Russia's second-largest financial institution VTB Bank says it is facing the worse cyberattack in its history after its website and mobile apps were taken offline due to an ongoing DDoS (distributed denial of service) attack.
"At present, the VTB technological infrastructure is under unprecedented cyberattack from abroad," stated a VTB spokesperson to TASS (translated).
"It is not only the largest cyberattack recorded this year, but in the entire history of the bank."
The bank says its internal analysis indicates the DDoS attack was planned and orchestrated with the specific purpose of causing inconvenience to its customers by disrupting its banking services.
At this time, VTB's online portals are offline, but the institute says all core banking services operate normally.
Moreover, VTB says customer data are protected as it's stored in the internal perimeter of its infrastructure, which the attackers have not breached.
The bank says it has identified that most malicious DDoS requests originate from outside the country. However, there are several Russian IP addresses involved in the attack too.
This means that foreign actors either use local proxies for the attacks or have managed to recruit local dissidents in their DDoS campaign.
Information about these IP addresses has been relayed to the Russian law enforcement authorities for criminal investigation.
VTB is 61% state-owned, with the Ministry of Finance and Ministry of Economic Development having a share in the group, so these attacks have a political hue, being an indirect blow to the Russian government.
'IT Army of Ukraine' claims attack
The pro-Ukraine hacktivist group, 'IT Army of Ukraine,' has claimed responsibility for the DDoS attacks against VTB, announcing the campaign on Telegram at the end of November.
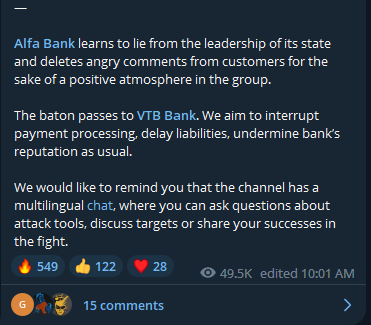
Hacktivists announcing VTB as the target
(BleepingComputer)
The particular group of hacktivists was formed with the official blessing of the Ukrainian government in February 2022, attempting to strengthen the country’s cyber front.
Notable service disruptions caused by the ‘IT Army of Ukraine’ include an outage in the portal used by vodka producers and distributors and the downing of the sites of Rostec, a leading Russian aerospace and defense conglomerate.
The pro-Ukraine hacktivists have been very active in November, targeting over 900 Russian entities, including stores selling military equipment and drones, the Central Bank of Russia, the National Center for the Development of Artificial Intelligence, and Alfa Bank.
The first signs of disruption on VTB came on December 1, 2022, when the hacktivists posted complaints about VTB customers on social media that the bank tried to play down.
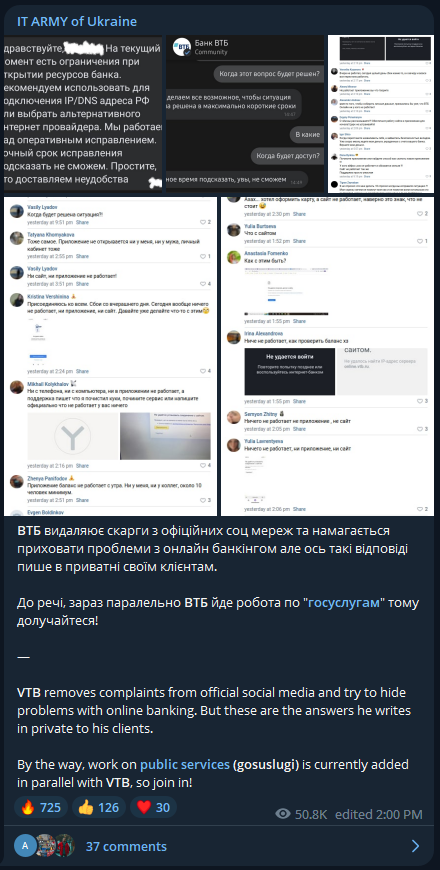
Follow-up to showcase disruption in VTB
(BleepingComputer)
With the bank's service disruption more evident now, as the websites and mobile apps are no longer available, VTB had to publicly admit it is fighting a DDoS attack.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.