An automated and large-scale 'freejacking' campaign abuses free GitHub, Heroku, and Buddy services to mine cryptocurrency at the provider's expense.
The operation relies on abusing the limited resources offered to free-tier cloud accounts to generate a tiny profit from each free account, which, when combined, becomes something more significant.
The threat actor behind the campaign, called 'Purpleurchin,' was observed performing over a million function calls daily, using CI/CD service providers such as GitHub (300 accounts), Heroku (2,000 accounts), and Buddy.works (900 accounts).
The use of those accounts is rotated and channeled through 130 Docker Hub images with mining containers, while obfuscation on all operational levels has kept Purpleurchin undetected until now.
Operation details
In a new report by Sysdig, researchers explain that the core of the operation is a linuxapp container ('linuxapp84744474447444744474') that acts as the command and control server (C2) and Stratum server, coordinating all active mining agents and directing them to the threat actor's mining pool.
A shell script ('userlinux8888') is used to automate the creation of GitHub accounts, create a repository, and replicate the workflow using GitHub actions. All GitHub actions are obfuscated using random strings for the names.
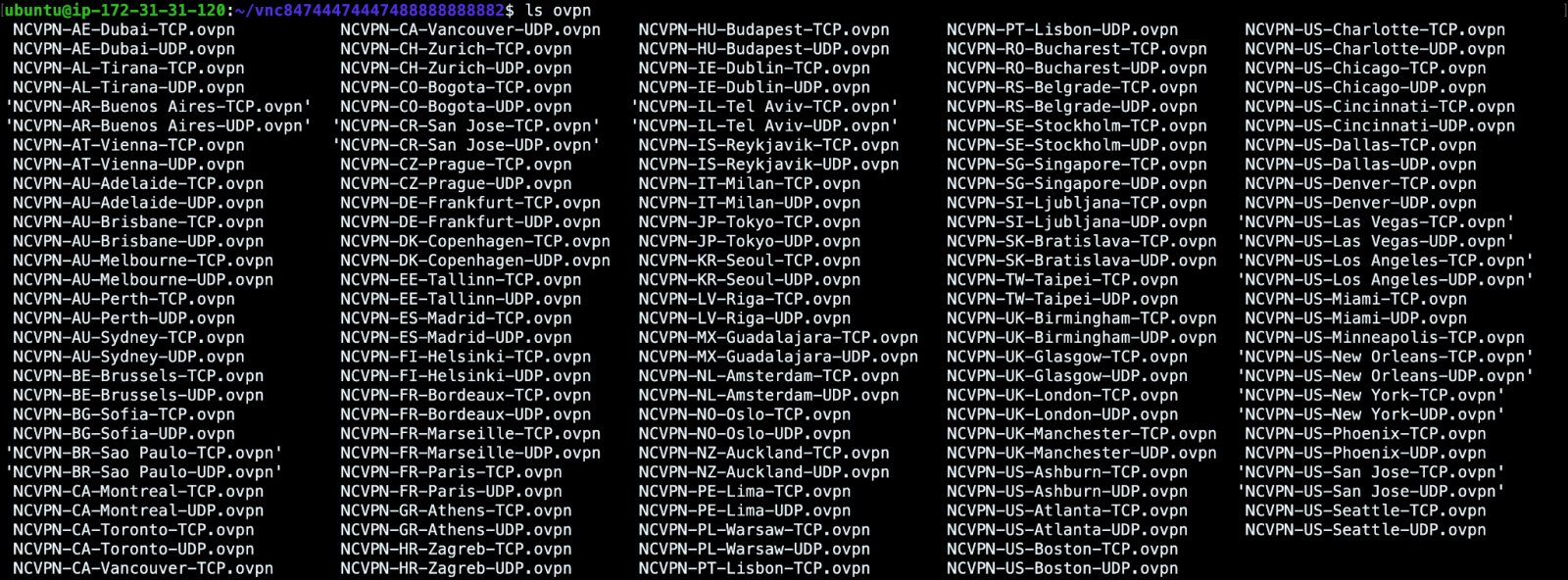
Purpleurchin uses OpenVPN and Namecheap VPN to register each account with a different IP address to evade GitHub's bot activity detection.
The GitHub actions launch over 30 instances of Docker images on each run, using pre-set arguments for the script to be executed, proxy IP and port to connect to, Stratum ID name, and max memory and CPU amounts to use.
Eventually, another script ("linuxwebapp88") will validate the configuration on the Stratum server, receive the Docker command contained in the GitHub repository, and start the miner container.
.png)
The campaign's operational diagram (Sysdig)
The miner uses a tiny part of the server's CPU power to stealthily mine a range of crypto coins such as Tidecoin, Onyx, Surgarchain, Sprint, Yenten, Arionum, MintMe, and Bitweb.
The mining process employs a custom Stratum mining protocol relay that hampers network scanners' ability to discover the outbound connections to mining pools.
This relay also obscures the threat actor's crypto wallet address, so Purpleurchin's profit remains an unanswered question for Sysdig's analysts.
Profit and damage
The cryptocurrency chosen by the threat actors to mine are marginally profitable, so Sysdig presumes the operation is either in an early experimental phase or attempting to take control of blockchains by creating a network control majority of 51%.
If the first scenario is true, the threat actor could soon switch to more profitable coins like Monero or Bitcoin.
In either case, the goal of Purpleurchin cannot be anything other than financial profit, but the ongoing freejacking operation might not be the direct channel to achieve that yet.
The damage for GitHub, however, is still significant and measurable, with Sysdig's analysts estimating it to be $15 per month per account. For Heroku and Buddy, the cost is between $7 and $10 per month per account.
Based on these calculations, it would cost the service provider over $100,000 for the threat actor to mine one Monero (XMR) via freejacking.
That's about ten times higher than the damage caused by normal cryptojacking operations, estimated to be roughly $11,000 per Monero.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.