Security analysts have discovered two API security vulnerabilities in BrickLink.com, LEGO Group’s official second-hand and vintage marketplace for LEGO bricks.
BrickLink is the world’s largest online community of LEGO fans, with over a million registered members.
BrickLink homepage (BleepingComputer)
Two API security issues discovered by Salt Security could have allowed an attacker to take over members' accounts, access and steal personally identifiable information (PII) stored on the platform, or even gain access to internal production data and compromise internal servers.
API flaw details
Salt Security’s analysts discovered the vulnerabilities while experimenting with user input fields on the BrickLink website.
The first one is a cross-site scripting (XSS) flaw in the “Find Username” dialog box of the coupon search section, which allowed an attacker to inject and execute code on the target’s machine using a specially crafted link.
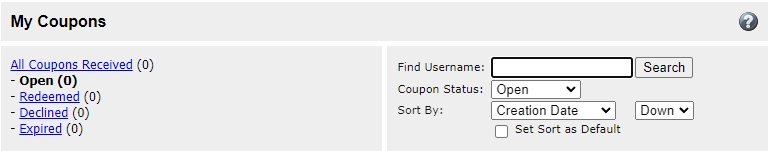
The vulnerable field on the site (BleepingComputer)
Using the target’s Session ID exposed on a different page, an attacker could leverage the XSS flaw to hijack the session and take over the target’s account.
Accessing the account means exposing all data stored on the platform, including personal details, email address, shipping address, order history, coupons, received feedback, wanted items, and message history.
The second flaw was located on the “Upload to Wanted List” page, where users can upload XML lists containing LEGO parts they wish to find and purchase.
By exploiting a flaw in endpoint parsing mechanism, Salt Security’s analysts launched a successful XML External Entity (XXE) injection attack, adding a reference to an external entity on their file.
The XXE attack enabled them to read files on the web server and execute a server-side request forgery (SSRF) attack, which could lead to exfiltrating the AWS EC2 tokens for the server.
The security researchers reported the discovered vulnerabilities to LEGO, and the company took action to fix all issues.
Cyberattacks are growing during shopping seasons and the retail sector is a more attractive target as the focus is on the commercial aspect of the business and less on improving security.
Shoppers are advised to use strong account credentials and enable two-factor authentication where available. When placing orders, a good recommendation is to use guest accounts or virtual/temporary payment cards, if that is possible.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.