Researchers have uncovered a large-scale phishing operation that abused Facebook and Messenger to lure millions of users to phishing pages, tricking them into entering their account credentials and seeing advertisements.
The campaign operators used these stolen accounts to send further phishing messages to their friends, generating significant revenue via online advertising commissions.
According to PIXM, a New York-based AI-focused cybersecurity firm, the campaign peaked in April-May 2022 but has been active since at least September 2021.
PIXM was able to trace the threat actor and map the campaign due to one of the identified phishing pages hosting a link to a traffic monitoring app (whos.amung.us) that was publicly accessible ithout authentication.
Massive scale of abuse
While it is unknown how the campaign initially started, PIXM states victims arrived at phishing landing pages from a series of redirects originating from Facebook Messenger.
As more Facebook accounts were stolen, the threat actors used automated tools to send further phishing links to the compromised account's friends, creating massive growth in stolen accounts.
"A user's account would be compromised and, in a likely automated fashion, the threat actor would log in to that account and send out the link to the user's friends via Facebook Messenger," explains PIXM in the report.
While Facebook has protection measures to stop the dissemination of phishing URLs, the threat actors used a trick to bypass these protections.
The phishing messages used legitimate URL generation services such as litch.me, famous.co, amaze.co, and funnel-preview.com, which would be a problem to block as legitimate apps use them.
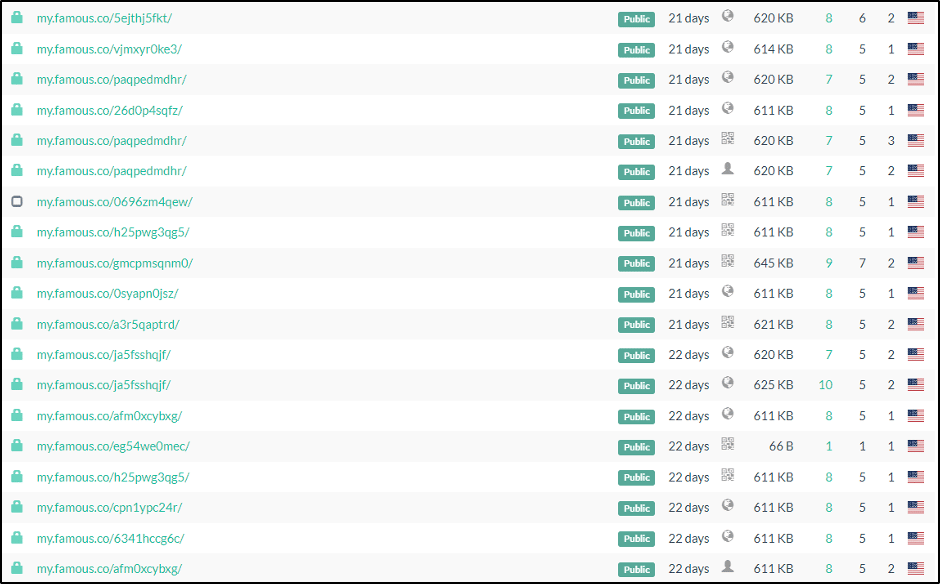
After discovering that they could gain unauthenticated access to the phishing campaign stats pages, the researchers found that in 2021, 2.7 million users had visited one of the phishing portals. This figure went up to 8.5 million in 2022, reflecting the massive growth of the campaign.
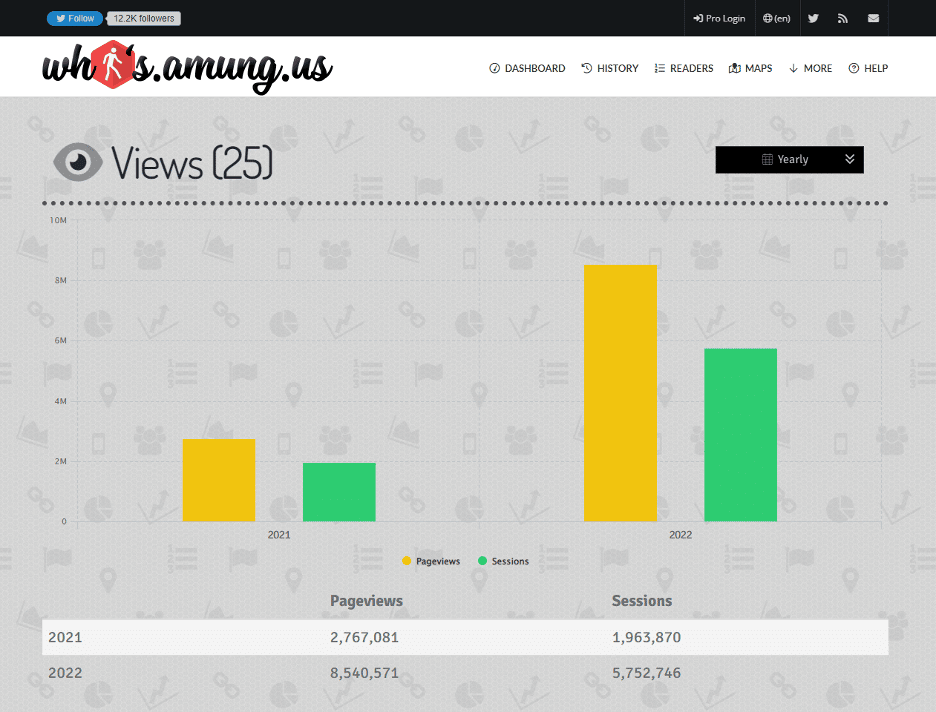
By diving deeper, the researchers identified 405 unique usernames used as campaign identifiers, each having a separate Facebook phishing page. These phishing pages had page views ranging from only 4,000 views to some in the millions, with one as high as 6 million page views.
