Cryptocurrency investment companies are the target of a developing threat cluster that uses Telegram groups to seek out potential victims.
Microsoft's Security Threat Intelligence Center (MSTIC) is tracking the activity under the name DEV-0139, and builds upon a recent report from Volexity that attributed the same set of attacks to North Korea's Lazarus Group.
"DEV-0139 joined Telegram groups used to facilitate communication between VIP clients and cryptocurrency exchange platforms and identified their target from among the members," the tech giant said.
The adversary subsequently impersonated another cryptocurrency investment company and invited the victim to join a different Telegram chat group under the pretext of asking for feedback on the trading fee structure used by exchange platforms across VIP tiers.
It's worth pointing out that the VIP program is designed to reward high-volume traders with exclusive trading fee incentives and discounts based on the activity in the past 30 days.
This attack chain notably dovetails with Volexity's analysis of an October 2022 campaign, wherein the threat actor pivoted from using MSI installer files to a weaponized Microsoft Excel document displaying the supposed cryptocurrency coin rates.
Microsoft described the document as containing likely accurate data to increase the likelihood of success of the campaign, suggesting that DEV-0139 is well versed in the inner workings of the crypto industry.
The malware-laced Excel file, for its part, is tasked with executing a malicious macro that's used to stealthily drop and execute a second Excel worksheet, which, in turn, includes a macro that downloads a PNG image file hosted on OpenDrive.
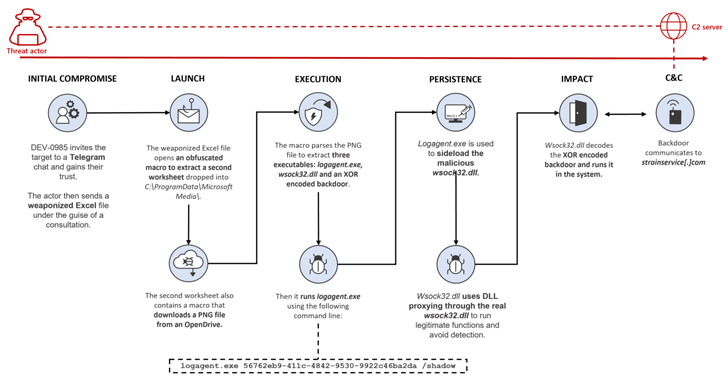
This image file contains three executables, each of which is used to launch the next-stage payload, ultimately paving the way for a backdoor that lets the threat actor remotely access the infected system.
Furthermore, the fee structure spreadsheet is password-protected in a bid to convince the target into enabling macros, thereby initiating the malicious actions. A metadata analysis of the file shows that it was created on October 14, 2022 by a user named Wolf.
DEV-0139 has also been linked to an alternative attack sequence in which an MSI package for a fake application named "CryptoDashboardV2" is delivered in place of a malicious Excel document to deploy the same implant.
The backdoor mainly enables remote access to the host by gathering information from the targeted system and connecting to a command-and-control (C2) server to receive additional commands.
"The cryptocurrency market remains a field of interest for threat actors," Microsoft said. "Targeted users are identified through trusted channels to increase the chance of success."
In recent years, Telegram has not only witnessed widespread adoption in the cryptocurrency industry, but also been co-opted by threat actors looking to discuss zero-day vulnerabilities, offer stolen data, and market their services through the popular messaging platform.
"With users losing confidence in the anonymity offered by forums, illicit marketplaces are increasingly turning to Telegram," Positive Technologies disclosed in a new study of 323 public Telegram channels and groups with over one million subscribers in total.
"The number of unique cyberattacks is constantly growing, and the market for cybercriminal services is expanding and moving into ordinary social media and messaging apps, thereby significantly lowering the entry threshold for cybercriminals."
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.