Authorities in the United States, Germany, the Netherlands and the U.K. last week said they dismantled the “RSOCKS” botnet, a collection of millions of hacked devices that were sold as “proxies” to cybercriminals looking for ways to route their malicious traffic through someone else’s computer. While the coordinated action did not name the Russian hackers allegedly behind RSOCKS, KrebsOnSecurity has identified its owner as a 35-year-old Russian man living abroad who also runs the world’s top spam forum.
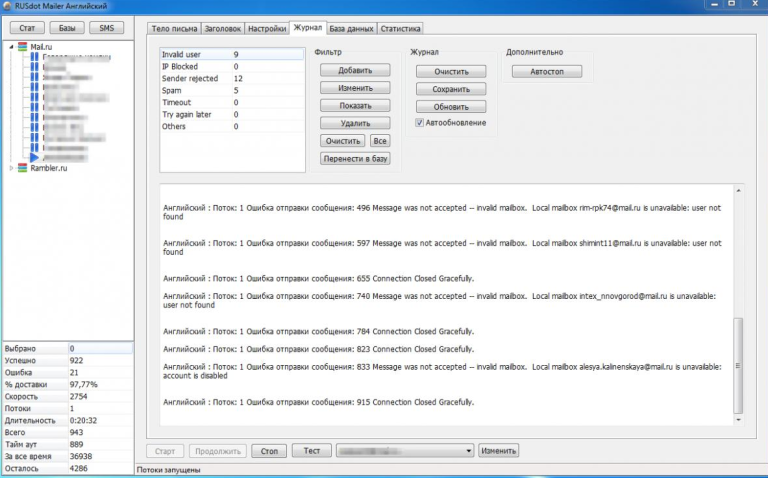
The RUSdot mailer, the email spamming tool made and sold by the administrator of RSOCKS.
According to a statement by the U.S. Department of Justice, RSOCKS offered clients access to IP addresses assigned to devices that had been hacked:
“A cybercriminal who wanted to utilize the RSOCKS platform could use a web browser to navigate to a web-based ‘storefront’ (i.e., a public web site that allows users to purchase access to the botnet), which allowed the customer to pay to rent access to a pool of proxies for a specified daily, weekly, or monthly time period. The cost for access to a pool of RSOCKS proxies ranged from $30 per day for access to 2,000 proxies to $200 per day for access to 90,000 proxies.”
The DOJ’s statement doesn’t mention that RSOCKS has been in operation since 2014, when access to the web store for the botnet was first advertised on multiple Russian-language cybercrime forums.
The user “RSOCKS” on the Russian crime forum Verified changed his name to RSOCKS from a previous handle: “Stanx,” whose very first sales thread on Verified in 2016 quickly ran afoul of the forum’s rules and prompted a public chastisement by the forum’s administrator.
Verified was hacked twice in the past few years, and each time the private messages of all users on the forum were leaked. Those messages show that after being warned of his forum infraction, Stanx sent a private message to the Verified administrator detailing his cybercriminal bona fides.
“I am the owner of the RUSdot forum (former Spamdot),” Stanx wrote in Sept. 2016. “In spam topics, people know me as a reliable person.”
A Google-translated version of the Rusdot spam forum.
RUSdot is the successor forum to Spamdot, a far more secretive and restricted forum where most of the world’s top spammers, virus writers and cybercriminals collaborated for years before the community’s implosion in 2010. Even today, the RUSdot Mailer is advertised for sale at the top of the RUSdot community forum.
Stanx said he was a longtime member of several major forums, including the Russian hacker forum Antichat (since 2005), and the Russian crime forum Exploit (since April 2013). In an early post to Antichat in January 2005, Stanx disclosed that he is from Omsk, a large city in the Siberian region of Russia.
According to the cyber intelligence firm Intel 471, the user Stanx indeed registered on Exploit in 2013, using the email address [email protected], and the ICQ number 399611. A search in Google for that ICQ number turns up a cached version of a Vkontakte profile for a Denis “Neo” Kloster, from Omsk, Russia.
Cybersecurity firm Constella Intelligence shows that in 2017, someone using the email address [email protected] registered at the Russian freelancer job site fl.ru with the profile name of “Denis Kloster” and the Omsk phone number of 79136334444. Another record indexed by Constella suggests Denis’s real surname may in fact be “Emilyantsev” [Емельянцев].
That phone number is tied to the WHOIS registration records for multiple domain names over the years, including proxy[.]info, allproxy[.]info, kloster.pro and deniskloster.com.

A copy of the passport for Denis Kloster, as posted to his Vkontakte page in 2019. It shows that in Oct. 2019, he obtained a visa from the American Embassy in Bangkok, Thailand.
The “about me” section of DenisKloster.com says the 35-year-old was born in Omsk, that he got his first computer at age 12, and graduated from high school at 16. Kloster says he’s worked in many large companies in Omsk as a system administrator, web developer and photographer.
According to Kloster’s blog, his first real job was running an “online advertising” firm he founded called Internet Advertising Omsk (“riOmsk“), and that he even lived in New York City for a while.
“Something new was required and I decided to leave Omsk and try to live in the States,” Kloster wrote in 2013. “I opened an American visa for myself, it was not difficult to get. And so I moved to live in New York, the largest city in the world, in a country where all wishes come true. But even this was not enough for me, and since then I began to travel the world.”
The current version of the About Me page on Kloster’s site says he closed his advertising business in 2013 to travel the world and focus on his new company: One that provides security and anonymity services to customers around the world. Kloster’s vanity website and LinkedIn page both list him as CEO of a company called “SL MobPartners.”
In 2016, Deniskloster.com featured a post celebrating three years in operation. The anniversary post said Kloster’s anonymity business had grown to nearly two dozen employees, most of whom were included in a group photo posted to that article (and some of whom Kloster thanked by their first names and last initials).

The employees who kept things running for RSOCKS, circa 2016.
“Thanks to you, we are now developing in the field of information security and anonymity!,” the post enthuses. “We make products that are used by thousands of people around the world, and this is very cool! And this is just the beginning!!! We don’t just work together and we’re not just friends, we’re Family.”
Mr. Kloster did not respond to repeated requests for comment.
It’s not clear if the coordinated takedown targeting the RSOCKS botnet will be permanent, as the botnet’s owners could simply rebuild — and possibly rebrand — their crime machine. Based on the RSOCKS owner’s posts, that is exactly what they intend to do.
“RSocks ceases to exist,” wrote the Rsocks account on the BlackHatWorld forum on June 17. “But don’t worry. All the active plans and fund balances will be transferred to another service. Stay tuned. We will inform you about its name and all the details later.”
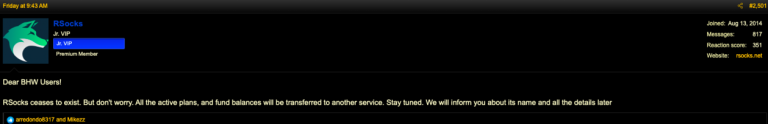
Rsocks told the BlackHatWorld community they would be back soon under a new name.
Malware-based proxy services like RSOCKS have struggled to remain competitive in a cybercrime market with increasingly sophisticated proxy services that offer many additional features. The demise of RSOCKS follows closely on the heels of VIP72[.]com, a competing proxy botnet service that operated for a decade before its owners pulled the plug on the service last year.
- aum
-

 1
1


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.