A new Google Search malvertizing campaign targets users looking to download the popular Notepad++ text editor, employing advanced techniques to evade detection and analysis.
Threat actors have been increasingly abusing Google Ads in malvertising campaigns to promote fake software websites that distribute malware.
According to Malwarebytes, which spotted the Notepad++ malvertising campaign, it has been live for several months but managed to fly under the radar all this time.
The final payload delivered to victims is unknown, but Malwarebytes says it's most likely Cobalt Strike, which usually precedes highly damaging ransomware deployments.
Abusing Google ads
The Notepad++ malvertizing campaign promotes URLs that are obviously unrelated to the software project yet use misleading titles displayed in Google Search result advertisements.
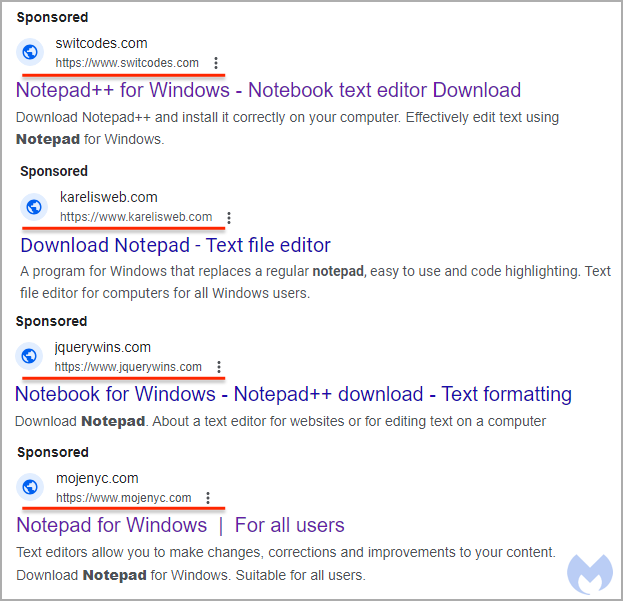
This SEO strategy is heavily abused in this case, and since titles are far larger and more visible than URLs, many people are likely to fall for the trap.
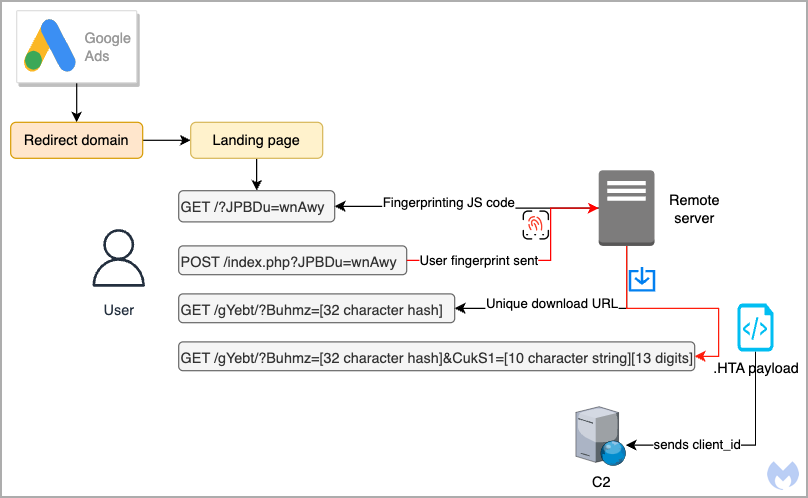
Once victims click on any of the ads, a redirection step checks their IP to filter out users likely to be crawlers, VPNs, bots, etc., leading them to a decoy site that does not drop anything malicious.
