A set of four malicious applications currently available in Google Play, the official store for the Android system, are directing users sites that steal sensitive information or generate ‘pay-per-click’ revenue for the operators.
Some of these sites offer victims to download fake security tools or updates, to trick users into installing the malicious files manually.
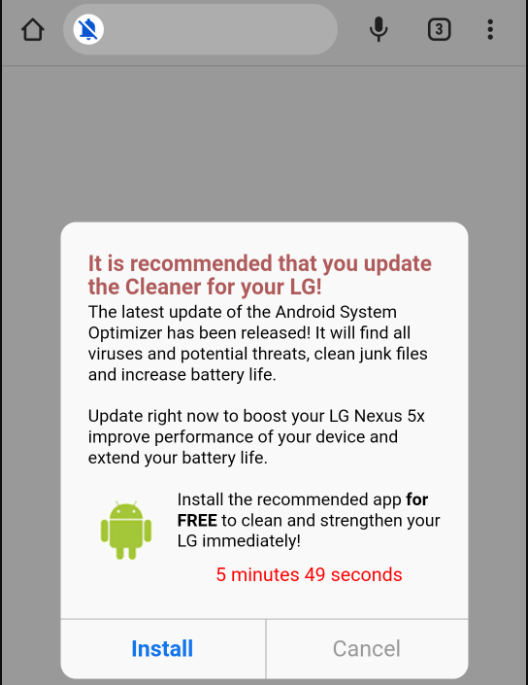
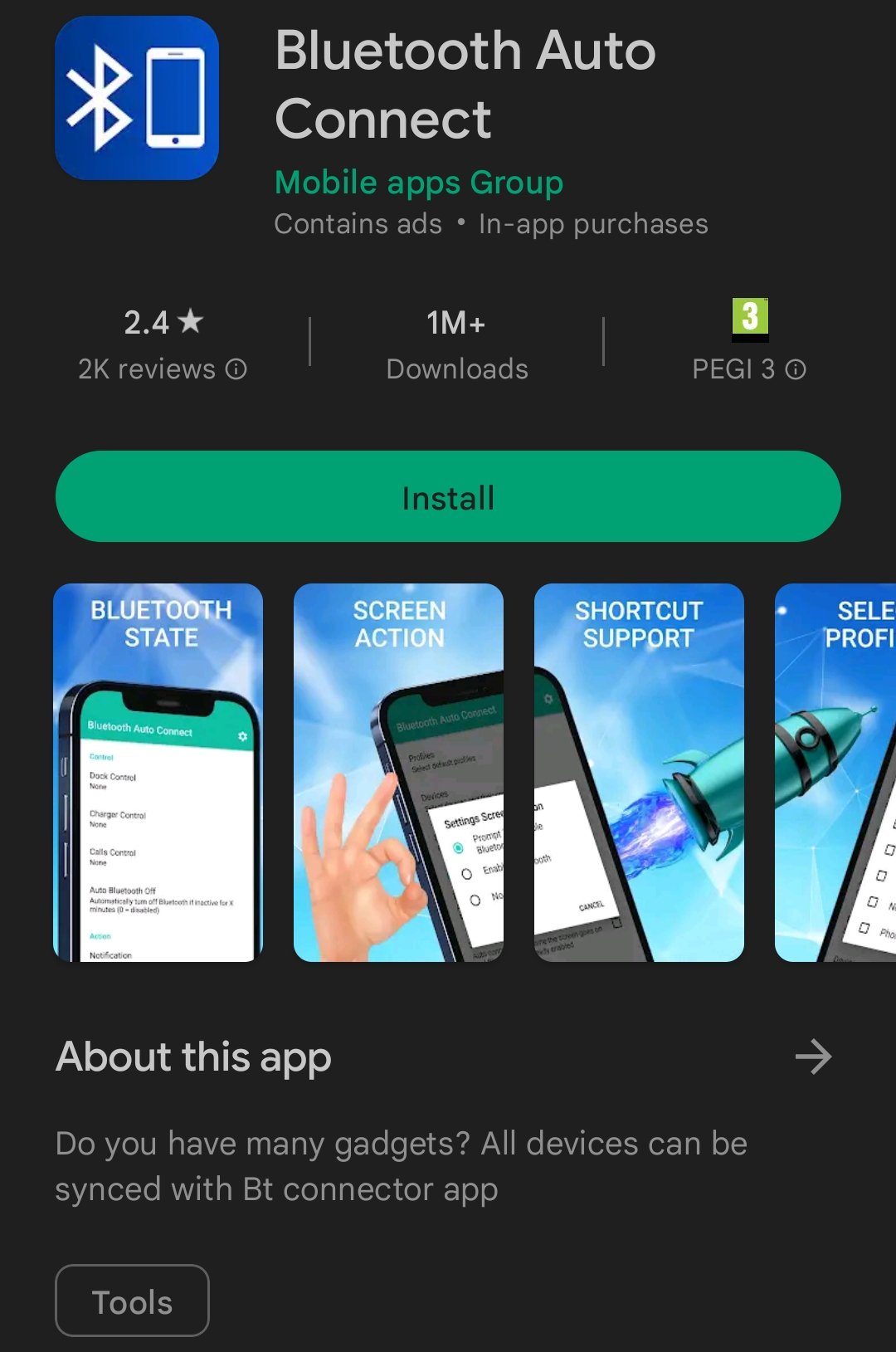
At the time of publishing, the apps are still present on Google Play under a developer account called Mobile apps Group, and have a total install count of more than one million.
According to a report from Malwarebytes, the same developer was exposed twice in the past for distributing adware on Google Play but it was allowed to continue publishing apps after submitting cleaned versions.
The four malicious apps uncovered this time are:
- Bluetooth Auto Connect, with over 1,000,000 installs
- Bluetooth App Sender, with over 50,000 installs
- Driver: Bluetooth, Wi-Fi, USB, with over 10,000 installs
- Mobile transfer: smart switch, with over 1,000 installs
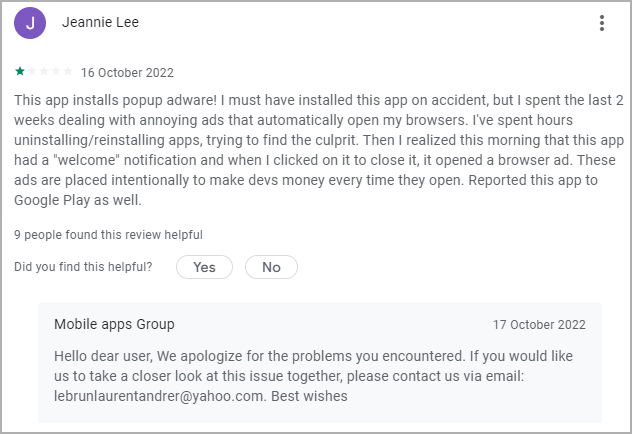
The apps don’t have favorable reviews on Google Play and many users left comments about intrusive ads that open automatically in new browser tabs.
Interestingly, the developer responds to some of these comments, offering to help resolve the ad problems.
BleepingComputer has contacted ‘Mobile apps Group’ to request a comment about the Malwarebytes researchers' findings but we have not heard back yet.
72 hours of delay
By monitoring the activity of the software from Mobile apps Group, Malwarebytes found that the apps have a 72-hour delay before showing the first ad or opening a phishing link in the web browser, and then continue to launch more tabs with similar content every two hours.
The researchers note that new browser tabs are opened even when the device is locked, so when users return to their phones after a while, they find multiple phishing and ad sites opened.
Analysis of the Manifest file revealed that the developer tried to obfuscate logs for the actions performed by using nonsense log descriptor such as "sdfsdf."
While this method works against automated code scanners, it helped the researchers spot the actions easier.
To keep adware away from your device, avoid installing apps from unofficial Android stores. Reading user reviews, monitoring battery usage, and network data activity, also helps determine if the device is running suspicious software. Keeping Google's Play Protect feature active is also a good way to keep the device safer.
If you have one of the above apps present on your Android device, it is recommended to remove them and run a full system scan using Play Protect or a mobile antivirus suite from a reputable vendor.
BleepingComputer has also contacted Google for a comment about the developer's history and their current apps, and we will update this story as soon as we hear back.




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.