A LockBit 3.0 ransomware affiliate is using phishing emails that install the Amadey Bot to take control of a device and encrypt devices.
According to a new AhnLab report, the threat actor targets companies using phishing emails with lures pretending to be job application offers or copyright infringement notices.
The LockBit 3.0 payload used in this attack is downloaded as an obfuscated PowerShell script or executable form, running on the host to encrypt files.
Amadey Bot activity
The Amadey Bot malware is an old strain capable of performing system reconnaissance, data exfiltration, and payload loading.
Korean researchers at AhnLab have noticed increased Amadey Bot activity in 2022 and reported finding a new version of the malware in July, dropped via SmokeLoader.
The latest version added antivirus detection and auto-avoidance capabilities, making intrusions and dropping payloads stealthier.
In the July campaign, Amadey dropped various information-stealing malware, such as RedLine, but the more recent campaign loads a LockBit 3.0 payload instead.
Infection chains
AhnLab researchers noticed two distinct distribution chains, one relying on a VBA macro inside a Word document and one disguising the malicious executable as a Word file.
In the first case, the user has to click on the "Enable Content" button to execute the macro, which creates an LNK file and stores it to "C:\Users\Public\skem.lnk". This file is a downloader for Amadey.
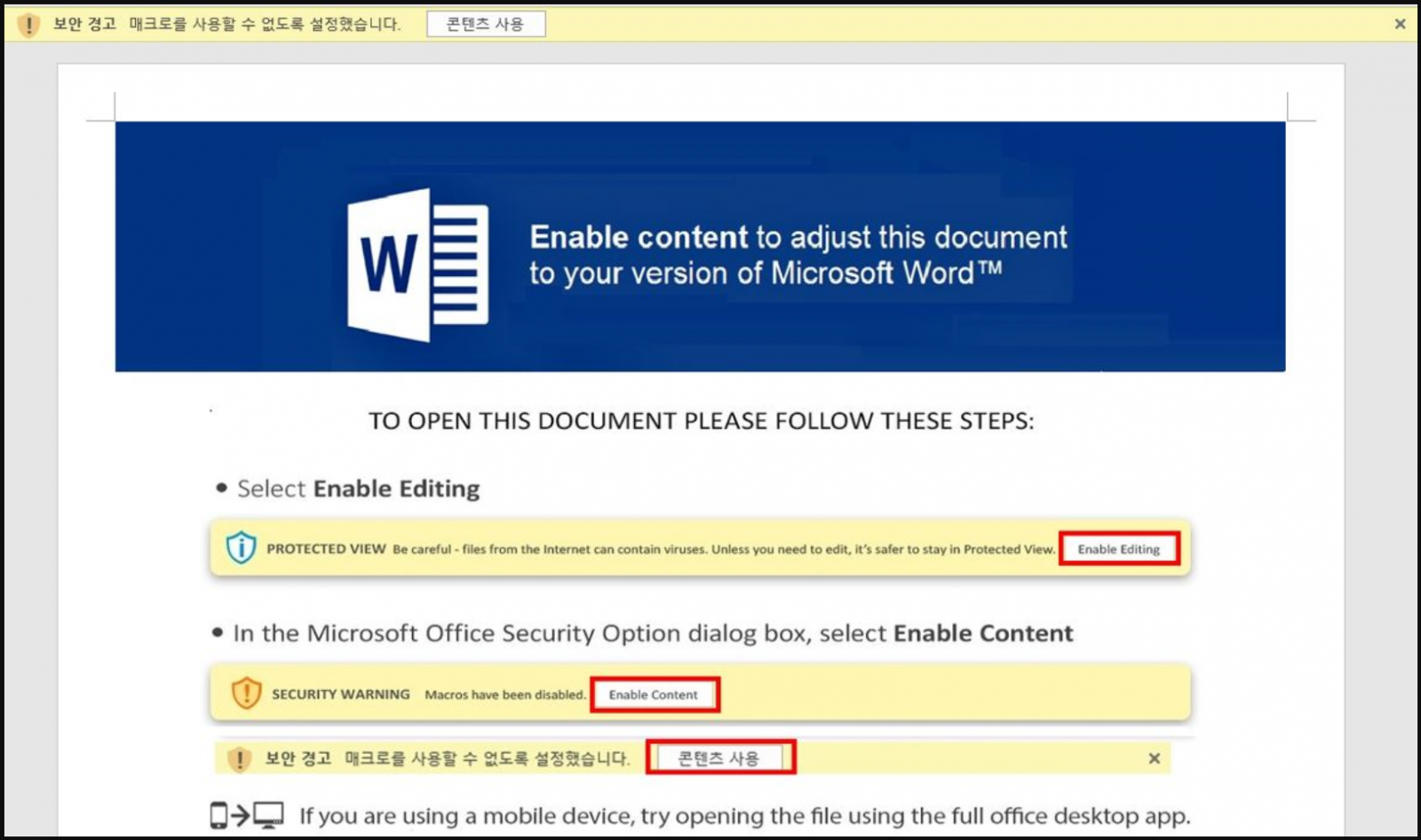
Malicious document initiating the infection chain (AhnLab)
The second case, seen in late October, uses email attachments with a file named "Resume.exe" (Amadey) that uses a Word document icon, tricking recipients into double-clicking.