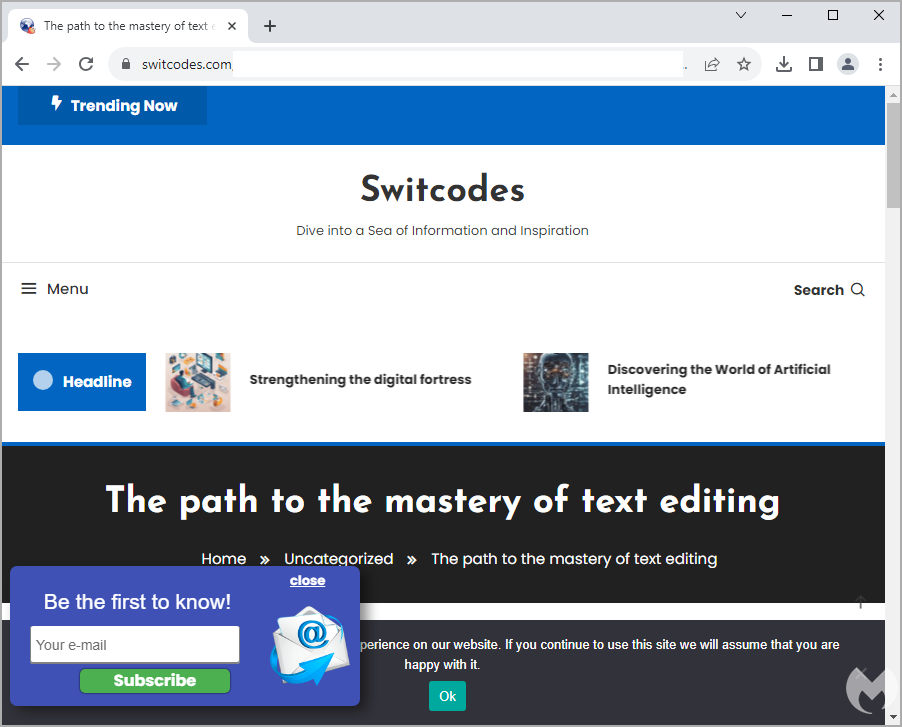
In contrast, legitimate targets are redirected to "notepadxtreme[.]com" which mimics the real Notepad++ site, featuring download links for various versions of the text editor.
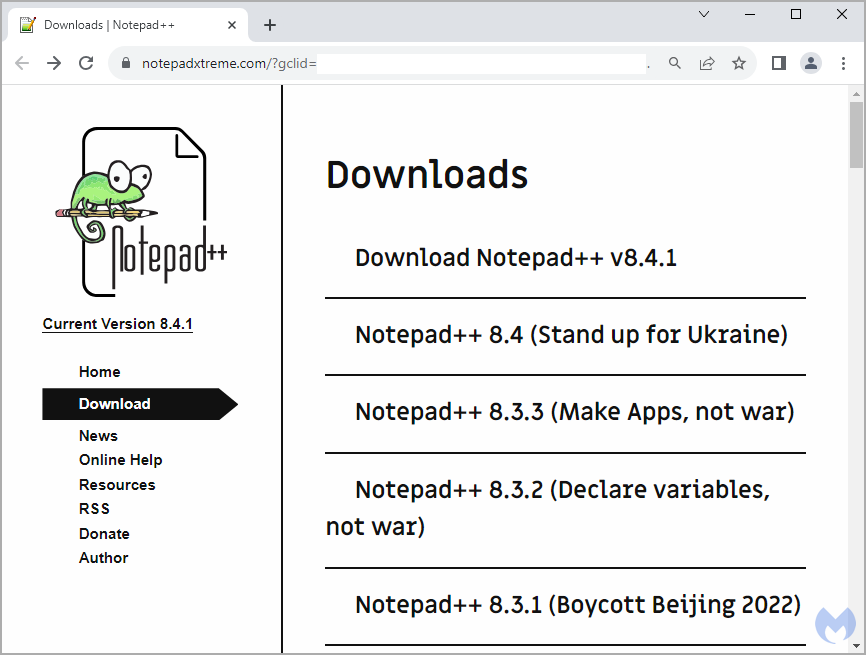
When visitors click on those links, a second system fingerprint check is performed by a JavaScript snippet to validate that there are no anomalies or indications that the visitor is using a sandbox.
Victims who are marked as suitable targets are then served an HTA script, which is assigned a unique ID, likely to enable the attackers to track their infections. That payload is served only once per victim, so a second visit results in a 404 error.
Malwarebytes' examination of the HTA didn't produce any useful information due to it not being weaponized at the time, but the analysts found the same file in a VirusTotal upload from July.
