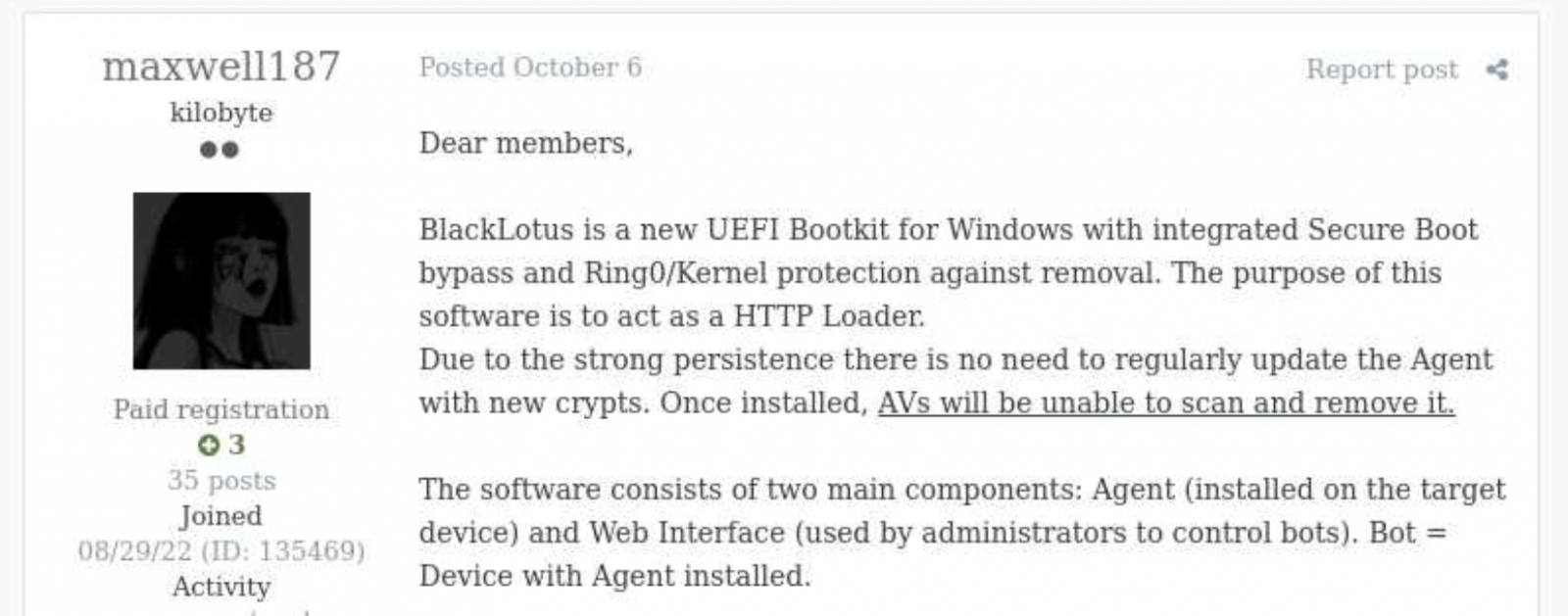
A threat actor is selling on hacking forums what they claim to be a new UEFI bootkit named BlackLotus, a malicious tool with capabilities usually linked to state-backed threat groups.
UEFI bootkits are planted in the system firmware and are invisible to security software running within the operating system because the malware loads in the initial stage of the booting sequence.
While cybercriminals who want a license for this Windows bootkit have to pay $5,000, the threat actor says rebuilds would only set them back $200.
The seller says BlackLotus features integrated Secure Boot bypass, has built-in Ring0/Kernel protection against removal, and will start in recovery or safe mode.
BlackLotus claims to come with anti-virtual machine (anti-VM), anti-debug, and code obfuscation features to block malware analysis attempts. The seller also claims that security software cannot detect and kill the bootkit as it runs under the SYSTEM account within a legitimate process.
Even more, this tiny bootkit with a size of only 80 kb on disk after installation can disable built-in Windows security protection such as Hypervisor-Protected Code Integrity (HVCI) and Windows Defender and bypass User Account Control (UAC).
"The software itself and the Secure Boot bypass work vendor independent. A vulnerable signed bootloader is used to load the bootkit if Secure Boot is used," the threat actor explained when a potential "customer" asked if it would work with a particular firmware.
"Patching this vulnerability by adding it to the UEFI revocation list is currently impossible, as the vulnerability affects hundreds of bootloaders that are still used today."
APT-level malware now more widely available
Kaspersky lead security researcher Sergey Lozhkin also spotted BlackLotus being advertised on criminal forums and warned that this is a significant move since this type of capability has commonly been available only to state-sponsored hacking groups.
"These threats and technologies before were only accessible by guys who were developing advanced persistent threats, mostly governments. Now these kinds of tools are in the hands of criminals all over the forums," Kaspersky lead security researcher Sergey Lozhkin said last week.
Other security analysts tagged BlackLotus' wide availability for any cybercriminal with deep enough pockets as a leap toward wider availability of APT-level capabilities in off-the-shelf malware.
"I've reviewed its features and capabilities and right off the bat, these are the salient points that every blue team and red team alike should be full aware of," Eclypsium's Scott Scheferman also warned.
"Considering this tradecraft used to be relegated to APTs like the Russian GRU and APT 41 (China nexus), and considering prior criminal discoveries we've made (e.g. Trickbot's Trickboot module), this represents a bit of a 'leap' forward, in terms of ease of use, scalability, accessibility and most importantly, the potential for much more impact in the forms of persistence, evasion and/or destruction."
However, Scheferman said that until a sample is found, there is no way to determine if the feature-set is complete or if it is even production ready.
"It should be noted, too, that until we or someone obtains a sample of this malware and runs it on a close-to-production box in a lab, there is always the chance it isn't ready for show time yet, or certain aspects of its features aren't working right, or even the chance the entire thing is a scam," he added.
If confirmed, this would be a worrying trend seeing that BlackLotus can also be used to load unsigned drivers that could be used in Bring Your Own Driver (BYOVD) attacks.
In recent weeks, such attacks have been linked to a wide range of threat actors, including state-backed hacker groups, ransomware gangs, and unknown attackers.
- aum and Karlston
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.