The notorious North Korean hacking group known as Lazarus has been linked to the recent Atomic Wallet hack, resulting in the theft of over $35 million in crypto.
This attribution is from the blockchain experts at Elliptic, who have been tracking the stolen funds and their movements across wallets, mixers, and other laundering pathways.
The attack on Atomic Wallet occurred last weekend when numerous users reported that their wallets were compromised and their funds had been stolen.
While the investigation into the incident was underway, crypto-analyst ZachXBT calculated the losses to be over $35 million, with the largest single victim losing almost 10% of the stolen total.
Yesterday, Elliptic reported that its analysis points to Lazarus Group as the threat actors responsible for the attack, making this the hackers'hackers' first major crypto heist for 2023.
Last year, the FBI attributed to Lazarus the Harmony Horizon Bridge hack in June 2022, which resulted in the theft of $100 million, and also the March 2022 hack of Axie Infinity, from which the North Koreans siphoned $620 million in crypto.
The latest attack on Atomic Wallet shows that the threat actors remain laser-focused on monetary goals, which experts have said are directly used to fund North Korea's weapons development program.
"At Elliptic, we have identified a large number of victim wallets, allowing the stolen funds to be traced in our software," reads Elliptic'sElliptic's report.
"Our analysis of the thief's transactions leads us to attribute this hack to North Korea'sKorea's Lazarus Group, with a high level of confidence."
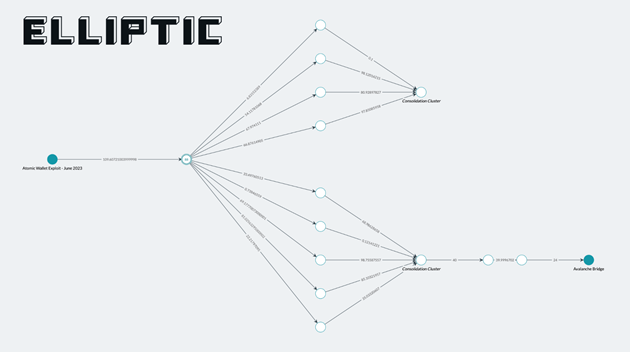
Elliptic's transaction tracing
Tracing the transactions
The first evidence pointing to the Lazarus group is the observed laundering strategy, which matches patterns seen in previous attacks by the particular threat actor.
The second attribution element is using the Sinbad mixer for laundering the stolen funds, which the threat group also used in the Harmony Horizon Bridge hack.
Elliptic has previously said that North Korean hackers have passed tens of millions of USD through Sinbad, demonstrating confidence and trust in the new mixer.
The third and most significant proof of Lazarus' involvement in the Atomic Wallet hack is that substantial portions of the stolen cryptocurrency ended up in wallets that hold the proceeds of previous Lazarus hacks and are assumed to belong to group members.
As last year's attacks have shown, successfully stealing cryptocurrency only accomplishes half the objective.
The rise of blockchain monitoring firms, coupled with the enhanced capabilities of law enforcement agencies, has significantly complicated the laundering process and subsequently cashing out the stolen assets.
As victims notify exchanges of wallet addresses containing stolen funds, preventing them from being exchanged for other crypto or fiat, it causes the hackers to turn to less scrupulous exchanges that take a hefty commission to launder the money.
Lazarus hackers linked to the $35 million Atomic Wallet heist



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.