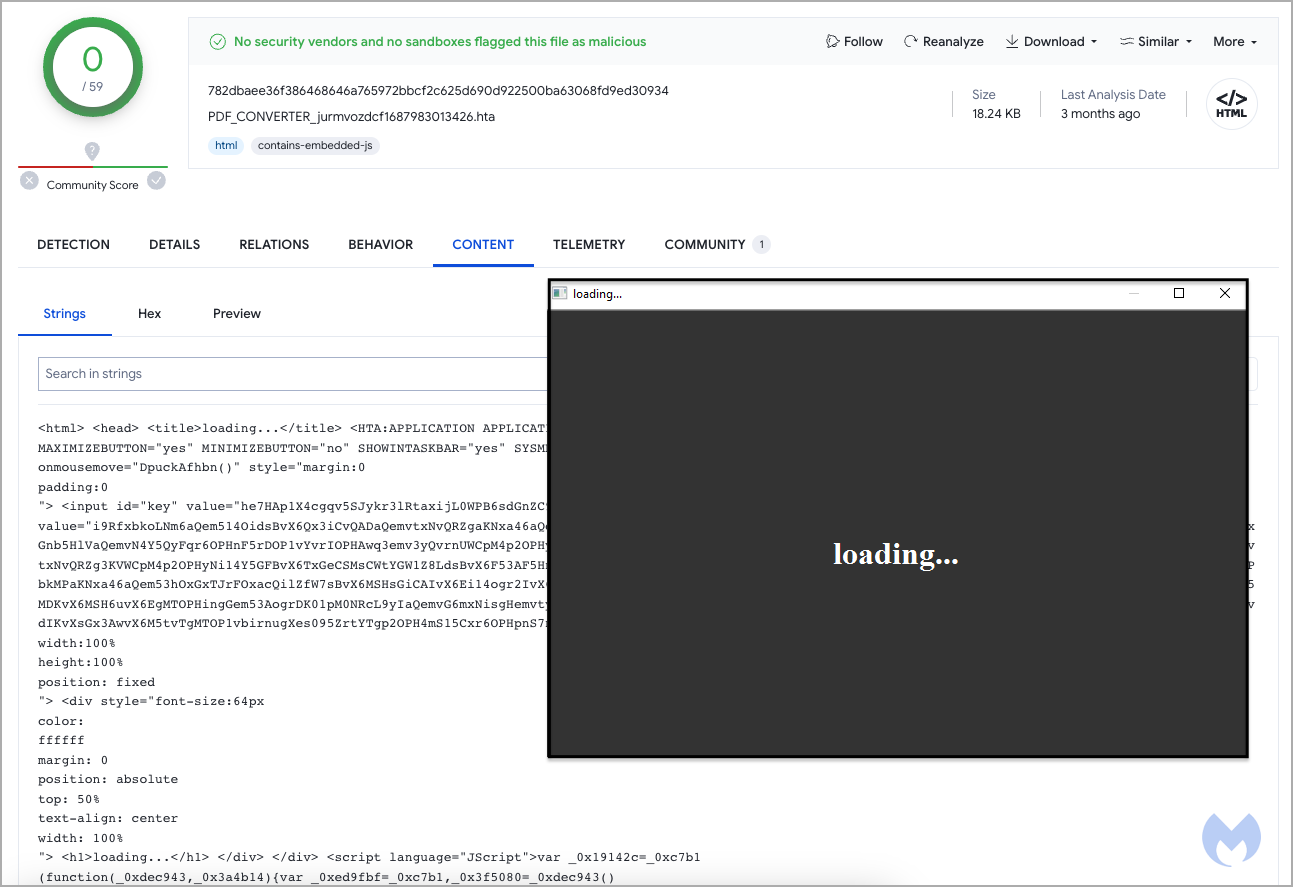
That file attempted to connect to a remote domain on a custom port, with the researchers believing it was likely part of a Cobalt Strike deployment.
To avoid downloading malware when looking for specific software tools, skip promoted results on Google Search and double-check that you have landed on the official domain.
If unsure about the project's real website, check its "About" page, documentation, Wikipedia page, and official social media channels.



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.