warns users to reset their Windows account password, linking to this support document.
"If your password is stolen from this site, attackers will true to use it other sites too. Use strong, unique passwords to keep your personal information safe," reads the Windows phishing protection alert.
"Microsoft recommends changing your local Windows account password."

Windows 11 phishing protection warningSource: BleepingComputer
While our previous Windows Enhanced Phishing Protection test showed that it did not work with certain applications, such as Firefox and Excel, today's tests show that this has been fixed, making the feature more robust.
However, it still does not work with other third-party applications that could commonly be used to store passwords, such as Notepad2, Notepad++, and likely many others.
Microsoft has also introduced a new "Warn others about suspicious apps and sites" phishing protection setting, but there is no information about this new setting and who 'others' represents.
Microsoft has not answered our questions related to this new setting.
Finally, it must be noted that the Windows 11 Phishing protection feature does not work if you use Windows Hello, such as PIN or biometrics, to log in to Windows.
For this feature to work, Windows users must log in with a password so it is cached in memory and can be compared to inputted text (typed or copied and pasted).
As this feature can be a powerful tool to protect corporate credentials, instantly alerting admins when a user is reusing their Windows password, trading the convenience of Windows Hello for better security is worth it.
It is recommended that all Windows users enable this security feature in Windows Security, even if it does not support all applications now.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.