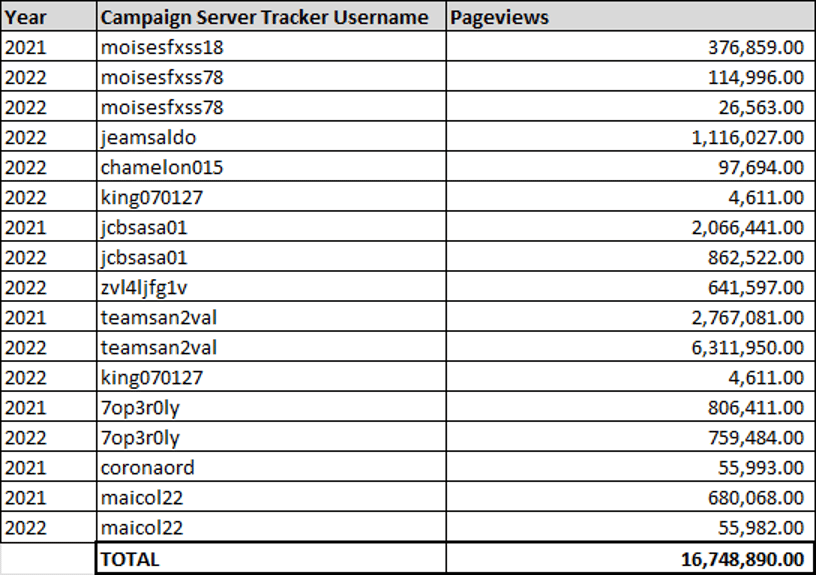
The researchers believe that these 405 usernames represent only a fraction of the accounts used for the campaign.
After the victim enters their credentials on the phishing landing page, a new round of redirections begins, taking them to advertising pages, survey forms, etc.
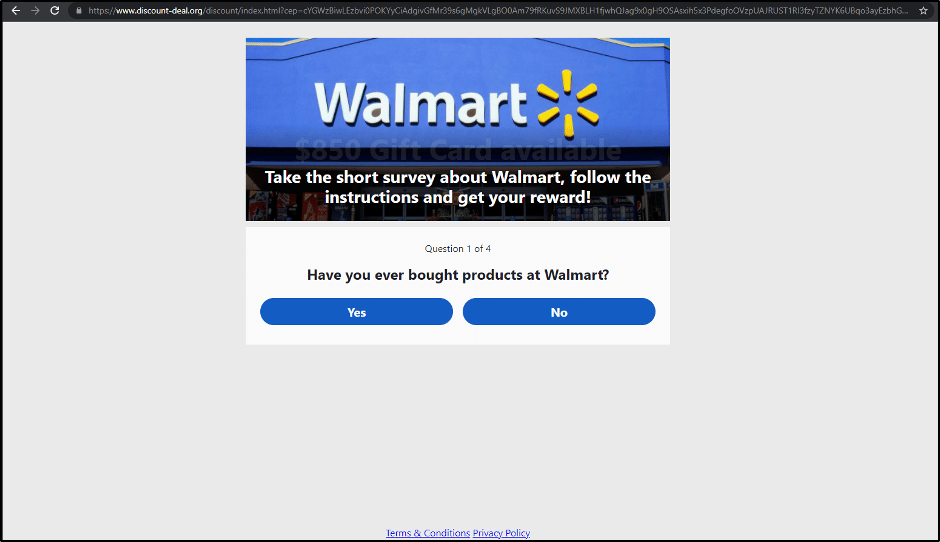
The threat actors receive referral revenue from these redirects, which are estimated to be millions of USD at this scale of operation.
Tracing the threat actor
PIXM found a common code snippet on all landing pages, which contained a reference to a website that has been seized and constitutes part of an investigation against a Colombian man identified as Rafael Dorado.
.png)
It is unclear who seized the domain and placed the notice on the site.
A reverse whois lookup revealed links to a legitimate web development company in Colombia and old sites offering Facebook "like bots" and hacking services.
PIXM shared the results of its investigation with the Colombian Police and Interpol, but as they note, the campaign is still ongoing, even though many of the identified URLs have gone offline.
Massive Facebook Messenger phishing operation generates millions



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.