An ongoing phishing campaign targeting U.S. government contractors has expanded its operation to push higher-quality lures and better-crafted documents.
The lure in these phishing emails is a request for bids for lucrative government projects, taking them to phishing pages that are clones of legitimate federal agency portals.
This is the same operation that INKY reported about in January 2022, with the threat actors using attached PDFs with instructions on going through the bidding process for the U.S. Department of Labor projects.
According to a report by Cofense, the operatives have expanded their targeting and are now also spoofing the Department of Transportation and the Department of Commerce.
Moreover, there’s now a plethora of different lures used in the messages, better phishing web page behavior, and removal of artifacts that revealed the signs of fraud in previous versions of the attached PDFs.
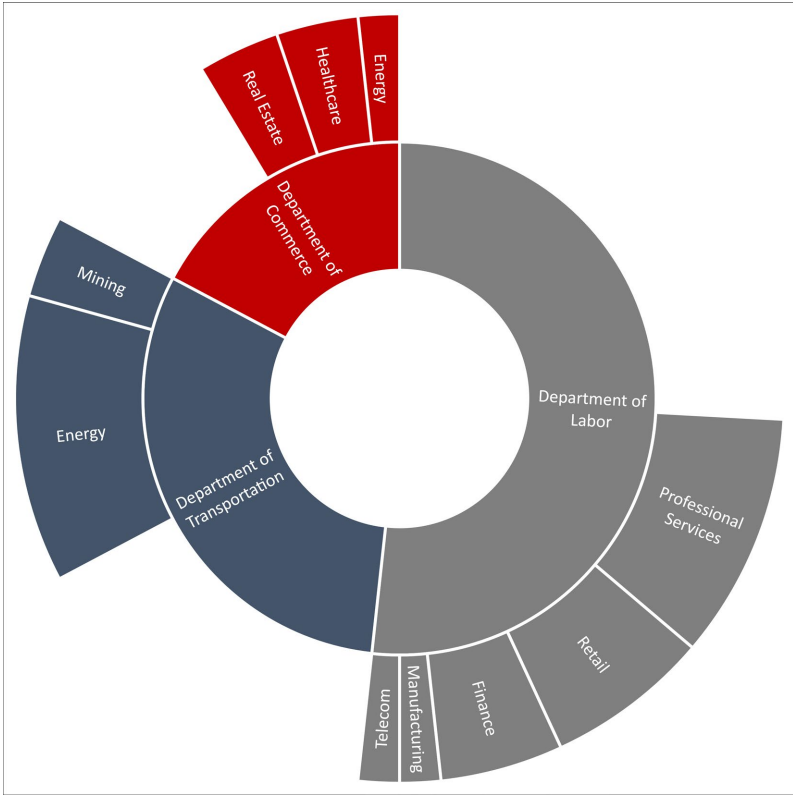
The various lures used for each case of spoofed department (Cofense)
Polishing a high-quality campaign
Building upon what they have previously achieved, the phishing actors behind this campaign have implemented careful revisions to increase their success rates.
Starting with the phishing emails, Cofense reports they now feature more consistent formatting, larger logos, and prefer to include a link to the PDF instead of attaching the file.
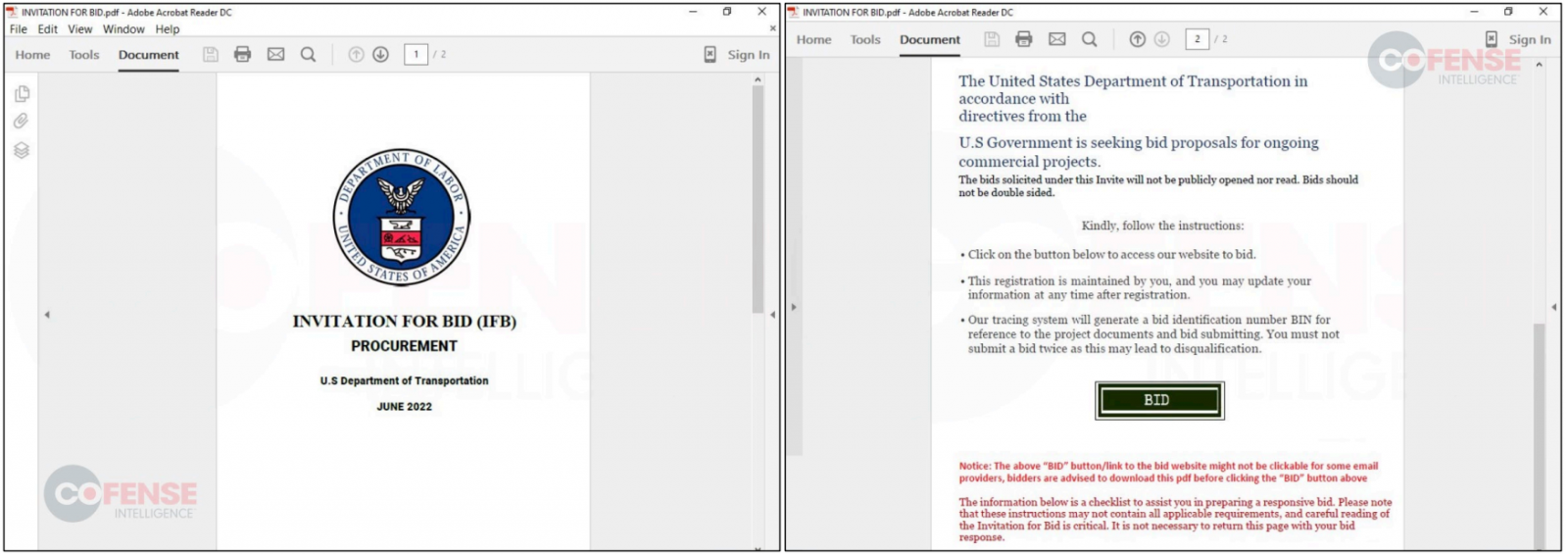
First and second page of new PDFs used in the campaign (Cofense)
The PDF files used to contain detailed instructions on how to bid, with overly technical information included. Now, they have been simplified and reduced in size, featuring more prominent logos and a link to the phishing page.
