Eleven11bot infects video recorders, with the largest concentration of them in the US.
A newly discovered network botnet comprising an estimated 30,000 webcams and video recorders—with the largest concentration in the US—has been delivering what is likely to be the biggest denial-of-service attack ever seen, a security researcher inside Nokia said.
The botnet, tracked under the name Eleven11bot, first came to light in late February when researchers inside Nokia’s Deepfield Emergency Response Team observed large numbers of geographically dispersed IP addresses delivering “hyper-volumetric attacks.” Eleven11bot has been delivering large-scale attacks ever since.
Volumetric DDoSes shut down services by consuming all available bandwidth either inside the targeted network or its connection to the Internet. This approach works differently than exhaustion DDoSes, which over-exert the computing resources of a server. Hypervolumetric attacks are volumetric DDoses that deliver staggering amounts of data, typically measured in the terabits per second.
Johnny-come-lately botnet sets a new record
At 30,000 devices, the Eleven11bot was already exceptionally large (although some botnets exceed well over 100,000 devices). Most of the IP addresses participating, Nokia researcher Jérôme Meyer told me, had never been seen engaging in DDoS attacks.
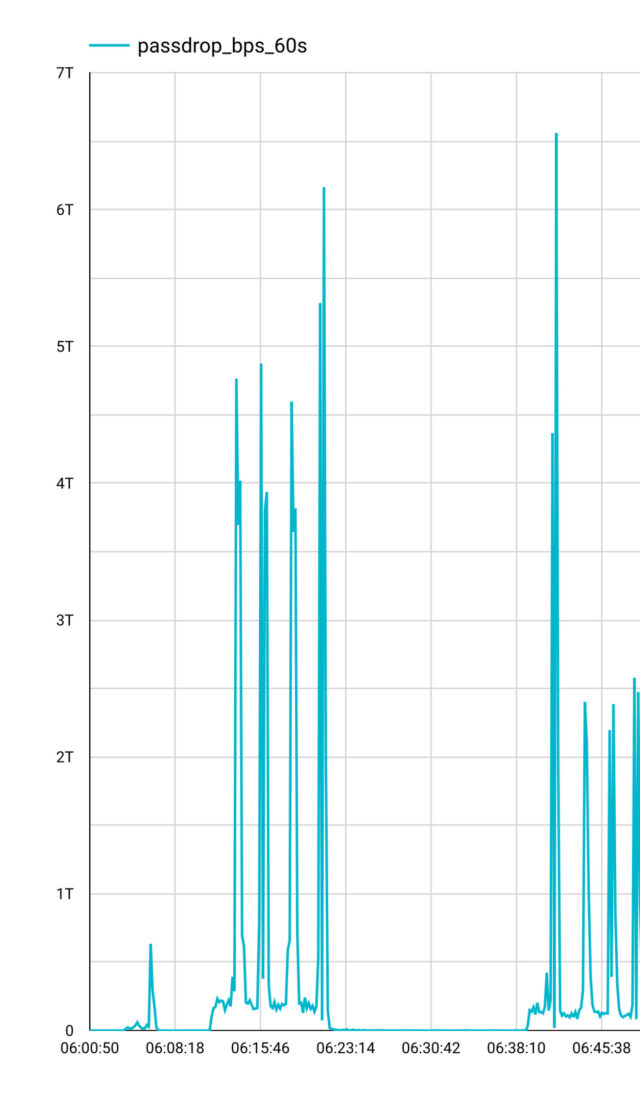
Besides a 30,000-node botnet seeming to appear overnight, another salient feature of Eleven11bot is the record-size volume of data it sends its targets. The largest one Nokia has seen from Eleven11bot so far occurred on February 27 and peaked at about 6.5 terabits per second. The previous record for a volumetric attack was reported in January at 5.6 Tbps.
"Eleven11bot has targeted diverse sectors, including communications service providers and gaming hosting infrastructure, leveraging a variety of attack vectors," Meyer wrote. While in some cases the attacks are based on the volume of data, others focus on flooding a connection with more data packets than a connection can handle, with numbers ranging from a "few hundred thousand to several hundred million packets per second." Service degradation caused in some attacks has lasted multiple days, with some remaining ongoing as of the time this post went live.
