An actor that security researchers call Prolific Puma has been providing link shortening services to cybercriminals for at least four years while keeping a sufficiently low profile to operate undetected.
In less than a month, Prolific Puma has registered thousands of domains, many on the U.S. top-level domain (usTLD), to help with the delivery of phishing, scams, and malware.
Short URL service for cybercriminals
Researchers from Infoblox, a DNS-focused security vendor that looks at 70 billion DNS queries daily, first observed Prolific Puma activity six months ago, after detecting a registered domain generation algorithm (RDGA) to create the domain names for the malicious URL shortening service.
Using specialized DNS detectors, they were able to track the malicious network as it evolved and abused the usTLD to facilitate crime on the internet.
Because of the nature of link shortening services, Infoblox could track the short links but not the final landing page, despite detecting a large number of interconnected domains exhibiting suspicious behavior.
“We eventually captured several instances of shortened links redirecting to final landing pages that were phishing and scam sites” - Infoblox
Some of the short links from Prolific Puma led directly to the final destination but others pointed to multiple redirects, even other shortened links, before getting to the landing page.
Infoblox says that there were also cases where accessing the short link took the user to a CAPTCHA challenge, likely to protect from automated scans.
Because of this inconsistency in what Prolific Puma’s short links loaded next, the researchers believe that multiple actors are using the service.
The delivery method for these links also varies and includes social media and advertisements but evidence points to text messages as the main channel.
Massive operation
The size of the Prolific Puma operation as uncovered by Infoblox is impressive. The actor registered up to 75,000 unique domain names since April 2022.
Looking at the unique domains in the actor’s network, the researchers saw at the beginning of the year a peak of close to 800 domains of up to four characters created in a single day.
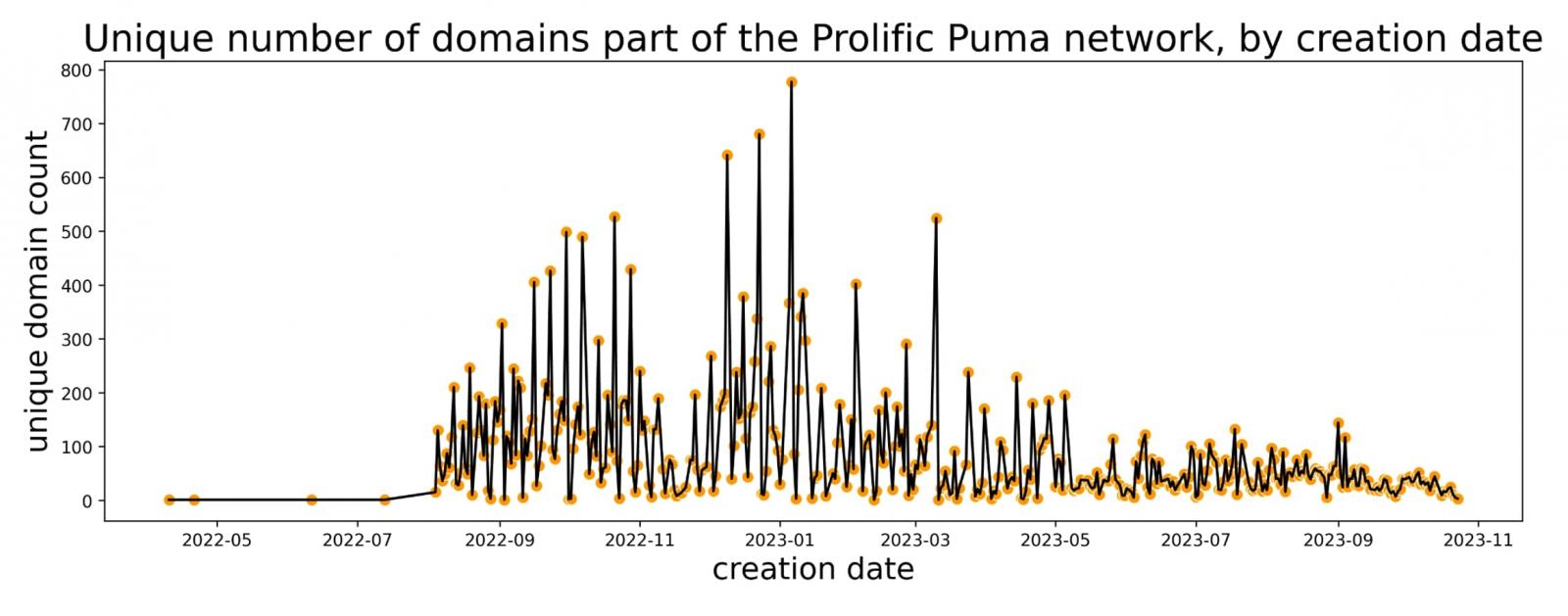
Prolific Puma domains are spread across 13 TLDs. Since May this year, though, the actor used the usTLD for more than half of the total domains created, the daily average being 43.