Both distribution paths lead to Amadey infections that use the same command and control (C2) address, so it's safe to assume the operator is the same.
Amadey to LockBit 3.0
At first launch, the malware copies itself to the TEMP directory and creates a scheduled task to establish persistence between system reboots.
Next, Amadey connects to the C2, sends a host profiling report, and then waits for the reception of commands.
The three possible commands from the C2 server order the download and execution of LockBit, in PowerShell form ('cc.ps1' or 'dd.ps1'), or exe form ('LBB.exe').
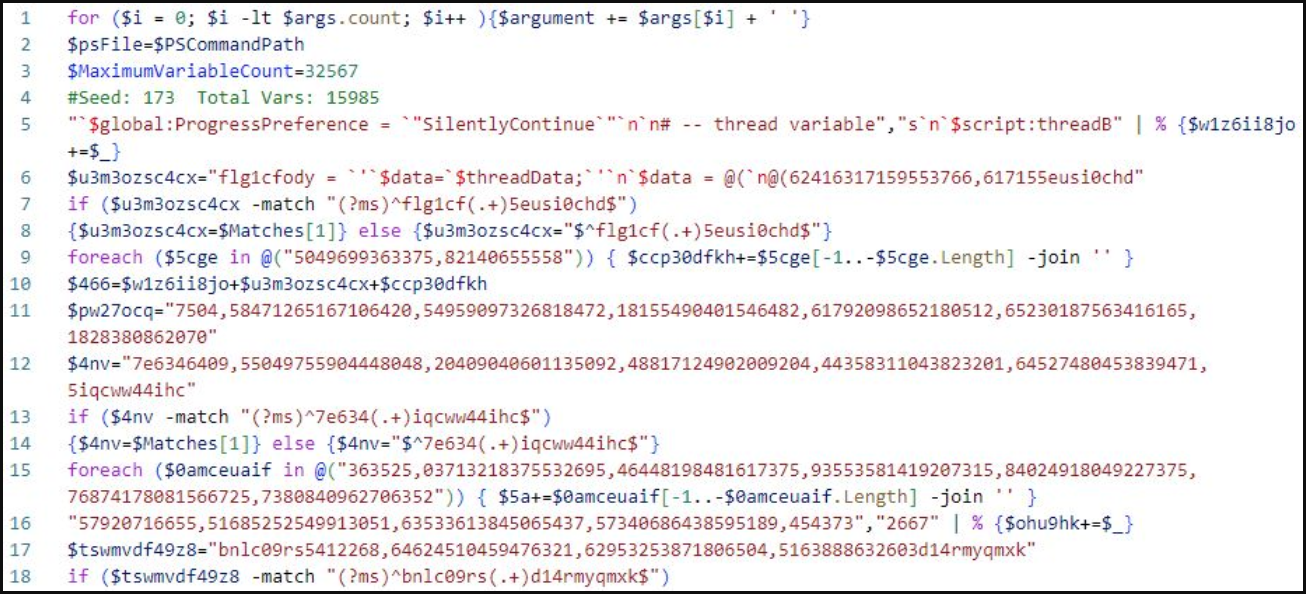
Obfuscated PowerShell version of LockBit (AhnLab)
The payloads are again dropped in TEMP as one of the following three:
- %TEMP%\1000018041\dd.ps1
- %TEMP%\1000019041\cc.ps1
- %TEMP%\1000020001\LBB.exe
From there, LockBit encrypts the user's files and generates ransom notes demanding payment, threatening to publish stolen files on the group's extortion site.
.png)
Sample of the generated ransom notes (AhnLab)
In September 2022, AnhLab observed another two methods of LockBit 3.0 distribution, one using DOTM documents with malicious VBA macro and one dropping ZIP files containing the malware in NSIS format.
Earlier, in June 2022, LockBit 2.0 was seen distributed via fake copyright infringement emails dropping NSIS installers, so it all appears to be the evolution of the same campaign.




Recommended Comments
There are no comments to display.