Microsoft has announced that the Edge Vulnerability Research team is experimenting with a new feature dubbed "Super Duper Secure Mode" and designed to bring security improvements without significant performance losses.
When enabled, the new Microsoft Edge Super Duper Secure Mode will remove Just-In-Time Compilation (JIT) from the V8 processing pipeline, reducing the attack surface threat actors can use to hack into Edge users' systems.
Security without a major performance hit
Based on CVE (Common Vulnerabilities and Exposures) data collected since 2019, around 45% of vulnerabilities found in the V8 JavaScript and WebAssembly engine were related to the JIT engine, more than half of all 'in the wild' Chrome exploits abusing JIT bugs.
"This reduction of attack surface has potential to significantly improve user security; it would remove roughly half of the V8 bugs that must be fixed," explained Johnathan Norman, Microsoft Edge Vulnerability Research Lead.
"This reduction in attack surface kills half of the bugs we see in exploits and every remaining bug becomes more difficult to exploit. To put it another way, we lower costs for users but increase costs for attackers."
Additionally, while the JIT compiler is designed to increase performance by compiling computer during program execution (at run time), disabling it in Super Duper Secure Mode "does not always have negative impacts."
While still in the experimental stage, Super Duper Secure Mode can be enabled by users of Microsoft Edge preview releases (including Beta, Dev, and Canary) by going to edge://flags/#edge-enable-super-duper-secure-mode and toggling on the new feature.
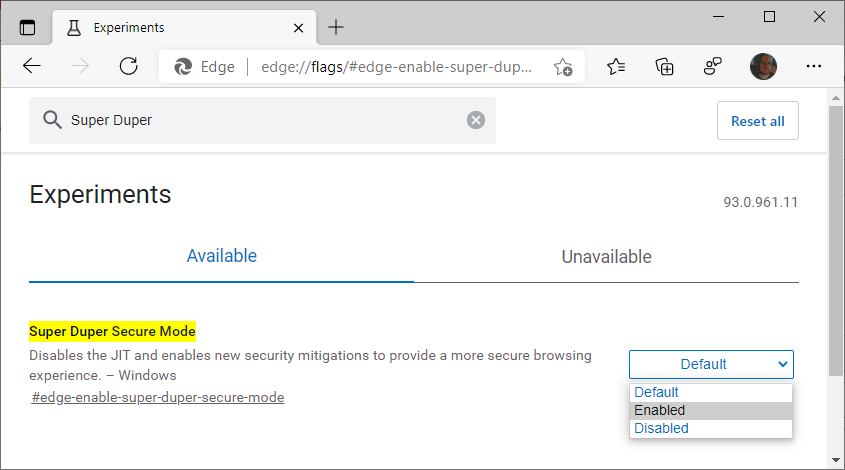
Right now, when enabled, Super Duper Secure Mode disables JIT (TurboFan/Sparkplug) and enables Control-flow Enforcement Technology (CET), an Intel hardware-based exploit mitigation designed to provide a more secure browsing experience.
In the future, Microsoft also wants to add support for Arbitrary Code Guard (ACG), another security mitigation that would prevent loading malicious code into memory, a technique used by most web browser exploits.
"This is of course just an experiment; things are subject to change, and we have quite a few technical challenges to overcome," Norman concluded.
"Also, our tongue-in-cheek name will likely need to change to something more professional when we launch as a feature. For now, we are going to continue having fun with it."
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.