A newly launched information-stealing malware variant called Mars Stealer is rising in popularity, and threat analysts are now spotting the first notable large-scale campaigns employing it.
Mars Stealer emerged as a redesign of the Oski malware that shut down development in 2020, featuring extensive info-stealing capabilities targeting a broad spectrum of apps.
Promoted on hacking forums at affordable prices in the range of $140-$160, Mars Stealer grew slowly until recently, when the abrupt shut down of Raccoon Stealer forced cybercriminals to seek alternatives.
Mars Stealer was overwhelmed by an influx of new users, as the service is operating similarly to how Raccoon used to run, so it’s about to become the springboard of numerous new campaigns.
Mars Stealer dev overwhelmed by new requests
Threat analysts at Morphisec report having spotted several of these new campaigns, including one using a cracked version of the malware that circulates with instructions on how to use it.
OpenOffice campaign
A new Mars Stealer campaign uncovered by Morphisec is using Google Ads advertising to rank cloned OpenOffice sites high on Canadian search results.
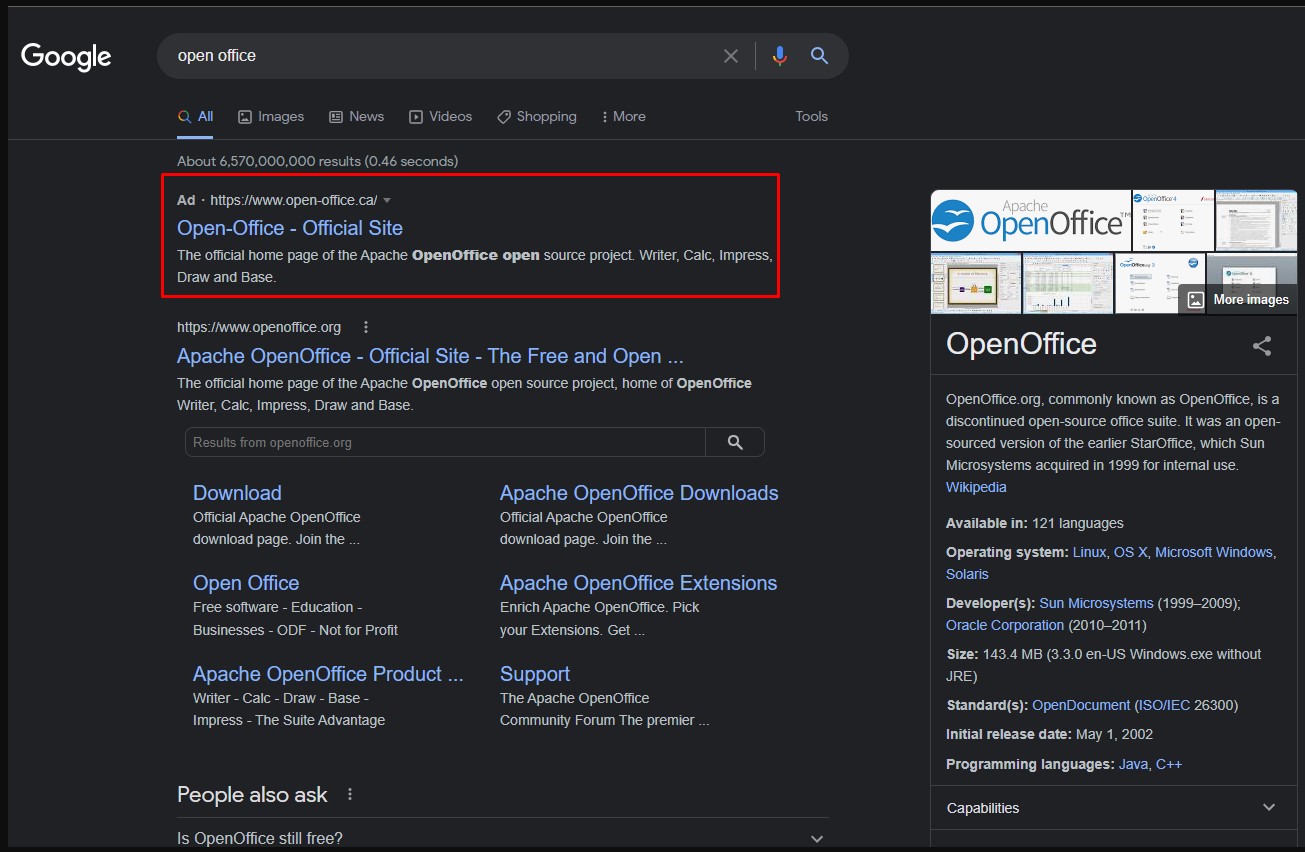
Poisoning Google Search results with malicious ads (Morphisec)
OpenOffice is a once-popular open-source office suite now belonging to the Apache foundation and has been surpassed by LibreOffice, which started as its fork back in 2010.
However, OpenOffice still enjoys a respectable number of daily downloads from people who seek a free document and spreadsheet editor. Possibly, the threat actors didn’t clone the much more popular LibreOffice because that would result in a quick take-down due to numerous reports.
