Security researchers are warning that LinkedIn has become the most spoofed brand in phishing attacks, accounting for more than 52% of all such incidents at a global level.
The data comes cybersecurity company Check Point, who recorded a dramatic uptick in LinkedIn brand abuse in phishing incidents in the first quarter of this year.
According to the company, in the last quarter of 2021, LinkedIn held the fifth spot on the list, the count for impersonating attacks being a much lower 8%.
The second most mimicked brand is German package delivery DHL, which previously was at the top of the list. A contributing factor for this was the increased shopping during the holiday season.
.png)
Combining DHL with FedEx, Maersk, and Ali Express, shipping-related phishing messages accounted for 21.8% in the first three months of 2022, still holding a significant portion.
In a LinkedIn impersonation sample that Check Point provided, the phishing email reaching the target’s inbox features LinkedIn logos and company-specific style, with a fraudulent request to connect with a made-up firm.
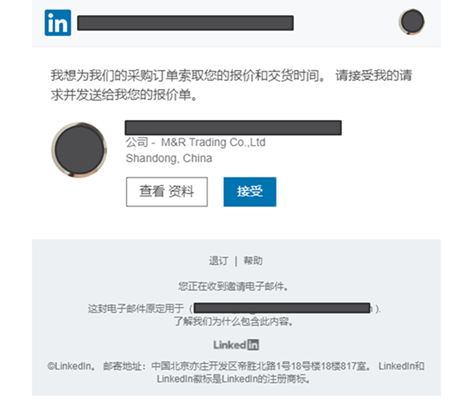
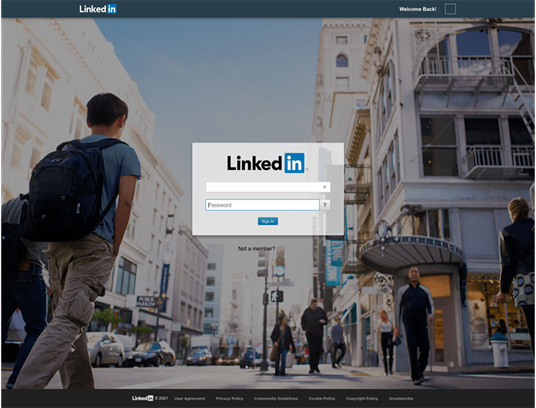
Clicking on the “Accept” button takes the victim to a phishing website that looks like an actual LinkedIn login page hosted on at an unofficial URL - carriermasr.com/public/linkedin.com/linkedin.com/login.php
data:image/gif;base64,R0lGODlhAQABAAAAACH5BAEKAAEALAAAAAABAAEAAAICTAEAOw==
Why is this happening?
Social media phishing is on the rise, as also reported Vade cybersecurity company recently. This is because the takeover of accounts on these platforms opens up a host of practical possibilities for the threat actors.
For example, the hackers may use compromised social media accounts to perform highly effective spear-phishing attacks, post links to malware-hosting sites, or send spyware directly to users who trust them.
In the case of LinkedIn, which is a professional-focused social media platform, the threat actors are likely aiming to perform spear-phishing attacks on high-interest targets, employees of specific companies and organizations.
Another potential exploitation scenario would be sending laced documents masqueraded as job offers to specific targets, convincing them to open the files and activate malicious macro code.
For example, North Korean hackers have launched multiple spear-phishing campaigns in the past that leveraged LinkedIn, which proved to be very effective.
However, the scale recorded by Check Point this time indicates that LinkedIn impersonation is no longer limited to advanced, narrow targeting threat groups like Lazarus.
LinkedIn brand takes lead as most impersonated in phishing attacks
- aum
-

 1
1



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.