Also, the PDFs previously featured the same signee, “edward ambakederemo,” whereas now, the metadata in the documents matches the spoofed department. For example, lures supposedly sent by the Wisconsin Department of Transportation are signed with “WisDOT.”
The phishing websites have also received targeted improvements, using HTTPS on all web pages in the same domain.
In addition to the “.gov” sites previously serving the campaign, the threat actors now also use very long domains like “transportation[.]gov[.]bidprocure[.]secure[.]akjackpot[.]com” to make them appear legitimate when opened from mobile browsers that can’t show the full length in the URL bar.
On the phishing page that tries to trick visitors into entering their Microsoft Office 365 account credentials, the threat actors have now added a Captcha Challenge step to ensure they’re not logging bot inputs.
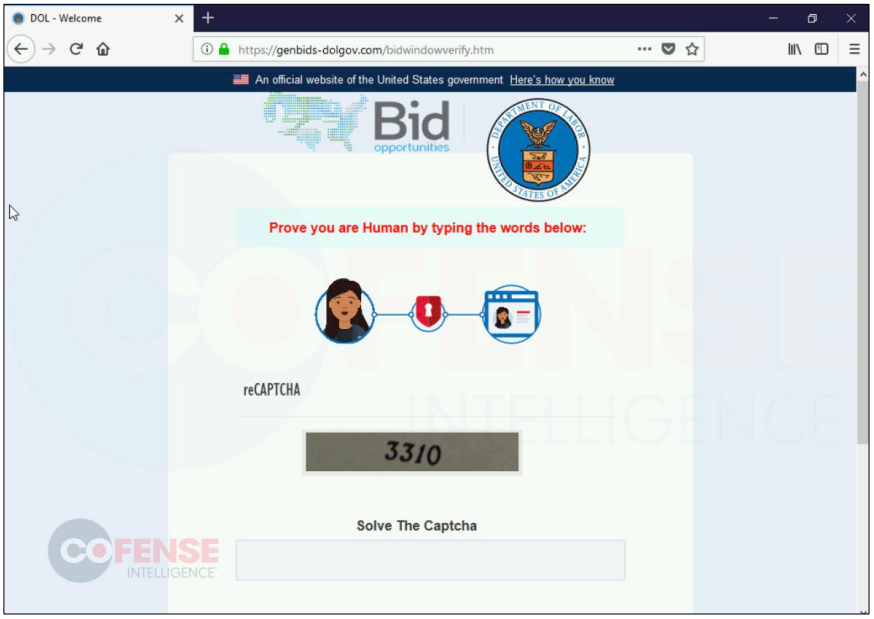
Captcha step added before exfiltrating the credentials (Cofense)
Outlook
It appears that the operatives of this campaign aren’t likely to stop any time soon, as they are now simultaneously expanding their targeting scope while refining their lures.
Considering that the emails, PDFs, and websites used in this phishing operation are essentially copies of the actual content from requests for bids and state bidding portals, it may be hard to catch the signs of fraud.
“Given the advancements seen in each area of the phishing chain, it is likely the threat actors behind these campaigns will continue to innovate and improve upon their already believable campaigns,” predicts Cofense.
The only way to defend against this is to examine all details like the sending address, the landing URL, and eventually visit the bidding portal through a search engine instead of following provided links.
If unsure, try searching the URLs online, as many of these long-lasting campaigns have published indicators of compromise confirming their fraudulent nature.
Source: Bleeping Computer




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.