Since mid-October, the researchers noticed closed to 2,000 domains in the usTLD indicating Prolific Puma activity that are behind private registration protection.
| Registrar | Domain Count (Sept 1 – Oct 15, 2023) |
|---|---|
| NameSilo – Prolific Puma | 1062 |
| NameSilo – possibly not Prolific Puma | 411 |
| PorkBun | 5 |
| NameCheap | 4 |
| Sav.com | 1 |
| Privately registered domains in the usTLD | |
It is worth mentioning that private registrations is not permitted in the .US namespace under the current policy and the registrant is required to provide accurate and true information.
Furthermore, registrars have an obligation to not offer private domain registrations to .US domain name registrants.
Typically, Prolific Puma domains are alphanumeric, pseudo-random, and vary in size, three or four-character ones being the most common. However, the researchers observed domains as long as seven characters.
| TLD | us | link | info | com | cc | me |
|---|---|---|---|---|---|---|
| Domains |
vf8[.]us 2ug[.]us z3w[.]us yw9[.]us 8tm[.]us |
cewm[.]link wrzt[.]link hhqm[.]link ezqz[.]link zyke[.]link |
uelr[.]info ldka[.]info fbvn[.]info baew[.]info shpw[.]info |
kfwpr[.]com trqrh[.]com nhcux[.]com khrig[.]com dvcgg[.]com |
jlza[.]cc hpko[.]cc ddkn[.]cc mpsi[.]cc wkby[.]cc |
scob[.]me xnxk[.]me zoru[.]me mjzo[.]me ouzp[.]me |
| Examples of 3 to 4 characters long domains registered by Prolific Puma on different TLDs | ||||||
In the last three years, the actor used hosting mainly from NameSilo, a cheap internet domain registrar that is often abused by cybercriminals, that offers an API for bulk registration.
To avoid scrutiny and detection, Prolific Puma ages its domains by leaving them inactive or parked for a several weeks. During this period, the actor makes a few DNS queries to gain reputation.
When ready for use, the actor transfers the domains to a bulletproof hosting provider, paying in Bitcoin cryptocurrency for a virtual private server with service with a dedicated IP address.
Infoblox found that some of these domains are abandoned after a period but the DNS record still points to the dedicated IP.
The researchers believe that Prolific Puma only provides the short link service and does not control the landing pages but do not exclude the possibility that the same actor runs the entire operation.
Below is an example of how Prolific Puma's service is used in a campaign with a phishing page asking for credentials and a payment, to ultimately deliver a malicious browser plugin.
According to Infoblox, the actor does not advertise its shortening service on underground markets but it is the largest and most dynamic. Using tens of thousands of domain names registered across multiple registrars enables them to fly under the radar.
“While security providers may identify and block the final content, without a broader view it is difficult to see the full scope of the activity and associate the domains together under a single DNS threat actor” - Infoblox
Infoblox was able to uncover the massive operation through algorithms that flag suspicious or malicious domains. Through passive DNS query logs, newly queried, registered, or configured domains are assessed and flagged as suspicious or malicious if they meet the criteria for associating them with a DNS threat actor.
Uncovering Prolific Puma started with automated analytics, which reveled a few related domains. When the company deployed algorithms for RDGA discovery earlier this year, domains used were identified in groups. Another algorithm correlated the domain clusters and attributed them to a single DNS threat actor.
The report from Infoblox provides a set of indicators for Prolific Puma activity that includes links shortner hosting IP addresses and domains, redirection and landing pages, and an email address found in domain registration data.
- vitorio
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.