Mastodon, the free and open-source decentralized social networking platform, has fixed a critical vulnerability that allows attackers to impersonate and take over any remote account.
The platform became popular after Elon Musk acquired Twitter and now boasts nearly 12 million users spread across 11,000 instances.
Instances (servers) on Mastodon are autonomous but interconnected (through a system known as "federation") communities that have their own guidelines and policies, controlled by owners who provide the infrastructure and act as administrators of their servers.
The newly fixed flaw is tracked as CVE-2024-23832 and stems from insufficient origin validation in Mastodon, allowing attackers to impersonate users and take over their accounts.
The vulnerability is rated 9.4 in CVSS v3.1 and impacts all Mastodon versions before 3.5.17, 4.0.13, 4.1.13, and 4.2.5.
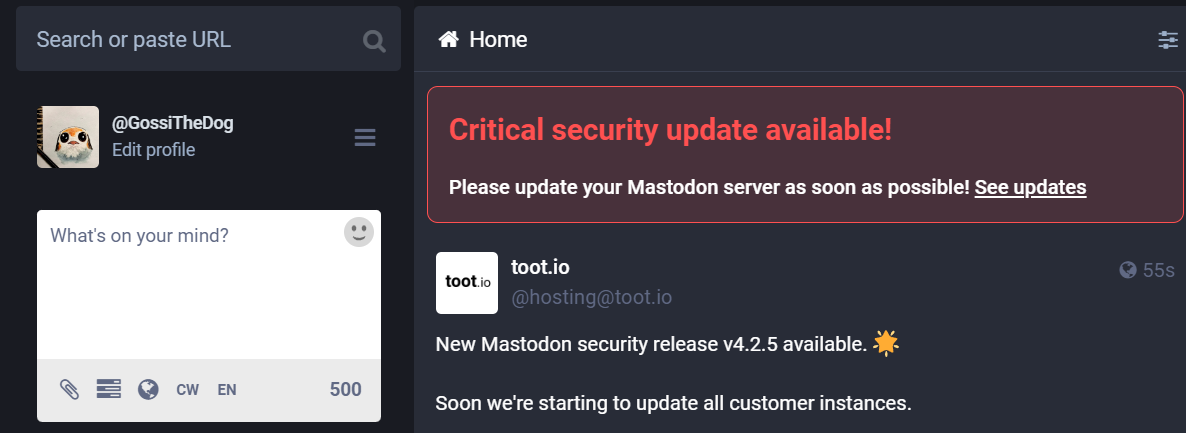
The flaw was fixed as of 4.2.5, released yesterday, which all Mastodon server administrators are advised to upgrade to as soon as possible to protect users of their instances.
Mastodon has withheld technical details for the time being to prevent active exploitation of the vulnerability. However, they promised to share more information about CVE-2024-23832 on February 15, 2024.
Mastodon users cannot do anything to address the security risk, but they should ensure that the admins of the instance they participate in have upgraded to a safe version by mid-February; otherwise, their accounts will be prone to hijacking.
Thankfully, Mastodon has opted to alert server admins via a pronounced banner about the critical update, so all instances that are actively maintained should become aware of the update and move to the safe version in the following days.
The repercussions of account impersonation and takeover in Mastodon can be significant, impacting individual users, communities, and the integrity of the platform, so CVE-2024-23832 is a severe flaw.
In July 2023, the Mastodon team fixed another critical bug tracked as CVE-2023-36460 and dubbed 'TootRoot,' which allowed attackers to send "toots" (the equivalent of tweets) that would create web shells on target instances.
Attackers could leverage this flaw to completely compromise Mastodon servers, allowing them to access sensitive user information, communications, and plant backdoors.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.