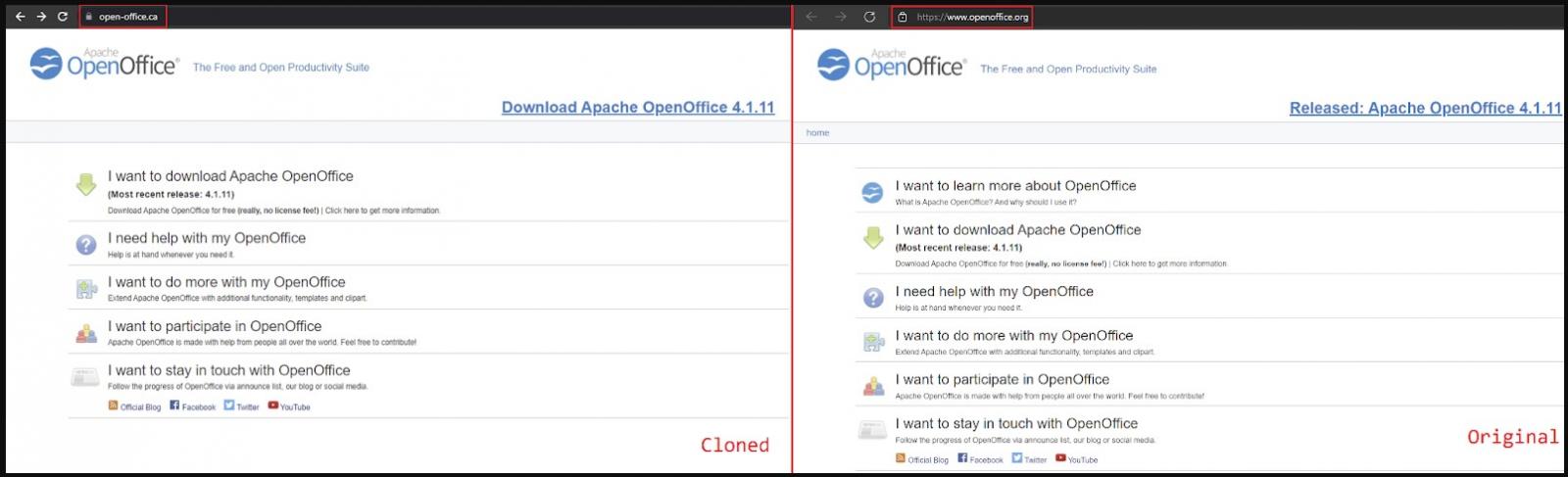
Malicious site compared to the real one (Morphisec)
The OpenOffice installer on the phony site is, in reality, a Mars Stealer executable packed with the Babadeda crypter or the Autoit loader, so the victims are unknowingly infecting themselves.
Due to an error in the configuration instructions of the cracked version, the operator has exposed the victims’ 'logs' directory, giving full access to any visitor.
A log is a zip file containing data stolen by an information-stealing Trojan and uploaded to threat actors' command and control servers.
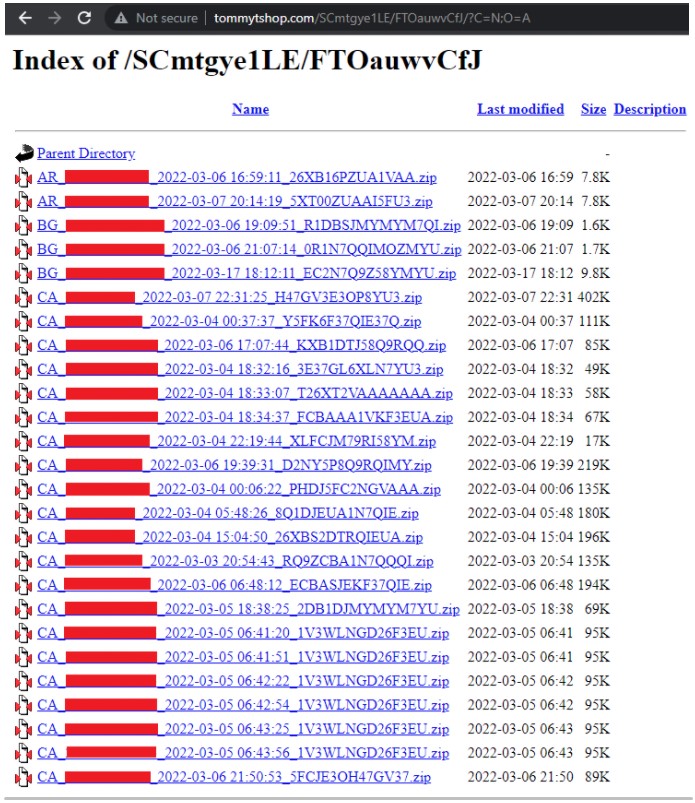
Directory storing stolen data (logs) - Morphisec
In this campaign, the stolen information produced by Mars Stealer appears to contain browser auto-fill data, browser extension data, credit cards, IP address, country code, and timezone.
Because the threat actor infected themselves with their copy of Mars Stealer during debugging, their sensitive information was also exposed.
This mistake allowed the researchers to attribute the attacks to a Russian speaker and discover the threat actor's GitLab accounts, stolen credentials used to pay for the Google Ads, and more.
A threat to crypto assets
Mars Stealer is a rising threat, promoted in over 47 darknet sites and hacking forums, Telegram channels, and “unofficial” distribution pathways like the cracked pack.
Morphisec says that the operators of these info-stealers are heavily focused on cryptocurrency assets.
Overview of stolen logs from a single campaign operator (Morphisec)
The most stolen browser plugin from the analyzed campaign is MetaMask, followed by Coinbase Wallet, Binance Wallet, and Math wallet, all “hot” wallets for managing cryptocurrency assets.
Morphisec also identified credentials belonging to a healthcare infrastructure provider in Canada and saw signs of compromise on several high-profile Canadian service firms.
To protect against info-stealers, ensure that you click on official sites and not Google Ad results and always scan downloaded executables on your AV before launching.
For those looking for a deep technical nose-dive into the new Mars Stealer malware, you can read 3xp0rt's analysis of the new malware variant.
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.