Magecart Hackers Hide Stolen Credit Card Data Into Images for Evasive Exfiltration
Cybercrime actors part of the Magecart group have latched on to a new technique of obfuscating the malware code within comment blocks and encoding stolen credit card data into images and other files hosted on the server, once again demonstrating how the attackers are continuously improving their infection chains to escape detection.
"One tactic that some Magecart actors employ is the dumping of swiped credit card details into image files on the server [to] avoid raising suspicion," Sucuri Security Analyst, Ben Martin, said in a write-up. "These can later be downloaded using a simple GET request at a later date."
MageCart is the umbrella term given to multiple groups of cybercriminals targeting e-commerce websites with the goal of plundering credit card numbers by injecting malicious JavaScript skimmers and selling them on the black market.
Sucuri attributed the attack to Magecart Group 7 based on overlaps in the tactics, techniques, and procedures (TTPs) adopted by the threat actor.
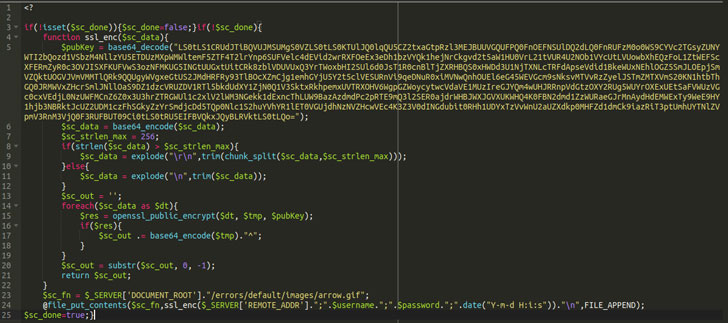
In one instance of a Magento e-commerce website infection investigated by the GoDaddy-owned security company, it was found that the skimmer was inserted in one of the PHP files involved in the checkout process in the form of a Base64-encoded compressed string.
What's more, to further mask the presence of malicious code in the PHP file, the adversaries are said to have used a technique called concatenation wherein the code was combined with additional comment chunks that "does not functionally do anything but it adds a layer of obfuscation making it somewhat more difficult to detect."
Ultimately, the goal of the attacks is to capture customers' payment card details in real-time on the compromised website, which are then saved to a bogus style sheet file (.CSS) on the server and downloaded subsequently at the threat actor's end by making a GET request.
"MageCart is an ever growing threat to e-commerce websites," Martin said. "From the perspective of the attackers: the rewards are too large and consequences non-existent, why wouldn't they? Literal fortunes are made [by] stealing and selling stolen credit cards on the black market."
- Karlston
-

 1
1



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.