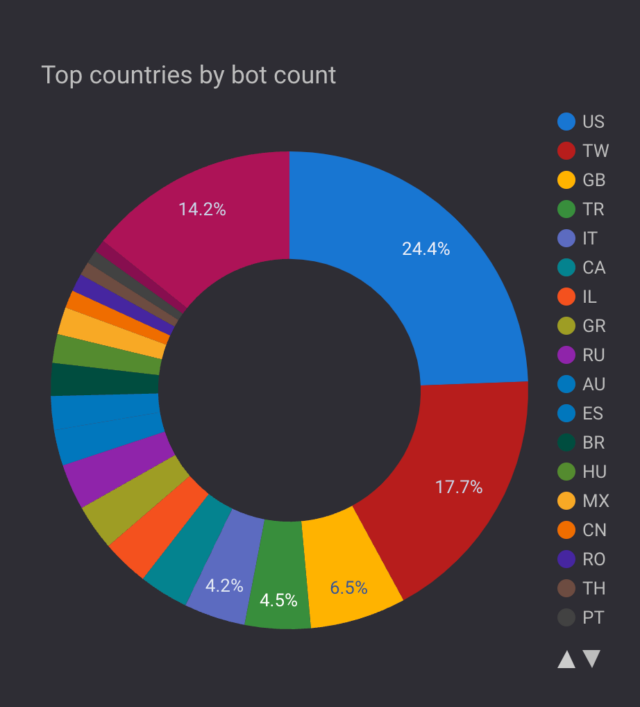
A breakdown showed that the largest concentration of IP addresses, at 24.4 percent, was located in the US. Taiwan was next at 17.7 percent, and the UK at 6.5 percent.
In an online interview, Meyer made the following points:
- This botnet is much larger than what we're used to seeing in DDoS attacks (the only precedent I have in mind is an attack from 2022 right after the Ukraine invasion, at ~60k bots, but not public).
- The vast majority of its IPs were not involved in DDoS attacks prior to last week.
- Most of the IPs are security cameras (Censys thinks Hisilicon, I saw multiple sources talk to a Hikvision NVR too so that is a possibility but not my area of expertise).
- partly because the botnet is larger than average, the attack size is also larger than average.
According to a post updated on Wednesday from security firm Greynoise, Eleven11bot is most likely a variant of Mirai, a family of malware for infecting webcams and other Internet of Things devices. Mirai debuted in 2016, when tens of thousands of IoT devices infected by it delivered what at the time were record-setting DDoSes of about 1 Tbps and took down security news site KrebsOnSecurity for almost a week. Shortly after that, Mirai developers published their source code in a move that made it easy for copycats everywhere to deliver the same massive attacks. Greynoise said that the variant driving Eleven11bot is using a single new exploit to infect TVT-NVMS 9000 digital video recorders that run on HiSilicon chips.
There have been conflicting reports on the number of devices comprising Eleven11bot. Following Nokia's report last Saturday of roughly 30,000 devices, the nonprofit Shadowserver Foundation said Tuesday that the true size was more than 86,000. Then in Wednesday's update, Greynoise said that based on data from fellow security firm Censys, both numbers were inflated and the true number was likely fewer than 5,000.
The upward revision from Shadowserver was likely the result of the belief that all infected devices displayed unique device information. That suspicion now appears to be incorrect. Instead, Meyer believes the information seen on infected devices is displayed on all such hardware, whether infected or not. Researchers from Greynoise and Censys weren't immediately available to explain how they arrived at the much lower estimate of fewer than 5,000.
Meyer said that he has consistently observed as many as 20,000 to 30,000 IP addresses participating in follow-on attacks, although many attacks come from much smaller subsets. He said that he has since sent a list of all 30,000 or so IP addresses he has observed to Censys and plans to also send them to Shadowserver soon in hopes of getting consensus on the true size.
"I am still confident on the estimated count as this is what we keep seeing in attacks and after human review of the source IPs," he wrote.
Mirai-based botnets employ various methods for infecting their targets. One common method is to attempt to log in to device administrator accounts using username/password pairs commonly set as defaults by manufacturers. Mirai botnets have also been known to exploit vulnerabilities that bypass security settings.
In any case, anyone running any sort of IoT devices should position them behind a router or other form of firewall so they're not visible from outside a local network. Remote administration from outside the Internet should be enabled only when needed. Users should also ensure each device is protected by a strong unique password. Last, devices should be updated as soon as security patches become available.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
News posts... 2023: 5,800+ | 2024: 5,700+ | 2025 (till end of February): 874
RIP Matrix | Farewell my friend ![]()
- Mutton
-

 1
1


3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.